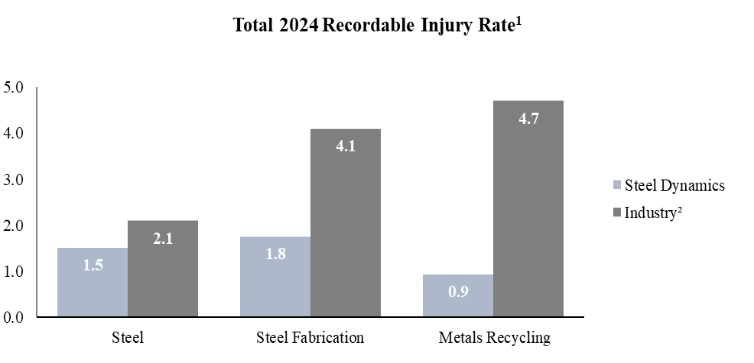
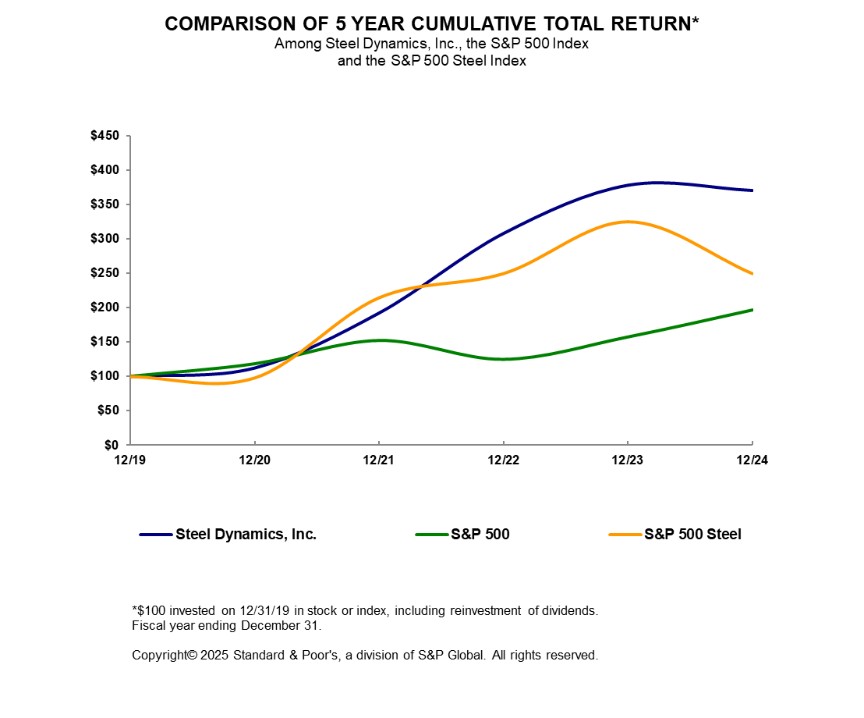
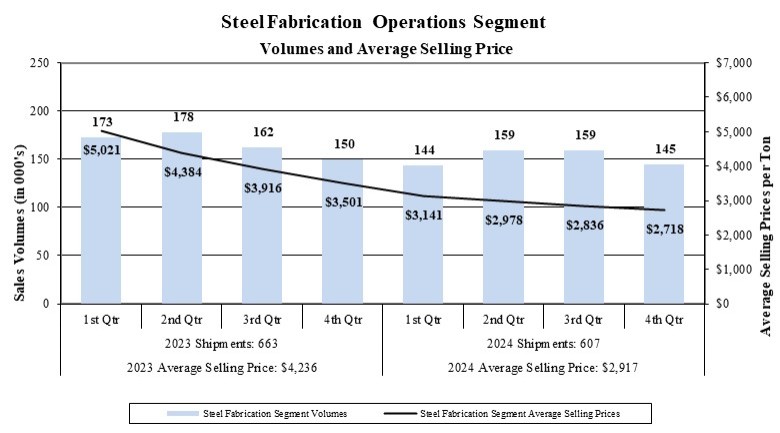
ITEM 1C. CYBERSECURITY
We manage risks from cybersecurity threats through our overall companywide risk management process, which is overseen by our Board of Directors and specific Board Committees. Management has created a global information security program, which encompasses a dedicated global information security team and policies, procedures, and processes for assessing, identifying, and managing risks from cybersecurity threats. Our policies, procedures, and processes follow recognized frameworks established by the National Institute of Standards and Technology (“NIST”), as well as other relevant standards. Our program is designed to maintain the confidentiality, integrity, security, and availability of the data that is created, collected, stored, and used to operate our business.
Risk Management and Strategy
We recognize the importance of assessing, identifying, and managing material risks associated with cybersecurity threats, utilizing, from time to time, tabletop exercises, business unit assessments, threat modeling, impact analyses, internal audits, external audits, third party vulnerability scans, third party penetration tests, and engagement of third parties to conduct analysis of our information security programs, including an overall assessment utilizing the NIST standards. These risks include, among other things: operational risks, intellectual property theft, fraud, extortion, harm to team members or customers, and violations of data privacy or security laws.
Our Director of Information Security is responsible for leading the Information Security Team which has established a cybersecurity risk management program of policies and processes for assessing, identifying, and managing risk from cybersecurity threats. We have integrated these processes into our overall risk management systems and processes, and routinely assess risks from cybersecurity threats, including any potential unauthorized access to or activity conducted through our information systems that may result in material adverse effects on the confidentiality, integrity, or availability of our information systems or any information residing therein. This program includes established reasonable safeguards to minimize the identified risks; processes to reasonably address any identified gaps in existing safeguards; updates to existing safeguards as necessary; and monitoring the effectiveness of those safeguards.
Our safeguards include continuous network monitoring, complex passwords, team member training that reinforces our policies, standards, and practices, incident response capability reviews and exercises, and cybersecurity insurance and disaster recovery plans for the protection of our assets. The information security training and awareness program engages personnel through training modules on how to identify potential cybersecurity risks and protect the Company’s resources and information. This training is mandatory for all team members monthly, and is supplemented by companywide testing initiatives, including periodic phishing tests.
Our cybersecurity risk management program also assesses third party providers, such as vendors, suppliers, and other business partners. Cybersecurity risks are evaluated when determining the selection and oversight of applicable third party providers and potential risks when handling or processing our employee, business, or customer data.
Further, we have designated a member of our senior leadership team, our Chief Financial Officer, to oversee the management of the safeguards, cybersecurity risk assessment, and mitigation process. From time to time, the Company’s program is reviewed and validated by internal and external experts.
In general, our incident response process follows the NIST framework and focuses on four phases: (i) preparation; (ii) detection and analysis; (iii) containment, eradication, and recovery; and (iv) post-incident remediation. As cybersecurity incidents occur, including at third party providers, the Director of Information Security leads the Information Security Team through a standardized incident response process that focuses on responding to and containing the threat, minimizing any business impact, and evaluating its severity level. The severity level assessment determines how widespread the incident is and to what degree it could impact our overall business and manufacturing environment. In the event an incident is determined by the Information Security Team to be a high severity level, our cross functional team, with expertise in various disciplines, will assess the incident to determine if it has had a material affect or is reasonably likely of having a material effect on the Company’s business strategy, results of operations, or financial condition.