UNITED STATES
SECURITIES AND EXCHANGE COMMISSION
Washington, D.C. 20549
FORM 8-K
CURRENT REPORT
Pursuant to Section 13 or 15(d) of the Securities Exchange Act of 1934
Date of Report (Date of earliest event reported): October 15, 2021 (October 12, 2021)
Appgate, Inc.
(Exact Name of Registrant as Specified in Its Charter)
| Delaware | | 000-52776 | | 20-3547231 |
(State or other jurisdiction
of incorporation) | | (Commission File Number) | | (I.R.S. Employer
Identification) |
2333 Ponce De Leon Blvd., Suite 900, Coral Gables, FL 33134
(Address of principal executive offices) (Zip Code)
(866) 524-4782
(Registrant’s Telephone Number, Including Area Code)
Newtown Lane Marketing, Incorporated
c/o Graubard Miller
405 Lexington Avenue, 11th Floor
New York, New York 10174
(Former name or former address, if changed since last report)
Check the appropriate box below if the Form 8-K filing is intended to simultaneously satisfy the filing obligation of the registrant under any of the following provisions (see General Instruction A.2. below):
| ☐ | Written communications pursuant to Rule 425 under the Securities Act (17 CFR 230.425) |
| ☐ | Soliciting material pursuant to Rule 14a-12 under the Exchange Act (17 CFR 240.14a -12) |
| ☐ | Pre-commencement communications pursuant to Rule 14d-2(b) under the Exchange Act (17 CFR 240.14d -2(b)) |
| ☐ | Pre-commencement communications pursuant to Rule 13e-4(c) under the Exchange Act (17 CFR 240.13e -4(c)) |
Securities registered pursuant to Section 12(b) of the Act:
| Title of each class | | Trading Symbol(s) | | Name of each exchange on which registered |
| N/A | | N/A | | N/A |
Indicate by check mark whether the registrant is an emerging growth company as defined in Rule 405 of the Securities Act of 1933 (§230.405 of this chapter) or Rule 12b-2 of the Securities Exchange Act of 1934 (§240.12b-2 of this chapter).
Emerging growth company ☐
If an emerging growth company, indicate by check mark if the registrant has elected not to use the extended transition period for complying with any new or revised financial accounting standards provided pursuant to Section 13(a) of the Exchange Act. ☐
INTRODUCTORY NOTE
Unless the context otherwise requires, “we,” “us,” “our,” “Appgate” and the “Company” refer to Appgate, Inc., a Delaware corporation (f/k/a Newtown Lane Marketing, Incorporated), and its consolidated subsidiaries following the Closing (as defined below). Unless the context otherwise requires, references to “Newtown Lane” refer to Newtown Lane Marketing, Incorporated prior to the Closing. All references herein to the “Board” refer to the board of directors of the Company.
This Current Report on Form 8-K (this “Report”) is being filed by the Company in connection with the completion of the transactions contemplated by that certain agreement and plan of reorganization, dated February 8, 2021 (the “Merger Agreement”), entered into by and among Newtown Lane, Newtown Merger Sub. Corp., a Delaware corporation and wholly owned subsidiary of Newtown Lane (“Merger Sub”), and Cyxtera Cybersecurity, Inc. (d/b/a AppGate), a Delaware corporation (“Legacy Appgate”). Pursuant to the Merger Agreement, Merger Sub was merged with and into Legacy Appgate (the “Merger”), with Legacy Appgate surviving the Merger and becoming a wholly-owned subsidiary of the Company. The Merger was consummated on October 12, 2021 (the “Closing” and such date the “Closing Date”).
In connection with the Closing, we experienced a change of control (the “Change of Control”), as:
| ● | SIS Holdings LP (“SIS Holdings”), the sole stockholder of Legacy Appgate immediately prior to the Closing, received an aggregate of 117,149,920 shares of the Company’s common stock, par value $0.001 per share (the “Common Stock”), which resulted in SIS Holdings owning an aggregate of approximately 89% of the Company’s issued and outstanding Common Stock as of the date of this Report; |
| ● | The size of the Board was increased to five and four new directors were elected (as further described in this Report); and |
| ● | Jonathan J. Ledecky resigned from his position as President of the Company and Manuel D. Medina became the Executive Chairman of the Company, Barry Field became the Chief Executive Officer of the Company, Jawahar Sivasankaran became the President and Chief Operating Officer of the Company, Rene A. Rodriguez became the Chief Financial Officer of the Company, and Jeremy M. Dale became the General Counsel and Secretary of the Company. |
As a result of the foregoing, the Change of Control occurred with respect to the Company’s stock ownership and management upon the Closing. Therefore, we have determined to treat the Merger as a reverse merger and recapitalization for accounting purposes, with Legacy Appgate as the acquirer for accounting purposes. As such, the financial information, including the operating and financial results and audited financial statements included in this Report will be that of Legacy Appgate rather than that of our Company prior to the completion of the transactions described herein.
Item 1.01 Entry into a Material Definitive Agreement.
As disclosed previously in Newtown Lane’s Current Report on Form 8-K as filed with the Securities and Exchange Commission (the “SEC”) on February 9, 2021 by Newtown Lane (the “Merger Agreement 8-K”), Newtown Lane entered into the Merger Agreement with Merger Sub and Legacy Appgate. The Merger, together with the other transactions contemplated by the Merger Agreement, are referred to herein as the “Transactions”.
The summary of the Merger Agreement is included in Item 1.01 of the Merger Agreement 8-K and is incorporated herein by reference. The summary of the Merger Agreement is qualified in its entirety by reference to the full text of the Merger Agreement, a copy of which is filed as Exhibit 2.1 to this Report, and incorporated herein by reference.
Pursuant to the terms and subject to the conditions set forth in the Merger Agreement, the Transactions were consummated on the Closing Date.
Item 2.01 of this Report discusses the consummation of the Transactions and the entry into of the agreements relating thereto and is incorporated herein by reference.
Support Agreements
Summaries of the support agreements entered into by Newtown Lane in connection with the execution of the Merger Agreement are included in Item 1.01 of the Merger Agreement 8-K and are incorporated herein by reference.
The summaries of the support agreements are qualified in their entirety by reference to the form of each support agreement, attached as Exhibits 10.2 and 10.3 to this Report, respectively, and incorporated herein by reference.
Merger Registration Rights Agreement
On October 12, 2021, in connection with, and as a condition to, the Closing, Newtown Lane entered into a registration rights agreement (the “Merger Registration Rights Agreement”) with SIS Holdings and Ironbound Partners Fund, LLC, the owner of the majority of the outstanding Common Stock of Newtown Lane prior to the Closing (“Ironbound”, and together with SIS Holdings, the “Holders”), and, solely with respect to Section 3.1 of the Merger Registration Rights Agreement, Medina Capital Fund II – SIS Holdco, LP. Pursuant to the Merger Registration Rights Agreement, the Holders have the right to require us to file one or more registration statements with the SEC for the sale of our Common Stock held by the Holders, subject to certain exceptions. The Company is obligated to use its commercially reasonable best efforts to have a resale “shelf” registration statement declared effective with the SEC by February 9, 2022 (or May 10, 2022 if the SEC notifies the Company that it will “review” the registration statement). The Company will also be required to facilitate “takedown” offerings from the shelf upon demand by the Holders, provided that (i) the Company is eligible to use Form S-3 and (ii) the offering (x) has an anticipated offering price, net of the underwriters’ discount, in excess of $50.0 million or (y) constitutes the total aggregate registrable securities then held by all the Holders. The Holders may also require the Company to file an S-1 or S-3 registration statement for any registrable securities not included in the aforementioned “shelf” registration statement, provided the offering (i) has an anticipated offering price, net of the underwriters’ discount, in excess of $50.0 million or (ii) constitutes the total aggregate registrable securities then held by all the Holders. All holders of registrable securities party to the Merger Registration Rights Agreement are entitled to certain “piggyback” registration rights in subsequent offerings. Such holders are entitled to notice of a registered offering by the Company or by stockholders other than the Holders and to have their shares included on a pro rata basis. The Merger Registration Rights Agreement also provides that the Company will pay certain expenses of the Holders relating to the registrations and indemnify them against certain liabilities which may arise under the Securities Act and other federal or state securities laws.
The foregoing description of the Merger Registration Rights Agreement is qualified in its entirety by reference to the full text of the Merger Registration Rights Agreement, a copy of which is filed as Exhibit 10.1 to this Report, and incorporated herein by reference.
SIS Holdings and Ironbound Lock-up Agreement
On October 12, 2021, in connection with, and as a condition to, the Closing, SIS Holdings and Ironbound entered into a lock-up agreement with Newtown Lane (the “Lock-Up Agreement”), providing that the Company’s Common Stock held by such persons may not be transferred for a period of 12 months following the Closing, except to certain permitted transferees or pursuant to certain customary exceptions.
The foregoing description of the Lock-Up Agreement is qualified in its entirety by reference to the full text of the Lock-Up Agreement, a copy of which is filed as Exhibit 10.4 to this Report, and incorporated herein by reference.
Magnetar Convertible Senior Notes
Note Purchase Agreement
Concurrently with the execution of the Merger Agreement, Legacy Appgate entered into a note purchase agreement (the “Note Purchase Agreement”) with the lenders named on the Schedule of Lenders (as defined in the Note Purchase Agreement) attached thereto. Pursuant to the Note Purchase Agreement, Legacy Appgate agreed to sell, and the Initial Holders (as defined below) agreed to purchase, upon the terms and subject to the conditions contained in the Note Purchase Agreement, (i) $50.0 million aggregate principal amount of Legacy Appgate’s 5.00% Convertible Senior Notes due 2024 (the “Notes”) on the date of the initial closing (the “Initial Closing”), (ii) $25.0 million aggregate principal amount of Notes (the “Additional Notes”) on the Closing Date and (iii) at the election of Magnetar, up to $25.0 million additional Notes in one or more subsequent transactions, on or prior to February 8, 2022.
Under the terms of the Note Purchase Agreement, Magnetar shall have the right to fund up to 25% of certain issuances of indebtedness of Legacy Appgate or any of its subsidiaries that is either (i) convertible or exchangeable for capital stock of Legacy Appgate or any of its subsidiaries or (ii) issued with warrants or a similar equity component convertible or exchangeable for capital stock of Legacy Appgate or any of its subsidiaries. The Note Purchase Agreement also grants to Magnetar certain preemptive rights in respect to future issuances of equity of Legacy Appgate or any of its subsidiaries.
The Initial Closing and the issuance of $50.0 million aggregate principal amount of Notes in connection therewith took place on February 9, 2021. The Additional Notes (in an aggregate principal amount of $25.0 million) were issued on the Closing Date. The Notes and Additional Notes were issued under and are governed by the terms of the Note Issuance Agreement (as defined and described below).
The foregoing description of the Note Purchase Agreement is qualified in its entirety by reference to the full text of the Note Purchase Agreement, a copy of which is filed as Exhibit 10.5 to this Report, and incorporated herein by reference.
Note Issuance Agreement
Concurrently with the execution of the Merger Agreement, on the date of the Initial Closing, Legacy Appgate entered into a note issuance agreement (the “Note Issuance Agreement”) together with Legacy Appgate’s wholly-owned domestic subsidiaries (each, a “Guarantor”) and Magnetar Financial LLC (collectively, with its affiliates, “Magnetar”), as representative of the several initial holders named therein (“Initial Holders”). The terms of the Note Issuance Agreement and the Notes are summarized below; capitalized terms used in this section but not otherwise defined herein shall have the respective definitions ascribed to them in the Note Issuance Agreement:
Interest and Maturity. The Notes bear interest at 5.00% per annum if paid in cash and 5.50% per annum if paid in kind, payable, at the election of Legacy Appgate, entirely in cash, entirely in kind or a combination of in cash and in kind, which interest accrues from February 9, 2021, and will be payable semiannually in arrears on February 1 and August 1 of each year, beginning on August 1, 2021. The Notes will mature on February 9, 2024 unless earlier redeemed or repurchased.
Conversion upon Change of Control. If Legacy Appgate undergoes a Change of Control other than the Merger prior to maturity, each holder of Notes shall have the option to convert all or any portion of such Notes into Legacy Appgate common stock or, following entry into the Supplemental Agreement (as defined below), our Common Stock, subject to and in accordance with the terms of the Note Issuance Agreement, including the applicable conversion rate thereunder.
Conversion. Other than upon a Change of Control, prior to maturity, each holder of Notes shall have the option to convert all or any portion of such Notes into Legacy Appgate common stock or, following entry into the Supplemental Agreement, our Common Stock, subject to and in accordance with the terms of the Note Issuance Agreement, including the applicable conversion rate thereunder.
Guarantees; Conversion Obligations. The Notes are guaranteed by each of Legacy Appgate’s wholly-owned domestic subsidiaries. Upon the consummation of certain events resulting in Legacy Appgate becoming a direct or indirect subsidiary of any person (including the Merger), such acquiring person, any direct or indirect parent company thereof and each subsidiary thereof (immediately prior to such event) shall unconditionally guarantee Legacy Appgate’s Obligations and assume all of Appgate’s Conversion Obligations and Change of Control Conversion Obligations and, upon such assumption, Legacy Appgate shall be released from its Conversion Obligations and Change of Control Conversion Obligations.
Repurchase Upon a Fundamental Change. Upon the occurrence of a Fundamental Change at any time after a Public Company Event, each holder of Notes shall have the option to require Legacy Appgate to repurchase for cash all or any portion of such Notes, at a repurchase price equal to 100% of the principal amount thereof, plus accrued and unpaid interest thereon, subject to and in accordance with the terms of the Note Issuance Agreement.
Repurchase Upon a Change of Control. Upon the occurrence of a Change of Control other than the Merger at any time before a Public Company Event, each holder of Notes shall have the option to require Legacy Appgate to repurchase for cash all or any portion of such Notes, at a repurchase price equal to 102% of the principal amount thereof, plus accrued and unpaid interest thereon, subject to and in accordance with the terms of the Note Issuance Agreement.
Covenants. The Note Issuance Agreement contains restrictive covenants that, among other things, generally limit the ability of Legacy Appgate and certain of its subsidiaries (subject to certain exceptions) to: (i) incur additional debt and issue Disqualified Stock; (ii) create liens; (iii) pay dividends, acquire shares of capital stock, or make investments; (iv) issue guarantees; (v) sell assets and (vi) enter into transactions with affiliates. The foregoing restrictive covenants are subject to a number of important exceptions and qualifications, as set forth in the Note Issuance Agreement.
Events of Default. The Note Issuance Agreement provides for customary events of default which include (subject in certain cases to customary grace and cure periods), among others: (i) nonpayment of principal or interest; (ii) breach of covenants or other agreements in the Note Issuance Agreement; (iii) defaults in failure to pay certain other indebtedness; and (iv) certain events of bankruptcy or insolvency. Generally, if an event of default occurs and is continuing under the Note Issuance Agreement, Magnetar or the holders of at least 25% in aggregate principal amount of the Note then outstanding may declare the principal of, premium, if any, and accrued interest on all the Notes immediately due and payable.
The foregoing description of the Note Issuance Agreement is qualified in its entirety by reference to the full text of the Note Issuance Agreement, a copy of which is filed as Exhibit 10.6 to this Report, and incorporated herein by reference.
Supplemental Agreement
On October 12, 2021, in connection with Closing, Newtown Lane entered into a supplemental agreement (the “Supplemental Agreement”) with Legacy Appgate and Magnetar, as representative of the holders of the Notes, pursuant to which Newtown Lane, among other things, unconditionally guaranteed all of Legacy Appgate’s Obligations, including the Notes, and assumed all of Legacy Appgate’s Conversion Obligations and Change of Control Conversion Obligations.
The foregoing description of the Supplemental Agreement is qualified in its entirety by reference to the full text of the Supplemental Agreement, a copy of which is filed as Exhibit 10.7 to this Report, and incorporated herein by reference.
Magnetar Registration Rights Agreement
Concurrently with the execution of the Merger Agreement, Legacy Appgate and the holders of Notes entered into a registration rights agreement (the “Magnetar Registration Rights Agreement”), pursuant to which, following a Public Company Event (as defined therein), Legacy Appgate would be obligated to file a registration statement to register the resale of certain securities of Legacy Appgate (including Legacy Appgate common stock, or, following entry into the Supplemental Agreement, our Common Stock, issued upon conversion of the Notes) held by such holders of Notes.
The Company has assumed these registration obligations pursuant to the Supplemental Agreement described above.
The foregoing description of the Magnetar Registration Rights Agreement is qualified in its entirety by reference to the full text of the Magnetar Registration Rights Agreement, a copy of which is filed as Exhibit 10.8 to this Report, and incorporated herein by reference.
Indemnification Agreements
On October 12, 2021, in connection with Closing, the Company entered into an indemnification agreement with each of the current directors and executive officers of the Company. Each indemnification agreement provides, among other things, for indemnification to the fullest extent permitted by applicable law and our A&R Charter (as defined herein) and A&R Bylaws (as defined herein) against any and all expenses, judgments, fines, penalties and amounts paid in settlement of any claim. The indemnification agreements provide for the advancement or payment of all expenses to the indemnitee and for the reimbursement to us if it is found that such indemnitee is not entitled to such indemnification under applicable law and our A&R Charter and A&R Bylaws.
The foregoing description of the indemnification agreements is qualified in its entirety by reference to the full text of the form of indemnification agreement between the Company and each of indemnitee, a copy of which is filed as Exhibit 10.9 to this Report, and incorporated herein by reference.
Item 2.01 Completion of Acquisition or Disposition of Assets.
The disclosure in Item 1.01 of this Report discusses the consummation of the Transactions and the entry into agreements relating thereto and is incorporated herein by reference.
FORM 10 INFORMATION
Item 2.01(f) of Form 8-K states that if the registrant was a shell company, as Newtown Lane was immediately before the Merger, then the registrant must disclose the information that would be required if the registrant were filing a general form for registration of securities on Form 10. Accordingly, the Company is providing below the information that would be included in a Form 10 if it were to file a Form 10. Please note that the information provided below relates to the Company after the consummation of the Merger, unless otherwise specifically indicated or the context otherwise requires.
Cautionary Note Regarding Forward-Looking Statements
This Report, including the documents incorporated by reference into this Report, contain forward-looking statements within the meaning of Section 21E of the Securities Exchange Act of 1934, as amended, and Section 27A of the Securities Act of 1933, as amended. Statements that do not relate strictly to historical or current facts are forward-looking and can be identified by the use of words such as “anticipate,” “estimate,” “could,” “would,” “should,” “will,” “may,” “forecast,” “approximate,” “expect,” “project,” “seek,” “predict,” “potential,” “intend,” “plan,” “believe,” and other words of similar meaning. Without limiting the generality of the foregoing, forward-looking statements contained in this Report include statements regarding the Company and its industry relating to matters such as anticipated future financial and operational performance, business prospects, the percentage of the Company’s future revenue derived from subscription term-based licenses compared to revenue from services, expected future increases in revenue and sales, including increasing the Company’s customer base, sales to existing customers, the U.S. federal government and through the Company’s channel partners, expected increases in gross profit and gross margin, the Company’s expected future net loss position, planned investments in sales and marketing and related increases in operating and general and administrative expenses and planned investments in research and development as a result of the Company’s expected growth, the expected future growth of the cybersecurity industry, including the growth in adoption of Zero Trust security solutions, the Company’s ability to innovate and add new functionality to existing products through research and development, the Company’s ability to fund working capital and capital expenditures for the next 12 months, potential future investments in the Company by Magnetar Financial, LLC under the Notes, the Company’s ability to remain in compliance with covenants under the Notes, the impact of foreign currency exchanges and inflation on the Company’s business, strategy and plans and similar matters.
The forward-looking statements included in this Report involve risks and uncertainties that could cause actual results to differ materially from projected results. Accordingly, investors should not place undue reliance on forward-looking statements as a prediction of actual results. The Company has based these forward-looking statements on current expectations and assumptions about future events, taking into account all information currently known by the Company. While the Company considers these expectations and assumptions to be reasonable, they are inherently subject to significant business, economic, competitive, regulatory and other risks and uncertainties, many of which are difficult to predict and beyond our control. These risks and uncertainties include, but are not limited to:
| ● | our future financial performance, including our expectations regarding our total revenue, cost of revenue, gross profit or gross margin, operating expenses, including changes in operating expenses and our ability to achieve and maintain future profitability; |
| ● | the effects of increased competition in our markets and our ability to compete effectively; |
| ● | market acceptance of our products and services and our ability to increase adoption of our products; |
| ● | our ability to maintain the security and availability of our products; |
| ● | our ability to develop new products, or enhancements to our existing products, and bring them to market in a timely manner; |
| ● | our ability to maintain and expand our customer base, including by attracting new customers; |
| ● | the potential impact on our business of the ongoing COVID-19 pandemic; |
| ● | our ability to maintain, protect and enhance our intellectual property rights; |
| ● | our ability to comply with laws and regulations that currently apply or become applicable to our business both in the United States and internationally; |
| ● | our ability to maintain an effective system of disclosure controls and internal control over financial reporting; |
| ● | SIS Holdings’ significant influence over our business and affairs; |
| ● | the future trading prices and liquidity of our Common Stock; |
| ● | our indebtedness, which may increase risk to our business; and |
| ● | other risks and uncertainties, including those described under the section below entitled “Risk Factors.” |
The forward-looking statements contained in this Report are based on the Company’s current expectations and beliefs concerning future developments and their potential effects on the Transactions and the Company. There can be no assurance that future developments affecting the Company will be those that the Company has anticipated. These forward-looking statements involve a number of risks, uncertainties (some of which are beyond the Company’s control) or other assumptions that may cause actual results or performance to be materially different from those expressed or implied by these forward-looking statements. These risks and uncertainties include, but are not limited to, those factors described under the heading “Risk Factors” below. Should one or more of these risks or uncertainties materialize, or should any of the assumptions prove incorrect, actual results may vary in material respects from those projected in these forward-looking statements. The Company will not and does not undertake any obligation to update or revise any forward-looking statements, whether as a result of new information, future events or otherwise, except as may be required under applicable securities laws.
Business
Mission Statement
Our mission is to empower and protect how people work and connect by enabling any user on any device to securely access any application, use any network, and perform any transaction.
Overview
Appgate is a cybersecurity company that protects against breaches and fraud through innovative, identity-centric, context-aware, Zero Trust1 solutions. Zero Trust is an approach to cybersecurity that shifts defenses from static, network-based perimeters to a dynamic security model based on users, assets, and resources. Appgate exists to provide modern organizations with a solution to the growing cyber crisis, against which their traditional cybersecurity tools are proving ineffective. The need for Appgate is growing as enterprise information technology (“IT”) changes with the adoption of new digital technologies, evolving IT architectures, and the increasing need to accommodate users’ preference to “work from anywhere.” While these changes are necessary for organizations to work efficiently and effectively, they introduce new security challenges. The corporate network is no longer consolidated and neatly protected behind a firewall, but rather has expanded into sprawling, distributed, hybrid environments, often with access to multiple clouds, that are more vulnerable to attacks. Adversaries have simultaneously grown stealthier, more sophisticated, and more determined, and have a track record of outmaneuvering legacy cybersecurity tools and wreaking havoc on organizations. Taken together, these changes have created a perfect storm which required a fundamentally different solution, Zero Trust, of which we have been a pioneer and recognized industry leader.
Appgate’s purpose-built solutions uniquely apply the principles of Zero Trust to protect organizations against growing cyber threats by applying the right access policies, and in the event of a security breach, limiting adversaries’ ability to cause widespread damage. Our solutions also reduce operational complexity by integrating with existing enterprise software and distinctively protecting users and networks across all IT infrastructure environments, whether cloud, hybrid, or on-premises, thus providing a ubiquitous, dynamic, user-centered foundation for organizations’ Zero Trust cybersecurity initiatives. Appgate enables businesses to meet both their immediate need to make their organizations resilient to adversaries without slowing down business, as well as their long-term need to develop a more modern, proactive cybersecurity approach essential for future success.
Appgate operated as a subsidiary of Cyxtera Technologies, Inc. (“Cyxtera”) until December 31, 2019, at which time Cyxtera spun out Appgate to become a standalone company. Appgate is headquartered in Coral Gables, Florida and had 423 full time employees across thirteen global offices as of June 30, 2021.
The Problem
Digital transformation, driven by growth in cloud computing, Software as a Service (“SaaS”), mobile devices, Internet of Things (“IoT”), and similar technologies, as well as increasing remote work, has changed the nature of cybersecurity risks by proliferating the number of entry points to organizations’ networks (often referred to as “increasing the attack surface”). Simultaneously, the number and sophistication of cyberattacks is ever-increasing. This combination of more vulnerable networks and more malicious activity has created a cybersecurity crisis, forever changing the threat landscape organizations face. According to Cybersecurity Ventures, cybersecurity breaches are expected to cause a record $6 trillion in aggregate damages in 2021 alone.
Traditional cybersecurity tools are not designed for today’s distributed, heterogeneous, and hybrid IT architectures. In large part, this is because traditional cybersecurity tools are perimeter-centric, or focused on the boundary between a private network and the public internet. This approach worked better historically when there were fewer entry points into an enterprise network. The perimeter-centric model is particularly problematic because it is built on a notion of implicit trust, which is the assumption that traffic initiated from within a network does not represent a risk. As a result, if there is a security breach, infiltrators can remain undetected, move laterally (i.e., after gaining initial access, progressively move through a network in search of sensitive and valuable data) across a network, and cause widespread damage.
Some of these traditional cybersecurity technologies have existed for well over two decades with little innovative change over that period of time. Many vendors of traditional cybersecurity tools have simply refreshed their product portfolios with better hardware, leaving the core security mechanism unchanged. For instance, virtual private network (“VPN”) technology has existed largely unchanged since the 1990s, and VPNs continue to be exploited regularly by adversaries.
These traditional security technologies are also often ineffective in newer cloud-based environments because they were not designed for the cloud and typically do not map well to cloud-based systems, causing friction and introducing security gaps. As organizations increasingly adopt cloud environments, security teams are facing a difficult choice – either mis-apply traditional security and networking tools to the cloud or introduce a new silo of cloud-only security and operational tools. Neither of these choices is secure or efficient.
| 1 | ZeroTrust enhances security by eliminating the implicit trust that is often granted based on physical or network location, instead requiring that all access be earned via dynamic attributes and strong authentication. Unlike traditional security models in which users are given overprivileged access and can easily move laterally within a network, Zero Trust only grants users access to resources that are needed to do their job at a particular time and place. Users are continuously monitored so that if their context or device changes, access can be revoked. This approach makes organizations much more resilient to attacks. |
Our Solution
Appgate’s software solutions and services, discussed in detail in the following paragraphs, use a fundamentally different identity-centric and context-aware approach grounded in the principles of Zero Trust to protect corporate users and consumers of online services. Zero Trust recognizes that the entire extended network is the attack surface, that no user, device, or application should be implicitly trusted, and that organizations must be resilient to attacks. We believe we have built the premiere pure-play Zero Trust platform capable of facilitating secure interactions between all devices, from all locations, in all IT environments.
Software:
Software Defined Perimeter (“SDP”) enables fast, secure connections for users and devices using the principles of Zero Trust. SDP offers comprehensive network security by segmenting resources and making them invisible to a user or device until trust is established. SDP uses adaptive and dynamic access policies based on user identity and device posture to continuously monitor users and limit lateral movement. This pioneering solution was the first SDP product to be Common Criteria Certified, which is the international “gold standard” for IT security. We believe that adoption of our SDP product is among the most pivotal steps an organization can take towards moving to a Zero Trust posture.
Risk Based Authentication (“RBA”) provides secure access between financial institutions and their customers to prevent transaction and financial fraud. RBA combines advanced authentication techniques and threat intelligence to authorize access and transactions. It allows for customizable and dynamic Zero Trust policy enforcement which enables seamless workflow processes.
Digital Threat Protection (“DTP”) offers digital threat visibility and comprehensive risk management to identify and eliminate attacks before they occur, across social media, phishing attacks, bogus websites, and malicious mobile apps. Its curated threat intelligence and continuous threat monitoring complements SDP and RBA to provide Zero Trust based protection throughout the threat lifecycle. It protects users against phishing attacks and account takeover attempts and provides business leaders with valuable reporting functionality.
Services:
Our Threat Advisory Services provide a dedicated, highly pedigreed team of consultants who provide breach and attack simulation in the form of customized vulnerability assessments and penetration testing, helping customers validate the effectiveness of their security infrastructure. In addition to providing a valuable service to our clients, their work allows us to stay at the cutting edge of cybersecurity threats and better understand the needs of our customers. This, in turn, provides us with feedback we can leverage to make our software products better. These advisory services also generate leads for our software solutions for organizations looking to achieve a Zero Trust posture.
We believe customers choose Appgate for the following six reasons:
| ● | Reduce network security risk: Appgate not only reduces the attack surface, which makes it harder for a hacker to penetrate, but it also limits an attacker’s ability to move laterally once in the network and applies continuous monitoring so that if a breach occurs, it is easier and faster to detect. |
| | | |
| ● | Integrate with their existing IT environments: We serve all IT environments, from legacy infrastructure to the cloud, and perform especially well against our competition in complex, hybrid environments that are pervasive in large enterprises and government agencies. |
| | | |
| ● | Improve the user’s experience: Our solutions provide a seamless and consistent user experience across all locations and devices, without the need for users to frequently re-authenticate themselves as they would using tools such as a VPN. Our solutions also make it easy for administrators to deploy and manage with a unified policy model active across all environments. |
| ● | Enhance existing security technologies: We have built a rich set of application programming interfaces (“APIs”) that integrate with organizations’ existing IT tools and allow us to extract useful context and, in turn, often extend the useful life of legacy systems by increasing their ability to defend against modern threats. |
| | | |
| ● | Prevent complex fraud: We offer a complete set of tools to prevent fraud for financial institutions and other consumer-facing organizations. Most attacks go through a multi-step process before causing significant damage to an organization. Appgate has solutions to address each phase, including planning and targeting, setup and launch and cashing out. Our solutions can be seamlessly tied together using risk orchestration, which allows customers to easily integrate protection layers based on risk tolerance and protect their consumers throughout the fraud attack lifecycle. |
| | | |
| ● | Proactively harden defenses: Understanding how threat actors operate enables us to proactively harden customer defenses. Our threat advisory services use advanced penetration testing, adversary simulation, and deep knowledge of evasion techniques to validate organizations’ defenses and uncover weaknesses before attackers do. |
We are a recognized market leader, given the quality of our offering and the strength of our vision. Examples of our industry recognition include the following:
| ● | Appgate was named a “Leader” in the Forrester New Wave™ for Zero Trust Network Access (Q3 2021). The report highlighted Appgate’s ability to address cloud, on-premises and hybrid IT models, noting that Appgate SDP "Is the best fit for companies that need high security and a self-hosted option. Appgate offers its Zero Trust Network Access (“ZTNA”) as a SaaS, but also as a self-hosted option for enterprises and agencies that need it." |
| | | |
| ● | Appgate was named a “Leader” in the Forrester Wave™ Zero Trust eXtended Ecosystem (Q3 2020). The report noted that Appgate already serves mega-enterprises and Department of Defense (“DoD”) customers, which is a testament to our capabilities and positions us well to benefit from the rising demand for Zero Trust solutions. |
| | | |
| ● | We were recognized by Forrester in their “New Tech: Zero Trust Network Access, 2021” report, where we were listed as a mature or “Late-Stage” vendor, indicating significant company tenure, number of customers, employees, and funding level as compared to our peers. |
| | | |
| ● | As of October 12, 2021, we have received 4.7 out of 5 stars from customer reviews on Gartner Peer Insights, with 95% of reviewers stating they would recommend Appgate to peers. |
| | | |
| ● | A 2021 Nemertes Research user survey rated Appgate a 9.5 out of 10 in its level of strategic importance to Zero Trust initiatives and further recognized Appgate SDP for “dramatically advancing strategic initiatives focused on implementing Zero Trust security, enabling digital transformation, supporting hybrid work-from-anywhere environments and improving employee satisfaction”. |
| | | |
| ● | Our Risk-Based Authentication solution was named a “Leader” in Quadrant Solutions’ SPARK Matrix™: Risk Based Authentication (RBA), 2021 report. |
| | | |
| ● | Appgate was 1 of 18 cybersecurity leaders selected from a list of hundreds of companies to participate in the National Institute of Standards and Technology (“NIST”) National Cybersecurity Center of Excellence, an initiative designed to provide guidance to organizations on how to implement Zero Trust architecture. |
| | | |
| ● | Our products and services serve some of the largest and most security-conscious organizations, including Fortune 10 enterprises, the US government, and many of the world’s largest financial institutions. We have authority to operate within the DoD, we’re certified for the Department of Homeland Security (“DHS”), and our Software Defined Perimeter (SDP) product is Common Criteria certified, indicating we meet the most stringent security requirements of government entities. |
| | | |
Currently, we serve over 600 organizations, including domestic and international government agencies and Fortune 500 enterprises that include at least one of the top-five largest companies in the defense contracting, telecommunications, and oil and gas sectors. We serve a global customer base across 40 countries. For the twelve months ending June 30, 2021, Appgate generated approximately $37 million of revenue and net losses of approximately $47 million. We expect losses to continue for the foreseeable future as we prioritize growth.
Industry Background
Cybersecurity attacks are increasing in severity and frequency as lateral movement, ransomware, and insecure remote access are pervasive.
Cyber threats are rising as adversaries are highly motivated and increasingly sophisticated in their approach. According to a report by Cybersecurity Ventures, breaches are expected to cost $6 trillion in damages in 2021, an aggregate cost greater than the GDP of any country in the world except the US and China. Cybersecurity Ventures predicts that in 2021, a ransomware attack will occur every 11 seconds, up nearly four times since 2016. One of the leading drivers behind the increasing costs of breaches is an attacker’s ability to remain undetected in a network for a long period of time and move laterally across it. According to IBM, the average breach in 2020 took 207 days to detect and another 73 days to contain, giving an attacker plenty of time to cause significant financial and reputational damage to an organization. Stopping lateral movement is essential to any security posture and is at the core of Appgate’s Zero Trust strategy.
The 2020 “SolarWinds” attack is an example of how costly a breach can be. A nation-state breached the networks of thousands of organizations, including as many as 425 of the Fortune 500 and all branches of the U.S. military, after clients of SolarWinds downloaded a software update that was infected with malicious code. The breach occurred sometime between March and June of 2020 and went undetected by traditional perimeter-based network security solutions until December of that year. The perpetrators moved laterally within the networks of these organizations, gathering sensitive data, and installing more malware. It will take years to contain the vast damages that are expected to cost up to $100 billion.
Following the SolarWinds attack, guidance was released by NIST, the National Security Agency (“NSA”), and the Cybersecurity and Infrastructure Security Agency (“CISA”) recommending a Zero Trust security approach. Additionally, on May 12, 2021, President Joe Biden issued an Executive Order explicitly calling for the adoption of a Zero Trust Architecture to improve the nation’s response to “persistent and increasingly sophisticated malicious cyber campaigns that threaten the public sector, the private sector, and ultimately the American people’s security and privacy.” The federal government continues to lead the industry in setting standards with the September 2021 release of a Zero Trust maturity model and Zero Trust strategy documents.
In addition to threats caused by external actors, insider threats, typically coming from employees or third-party contractors, also pose a growing security threat to organizations. According to IBM, non-malicious insiders caused 23% of organizational data breaches in 2020. While insider breaches are most frequently caused by simple human error, these non-malicious breaches are still expensive, with an average cost of $3 million per breach in 2020. Therefore, it is critical to limit access to only those resources individuals require to do their job.
Finally, identity fraud is also on the rise as cyber criminals are directly targeting consumers and financial institutions. According to Javelin Strategy & Research’s 2021 Identity Fraud Study, total identity fraud losses soared to a record $56 billion in 2020. Commercial banks are a frequent target of criminals, who use targeted email phishing, social media, and other strategies to induce bank employees and their consumers to inadvertently share their credentials. The COVID-19 pandemic has accelerated this trend, as more consumers moved to online and mobile channels to execute banking transactions. As consumers increasingly rely on these channels, financial institutions must rely on best-in-class authentication and security protocols to protect against fraud.
Because of the ever-evolving threat landscape, the cybersecurity market is experiencing significant growth as “next-generation” security solutions are designed to address these many challenges.
Traditional security tools are being rendered ineffective by the move to distributed IT environments, the growing prevalence of remote workforces, persistent human error, and increased consumer engagement on digital platforms.
Historically, security has centered around network perimeters, not users. Traditional perimeter-centric security tools, such as VPNs, firewall equipment, and network access control equipment were designed for a network infrastructure and threat landscape that no longer exist. Many vendors of these perimeter-centric technologies have simply refreshed hardware without altering the flawed security paradigm on which these legacy solutions are based. While the perimeter-centric approach used by these technologies made sense previously, it’s ineffective and easily exploitable in a modern environment for several reasons.
First, the network perimeter has evaporated as organizations’ infrastructures and people’s ways of working have evolved. Today’s hybrid networks now include on-premises, public and private cloud resources, or a combination of these (i.e., hybrid). The wide adoption of Infrastructure-as-a-Service (“IaaS”), SaaS, mobile devices, IoT, and large-scale remote working underscore just how far organizations have moved from traditional networking. Organizations now expect their workers to securely move from place-to-place and device-to-device without losing productivity. These factors have dramatically increased the attack surface, the scope of network vulnerabilities, and the likelihood of network infiltration, as each new user, connection, device, or online interaction introduces risk.
Second, the network is vulnerable and therefore the likelihood of a breach continues to grow. Not only are the number of attacks and sophistication of adversaries increasing, but also there is risk coming from the impacts of human error, which account for a large portion of data breaches. Even as network security technology improves, you can never fully solve the human element, as people reuse passwords, click links, download files, and don’t update software.
Finally, the perimeter-centric model was built on the notion of implicit trust, in which users, once inside the network, are granted access to more resources than they need. As a result, if a breach occurs and an attacker is inside the network, they are easily able to perform reconnaissance, exploit vulnerable systems, and live undetected while they carry out their mission and cause widespread damage.
This context indicates why specific security technologies need to be replaced. VPNs provide remote access, not security. In fact, VPN entry points represent well-known and widely exploited vulnerabilities. VPNs also perpetuate the outdated model of a single network perimeter entry point (i.e., not a distributed network architecture) and broad network access privileges. Network access control solutions are similarly outdated. For instance, because they are hardware-based and require physical proximity to users, they have been rendered ineffective by the shift to work-from-home. They also have an inherently “coarse-grained” access control model – allowing or denying access only to broad sections of the network, rather than to individual resources, thus frequently giving users access to more resources than they need. While traditional firewalls will always have a place in organizations’ network infrastructure, they are not suited for controlling access by remote users with granularity or fidelity. Firewall policy models are oriented around IP addresses, not users, therefore limiting their ability to adapt to today’s identity-centric security needs.
Organizations have adopted a complex set of cybersecurity tools that do not always integrate well.
Many organizations struggle with a large set of mismatched and overlapping cybersecurity tools. In 2020, IBM estimated that the average large enterprise uses an average of 45 cybersecurity tools, with some large organizations operating with in excess of 100 tools. Unfortunately, many of these tools do not integrate well, resulting in significant performance issues and leaving organizations with operational complexity and management difficulties. Some larger legacy security providers have tried to address this issue by creating portfolios of products that have generally been compiled through the acquisition of disparate solutions. While tools in these portfolios are usually easier to manage, the mix of products typically are not all “best of breed” and often require a complete system overhaul that can be time consuming and expensive. This drives the need for organizations to adopt a solution that simplifies and integrates technologies together.
Our Solution
Appgate offers software solutions and services to address these changing cybersecurity threats:
Appgate SDP: In traditional IT architectures, employees, contractors, and vendors have overprivileged access across multiple IT environments, exposing many attack surfaces. Appgate SDP is designed to ensure trusted network access for all corporate users across all devices and IT environments, including cloud, hybrid, or on-premises. We empower organizations to defend their network from wrongful access and continuously monitor for changes in user behavior once a connection is made. The network remains invisible until a user is authenticated and connected, so that no ports are exposed and open to attacks. Once authenticated and on the network, SDP employs the principles of least-privileged access, which dictate that users can only access resources they need to do their job. Access is conditional, based on many factors, and if any one of them change during the online session, the user can be denied access in part or in full to resources and applications. The most common Appgate SDP use cases include VPN replacement for remote access, cloud and hybrid deployments, cloud migrations, securely providing third-party access, secure Development and Operations (“DevOps”), and integrating Merger & Acquisition (“M&A”) assets into a secure network environment.
Digital Threat Protection: Consumers are increasingly reliant on digital platforms to conduct daily tasks, which creates greater opportunities for fraud. Appgate helps organizations minimize the impact of fraud for themselves and for their consumers. Most cyberattacks start with a phishing attempt and rapidly escalate from there. Appgate’s DTP solution helps combat external threats, including phishing links, malicious mobile apps, and fraudulent websites, targeting consumers. It illuminates threats lurking online, continuously monitors activity, and takes swift action to stop attacks before damage is done, and often before intended victims are even aware.
Risk-Based Authentication: In order to augment weak authentication measures, like the password, organizations have unintentionally created friction for their customers. RBA offers an intelligent and data informed approach to authenticating users without friction. Our solution uses real-time behavioral risk assessments, context-based authentication, and machine learning to protect individuals against targeted attacks. It employs strong authentication and transaction monitoring to determine if the person attempting to access their account is legitimate, and if not, access is denied. During an online session, the user’s activity is constantly monitored for changes in behavior. Transactions can be blocked or challenged in real-time, preventing account takeover.
Appgate Threat Advisory Services: Because no cybersecurity system is infallible, it is critical for an organization to address weaknesses in their network before an attacker does. Appgate’s Threat Advisory Services proactively identifies vulnerabilities and validates defenses. We use highly sophisticated, bespoke processes based on the individual needs of our customers to simulate nation-state-level and other complex attacks. These engagements help organizations test and validate the security investments they’ve made and can lead to the implementation of our software solutions based on remediation recommendations as we help our customers accelerate their Zero Trust journey. Another benefit is that we can use real-time information from our services engagements to stay up to date on the evolving cybersecurity threats to inform our software technology roadmap, helping us more rapidly address our customers’ evolving needs.
Key Benefits
We believe we provide unique and innovative cybersecurity solutions to address the security challenges faced by any modern organization and are a preferred security vendor for the following reasons:
| ● | Pure-play Zero Trust security provider. As a pioneer, leader, and one of the earliest proponents of Zero Trust, we have built and honed a pure-play platform based on Zero Trust principles to facilitate secure interactions for organizations, their devices, and their consumers. Our leading software solutions are, and have always been, rooted in Zero Trust principles and provide organizations with a strong foundation in their shift towards this modern cybersecurity posture. |
| ● | Effective across all environments. Modern organizations require infrastructure to support on-premises, hybrid, cloud, IoT, bring your own device (“BYOD”), and other disparate platforms. Most of our competitors provide solutions for some of these platforms and none of our competitors provide an effective solution that can dynamically adjust for changes in context across all environments. The result in most organizations is a patchwork of products that often do not integrate well, thereby creating additional complexity, security gaps, and administrative burden. We believe we were among the first to identify the need for and deliver an enterprise class, software-based, unifying solution that dynamically works across all environments. |
| ● | A better approach to network security. Our solutions use the principles of Zero Trust to strengthen network security, making it harder for adversaries to attack a network. Additionally, if a breach were to occur, an attacker’s lateral movement would be restricted so they can be identified and contained swiftly and overall damages could be limited. |
| ● | Prevents complex fraud. We offer financial institutions and other consumer-facing organizations a complete set of solutions based on Zero Trust principles to prevent fraud. Unlike traditional rules-based products, our solutions incorporate machine learning and behavioral analytics to identify and stop fraudulent activities, and dynamically assess risk to make decisions about when to authenticate connections. Our proprietary technology is also focused on detecting and deactivating targeted external threats which utilize phishing links, malicious mobile apps, or fraudulent websites. We continuously analyze and monitor an array of digital channels to identify threats, and execute site take-downs, often before intended victims are even aware. Finally, we provide rich insights on victims, so organizations are better prepared to stop future complex fraud campaigns. |
| ● | Supports business growth. Appgate’s solutions provide a strong, secure foundation allowing customers to grow at the pace of their business, unconstrained by cybersecurity worries. Appgate’s security solutions are easily extendable, enabling customers to onboard new customers, vendors, and M&A assets without compromising security. |
| ● | Allows secure “work from anywhere”. Appgate’s solutions offer fast, secure, direct connections from any location, enabling increasingly popular remote workforce models. Unlike perimeter-based approaches, our SDP platform uses a uniform identity-centric policy model to connect users from any device in any location. While remote workforce models typically invite security risk, Appgate’s security architecture is designed to ensure that increased workforce mobility does not create additional vulnerable access points. |
| ● | Strong integration capabilities. Our solutions can be easily deployed alongside existing security systems and across the entire IT environment. We utilize what we believe is the richest set of APIs amongst our peers to enable our solution to coordinate and communicate with other IT systems and improve the interoperability with other security products. Our approach allows customers to both extend the reach and value of their existing security and non-security tools by integrating them into our Zero Trust security solutions. We believe this value proposition enables a faster purchasing decision and differs from “next generation” security solutions that require an overhaul of a customer’s existing security system. |
| ● | Empowers digital transformation. Because our solutions are highly compatible with other technologies, Appgate customers are emboldened to adopt new, transformative non-security solutions without fear of integration issues. Unlike many legacy security tools, Appgate’s solutions are highly conducive to digital transformation and empower customers to continue on their digital journey. |
| ● | Enhanced customer experience. Our products provide an enhanced, agile experience for end users and administrators for the following reasons: |
| | | |
| o | Seamless end user experience: We provide automatic, dynamic access without having to frequently engage with the end user or disrupt workflow processes. Users are authenticated the same way regardless of where they are located or what device they are using. This approach differs from, and can be a replacement for, inflexible tools like VPNs and static multi-factor authentication systems, which often require users to re-authenticate themselves routinely, frustrating users. Our fraud protection suite is designed to stop attacks as they are unfolding and before the user is even aware. It is designed to fully protect them from phishing attacks, malware downloads and fraudulent transactions. |
| | | |
| o | Uniform policy model: We allow system administrators to create a single set of access policies that can be used uniformly across multiple disparate environments, increasing ease of use, operational efficiency, and security. This is in sharp contrast to not only traditionally siloed products (e.g., VPNs, NACs), but also many other ZTNA providers, who utilize static (versus dynamic) security rules or who cannot secure access for on-premises users. |
| o | Customer support and innovation: We partner with our customers on their Zero Trust journeys to ensure they receive maximum value from our products. We do so by providing first-class customer support and continually innovating to meet our customers’ needs. Our customer success team works closely with our customers throughout their entire life cycle, maintaining an open line of communication, frequently requesting feedback to ensure we are meeting their needs, and supporting them as new needs arise. By doing so, we become an extension to our customers’ teams. Partnering with our customers also influences how we prioritize our technology roadmap and enhances the value of our products to meet their changing needs. We collect customer feedback systematically, including quarterly feedback from our Customer Advisory Board, a panel comprised of select customers who are among the heaviest users of our solutions. |
| | | |
| o | Improved Operational Efficiency: Adoption of Appgate’s user-friendly software solutions frequently leads to improved operational efficiency for organizations. A recent Nemertes survey concluded that all respondents reported improvements in one or more key operational metrics, including average user provisioning time, average login time, and number of access-related security tickets, after adopting Appgate’s solutions. |
Competitive Strengths
Our competitive strengths include:
| ● | Leading Zero Trust product providing differentiated efficacy and user experience. Our solutions were purpose-built to meet the needs of modern organizations, whose networks are transforming with the expansion of cloud, SaaS, mobile, IoT, and remote working. Appgate’s SDP Zero Trust Network Access was designed to function and integrate across all IT environments, including cloud, hybrid, and on-premises, and as a result, it is the only product to do so effectively. Our user-friendly product allows system administrators to create a single set of access policies that can be used uniformly across multiple environments, reducing risk and administrative resources. Our solutions also integrate well with many existing security systems. We accomplish this through our broad set of APIs, which not only can be quickly deployed to extend the usefulness of existing systems, but also extract threat data and context from other technologies which we in turn can use to enrich our risk scoring and authentication decisions. |
| ● | Industry leading reputation. Our SDP product was named a “Leader” in the Forrester New Wave™ for Zero Trust Network Access (Q3 2021) and, as of October 12, 2021, received 4.7 out of 5 stars from customer reviews on Gartner Peer Insights. SDP was also recognized by Forrester in their “New Tech: Zero Trust Network Access, 2021” report, as a mature or “Late-Stage” vendor, indicating significant company tenure, number of customers, employees, and funding level as compared to our peers. Our Risk-Based Authentication solution was named a “Leader” in Quadrant Solutions’ SPARK Matrix™: Risk Based Authentication (RBA), 2021 report. We believe these high-profile recognitions received from trusted industry experts have elevated our reputation with existing and prospective customers. |
| ● | Strong customer focus. We are a trusted, long-term partner to our customers and are devoted to offering exceptional service. Our customer success team not only works with customers during the sales and renewal process, but also works with and supports our customers throughout their entire journey. They accomplish this through frequent communication and quarterly business reviews, helping them through new issues/use cases as they arise, and consistently seeking feedback to improve our products and services. Appgate also runs a Customer Advisory Board to enhance the open dialogue across customers to ensure we understand their changing needs. Our customers’ feedback is used as a direct input to our innovation roadmap so that we can quickly rollout the changes that we know are the most critical to our customers. Our goal is to become a true partner to our customers, involved in their day-to-day operations, going above and beyond a transactional vendor relationship. We continue to invest in our channel partners to increase customer adoption and satisfaction. A recent Nemertes survey of our customers revealed that 100% of respondents said Appgate accelerated their digital transformation. Of those implementing Zero Trust, they ranked Appgate’s importance to their strategy 9.5 out of 10. |
��
| ● | Demonstrated “license to win” with proven integrated sales and engineering approach. Our robust product offerings currently serve over 600 customers including Fortune 100 enterprises and domestic and international government agencies. We attract blue chip private and public sector organizations due to our integrated technical sales approach. We extend our customer reach through our trusted channel partners, such as Lumen, Optiv, Presidio, Guidepoint Security, DXC, TechMatrix, SageNet, Q2, Alkami, GBM, CLM, Kite, and Cybernet using a sell-with approach to avoid conflicts and increase win rate. Our customer acquisition engine is complemented by our strong sales engineering team which can powerfully demonstrate the value of our product to even the largest, most complex prospective customers. While our solutions have proven suitable for these large customers, they are also affordable and can meet the needs of organizations of any size. |
| ● | Highly experienced management team with a singular focus on cybersecurity threats. Our senior management team is composed of experienced executives with extensive expertise in the cybersecurity industry as well as knowledge of the markets in which we operate. The members of our senior management team have an average of over 20 years of experience in the enterprise technology and cybersecurity spaces and have a strong historical track record of success. Our seasoned executives were among the earliest pioneers in the Zero Trust security movement and are devoted to the continued growth of our business. |
Our Opportunity
The need for Zero Trust access and authentication solutions is increasing as more organizations expand their predominantly hybrid IT infrastructures to account for cloud computing, SaaS, mobility, IoT, BYOD, and remote working, thus introducing new attack vectors that traditional perimeter-based solutions cannot protect. Digital fraud is also on the rise as digital transaction volumes continue to grow. While these shifts were well underway prior to the COVID-19 pandemic, its impact has only accelerated these trends. For example:
| ● | According to 451 Research in 2020, hybrid IT environments are the most common amongst organizations, with approximately 60% of organizations currently operating or planning to operate using hybrid IT environments. |
| ● | Gartner estimates that public cloud services end user spend will grow at a 21% compound annual growth rate (“CAGR”) over the next three years. |
| ● | At the end of 2021, 99% of organizations will be using one or more SaaS solutions. |
| ● | Ericsson expects mobile data traffic to grow 4.5x over the next 6 years, representing a 28% CAGR. |
| ● | The number of connected IoT devices is expected to increase from approximately 9 billion in 2020 to approximately 14 billion in 2024, implying a 12% CAGR, according to 451 Research. |
| ● | BYOD has been normalized, evidenced by a 2012 Cisco study that found over 95% of organizations have allowed employee-owned devices in the workplace. |
| ● | PricewaterhouseCoopers estimates that over 50% of US enterprises will adopt a permanent hybrid (remote / in-office) workweek following the COVID-19 pandemic. |
| ● | The Federal Trade Commission reports that Americans lost over $3 billion to fraud in 2020. Key factors contributing to this large loss include COVID-19-related acceleration of e-commerce and online food delivery. |
| ● | Over 70% of Americans reported use of peer-to-peer (“P2P”) payment applications in 2020, ultimately prompting the Federal Communications Commission (“FCC”) to issue a warning about potential fraud in 2021. |
With these changes and the fact that cyber threats are on the rise, the need for organizations to adopt Zero Trust solutions is becoming more urgent.
Our Zero Trust SDP product can provide seamless secure network access across all environments, including cloud, hybrid, and on-premises. Therefore, we believe it is well positioned to continue to displace and take share from traditional network security solutions, such as firewalls, VPNs, NACs, and intrusion detection systems, as these legacy solutions are not built for cloud or hybrid IT environments and thus increase the risk of network exposure. We are also well positioned against cloud only cybersecurity providers given the prevalence of hybrid IT environments.
Our total addressable market encompasses hybrid, cloud, and on-premises network security, which Gartner estimates is a combined $39 billion market opportunity in 2021, expected to grow at a 14% CAGR to reach $57 billion by 2024. As more organizations migrate their IT to the cloud and embrace hybrid architectures, the need for a new network security approach will become increasingly apparent, and we believe we are well positioned to grow and take share in this market for the reasons discussed above.
We believe we are also well positioned to benefit from the recent rising interest in the idea of a Secure Access Service Edge (“SASE”). This term, recently created by the analyst firm Gartner, encompasses the trend of integrating many security and network technologies to secure hybrid, cloud, and on-premises environments. Appgate SDP is a recognized leader in ZTNA, which we believe is the most critical element of SASE because there cannot be security without securing access to the network first. Given our positioning, we believe our Zero Trust platform will be among the earliest beneficiaries of the SASE trend.
Our RBA and DTP solutions address Fraud Detection and Prevention (“FDP”). According to Global Market Insights, FDP was a $20 billion market in 2018 and expected to grow at a 23% CAGR from 2019-2025, which implies a total market size of $30 billion in 2020. The continued growth of online banking, e-commerce and P2P payment applications underpins the need for robust solutions to defend against pervasive, complex, and always-evolving fraud schemes. While growth in digital transactions has been ongoing, the COVID-19 pandemic has further accelerated this trend as more people have moved online to complete transactions, providing even greater opportunity for increased fraud.
Additionally, our DTP offerings are well-positioned to capitalize on the growing set of active and targeted phishing campaigns, as well as the increasing use of malicious websites and mobile apps for criminal purposes. Zero Trust should extend to the set of digital properties owned by the organization; ensuring that their customers aren’t deceived by fraudulent websites, phishing campaigns, or mobile apps is critical to these businesses’ reputations.
Growth Strategies
We expect to work with new and existing customers to support their Zero Trust journeys and beyond. Key elements of our growth strategy include:
| ● | Continue to grow customer base. While our solutions are uniquely positioned to serve large, regulated, security-conscious organizations with complex, hybrid IT environments, our solutions also offer value to medium and small sized customers. We believe we can continue to grow our customer base as we scale our sales team and increase our investment in channels and strategic partners. |
| ● | Expand with existing customers. We utilize a land and expand strategy through which we typically expand a customer account by adding new use cases or more users, including third-party users as contractors. We continue to invest in our customer success function, focused on retention and increased customer cross-selling. |
| ● | Grow our global footprint. We currently have customers across over 40 countries and have offices in 8 countries, reflecting our investment to be a global company and our success selling products internationally. In the twelve months ended June 30, 2021, international sales represented 52% of our revenue. While we expect our international markets to continue to grow, we anticipate the growth in the United States to outpace that of international markets. |
| ● | Expand our channel and product partnerships. Our Zero Trust solutions are highly complementary to a number of other security products, and as such, we have built a number of highly strategic product and go-to-market partnerships. Our products are easy to deploy and can be distributed by value-added resellers and service providers. We have strong growing channel partnerships with Lumen, Optiv, Presidio, Guidepoint Security, DXC, TechMatrix, SageNet, Q2, Alkami, GBM, CLM, Kite, and Cybernet, among others and work closely with federal systems integrators such as Raytheon, Northrop Grumman, and ManTech, who are building out solutions around our products for wider distribution. |
| ● | Expand our presence with U.S. federal government. With NIST, The White House, and other agencies endorsing the adoption of Zero Trust, we expect to have ample opportunities to leverage our early and continued success with the Department of Defense and Department of Homeland Security and to build trust with other government agencies and departments. Our solution was the first SDP product to be Common Criteria Certified, which is the international “gold standard” for Information Technology security. Common Criteria is recognized by 30 nations and was developed by the United States, United Kingdom, Canada, France, Germany, and the Netherlands. |
| ● | Innovate to add new functionality and use cases. We invested 28% of our revenue in research and development in the twelve months ended June 30, 2021 and maintain a robust product and technology roadmap. Our roadmap incorporates customer feedback which gives us confidence that we will be able to monetize our development efforts. We seek to offer highly scalable, flexible, and user-friendly products to address a variety of high-impact use cases. |
Our Technology and Architecture
Appgate’s cybersecurity solutions empower and protect how people work and connect. Our solutions are designed to enhance security, limit the ability of attackers to succeed, and minimize damage in the event of a breach. We recognize that IT, business, and security infrastructures are complex and can act as impediments to innovation, security, efficiency, and effectiveness. Organizations need security solutions that can be easily and effectively deployed and integrated into their existing environments.
Our solutions are designed with customer integration and customer success in mind, and this philosophy has influenced our technology architectures. We believe that customers should retain the choice of where and how to deploy their security infrastructure, enforce access, and route traffic. As such, we have designed and architected our solutions to support secure access to the cloud and on-premises.
Appgate SDP
Our Zero Trust Network Access solution, Appgate SDP, is purpose-built to secure enterprise environments by applying the core principles of Zero Trust. With Appgate SDP, our customers have successfully achieved enterprise Zero Trust security, at scale and at speed, integrated into their IT and security teams, business processes, and technologies.
The Appgate SDP architecture is fully aligned with the NIST Zero Trust model, which contains the following fundamental principles:
| ● | No implicit trust. There is no inherent trust (or access) granted to assets or user accounts based solely on their physical or network location, instead assuming a network has already been breached. |
| ● | Authentication and authorization required before access is granted. Authentication and authorization are discrete functions performed before any access to an enterprise resource is permitted. This applies to users, servers and devices. |
| ● | Minimal attack surface (principle of least privilege). All users, devices, and networks must only permit access to the minimal set of resources, and only for authenticated and authorized users. This applies to all users (remote and on-premises), all devices (enterprise-issued and BYOD), and all resource types (on-premises, cloud-based, physical, or virtual). |
| ● | Dynamic, identity-centric policies. The focus is on protecting specific resources (assets, services, workflows, network accounts, etc.), not broad network segments. Access policies dynamically evaluate user, device, network, and resource attributes to make decisions about whether access should be permitted at any given point in time. |
Deployment Architecture
The Appgate SDP deployment architecture is comprised of the following five elements.
| A. | Client. The user of a resource (described below). In the typical Appgate SDP use case, the client is an organization’s employee seeking to access an application from a PC or mobile device. |
| B. | Controller. Effectively the brain of the system, the controller houses the enterprise policy model (the rules used to determine which users should have access to which resources), aggregates the information required to enforce the enterprise policy model, and then makes an authentication and authorization decision. |
| | | |
| C. | Gateway. Policy enforcement points that restrict access to resources until a client is authorized. |
| | | |
| D. | Enterprise Systems. Sources of information about a user and context used to make authentication and authorization decisions. |
| | | |
| E. | Resource. Any application, server, network, IoT device, containerized workload, etc. that can be located in any cloud or on-premises environment. |
| | | |
A conceptional depiction and description of the Appgate SDP deployment architecture are as follows:
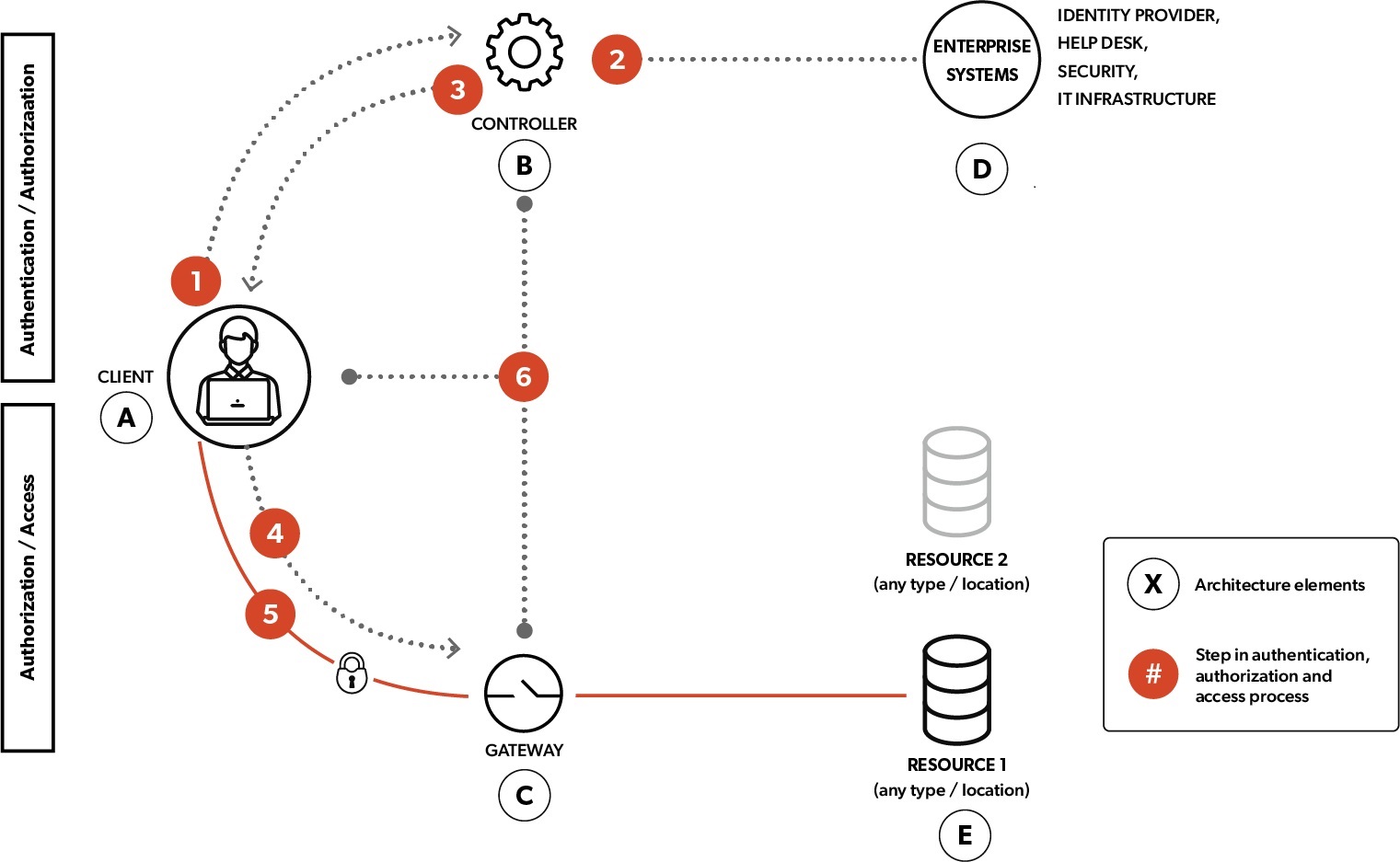
| 1. | The Client (or user) first connects to the Controller. |
| | | |
| 2. | The Controller begins by authenticating the user with the enterprise identity provided. It then aggregates all relevant data from the Enterprise Systems, including information about both a) the user’s identity, location, and device security posture and b) contextual information from the organization’s network, security, and business process systems. The Controller then uses this information to determine to which resources the user should have access at that particular time and place. |
| | | |
| 3. | The Controller generates and sends a live entitlement token to the user. An entitlement token is an electronic credential that indicates to which resources a user should have access. The entitlement token is “live” because it can change based on changes in context. |
| | | |
| 4. | The Client creates an encrypted tunnel to a Gateway and sends the live entitlement token to the Gateway for validation. |
| | | |
| 5. | The Gateway creates a logical “segment of one” to connect the Client to the specific resource(s) to which the Client has been granted access. |
| | | |
| 6. | The system continuously evaluates context and changes entitlements based on changes to context. |
Furthermore, the components of the Appgate SDP platform itself – the Controllers and Gateways – utilize a cryptographic mechanism to cloak themselves from unauthorized users. This mechanism is designed to ensure that these components can be accessed by legitimate users located anywhere, while remaining resilient and inaccessible to unauthorized use or malicious actors.
In addition, Appgate SDP’s architecture is designed to ensure that customers retain the ability to choose how and where their network traffic is routed (some customers use Appgate SDP as an SD-WAN replacement as a result), and how and where to deploy Gateways. Gateways are distributed across their organizations’ environments, protecting both on-premises and cloud-based environments. Similarly, the distributed nature of the Appgate SDP system provides a unified access control model for all users (both remote and on-premises) for all resources, using a single policy model and a single platform. As a result, customers benefit by being able to decommission ineffective siloed and legacy security technologies (such as VPNs and NACs), replacing them with a modern Zero Trust platform.
Deployment Options
Appgate SDP supports a wide variety of deployment models and access methods to ensure ongoing customer choice. Specifically, customers may choose to deploy entirely in a self-hosted and self-managed model, or they may utilize the Appgate-hosted cloud-based model, to take advantage of its simpler deployment and management. U.S. government entities can deploy via a FedRAMP Joint Authorization Board (JAB)-approved environment.
In addition to the many types of resources that need securing, organizations also have a wide variety of end-user populations and types, and the Appgate SDP platform provides an industry-leading set of access methods. Users can access Appgate SDP-protected resources via installed client software, through a clientless web portal, or through a network-based connector service. Likewise, Appgate SDP adeptly meets complex enterprise and government agency networking needs, including dynamic and policy-based control of network segmentation, routing, and name resolution. It delivers superior security while also improving the end user experience and reducing administrative burdens.
Digital Threat Protection
Our Digital Threat Protection (DTP) solution offers visibility and comprehensive fraud risk management to identify and eliminate attacks before they occur. DTP evaluates fraud risk across social media, phishing attacks, bogus websites, and malicious mobile apps. Its curated threat intelligence and continuous threat monitoring provides protection throughout the fraud risk lifecycle.
Additionally, it provides business leaders with valuable proactive detection, mitigation, and reporting functionality for their end-users. DTP helps combat external threats by detecting fraud risk lurking online, continuously monitoring brand-centric activity, and taking swift action to stop attacks before damage is done — often before intended victims are even aware. The DTP solution is deployed in Appgate’s cloud-hosted environment, ensuring that customers have a high degree of confidence in its availability and scalability. It is monitored and operated by our 24x7 Security Operations Center (SOC) team, who detect and respond to fraud risk events in near real-time.
DTP customers benefit from automated monitoring and manual follow-up, including threat analysis and verification, and initiation of malicious site takedowns. Specifically, the DTP service monitors customer websites, and detects phishing sites that have cloned legitimate ones. It also monitors newly registered domains, DNS entries, and posted links on social media sites, looking for similar domains that may be phishing sites. DTP also provides a unique and differentiated feature called Victim Insights, which through an encrypted key, identifies which users clicked on phishing sites and what credentials they entered, enabling rapid and precise responses. DTP also monitors mobile app stores, detecting rogue mobile apps designed to fool users.
DTP combines automated analysis of detected fraud attempts with skilled SOC operators who verify detected events and initiate takedown with relevant parties, including ISPs, registrars, and mobile app operators. The SOC also guides customers through recommended remediation steps within their enterprise systems.

Also, with the high volume of compromised information for sale across the Dark Web, DTP has an offering that provides peace of mind and reports risk exposure in detail. It defends against targeted threats by pinpointing exactly which employee credentials have been breached and are circulating across the Dark Web and mitigating the effects of targeted threats by reporting risk exposure to ensure quick action against exposed data.
Additionally, Appgate’s solution identifies and immobilizes sophisticated threats such as web injections and credential grabbing on transactional websites, without requiring software installed on the user’s device. It provides detection of unauthorized changes executed against the content of a company’s website, and built-in analytical systems in charge of evaluating users’ sessions to identify fraud indicators that will point out when cybercriminals have managed to get access to users’ accounts.
We facilitate all these services through our web-application online portal where our customers can see the results of our efforts. We create tickets in which the details of the alerting are provided, the credentials harvested, IP address and domain details given, along with the ability to request support directly to the SOC agents. Threat tracking maps and social media feeds are also provided if our customers want to peruse some of our raw data feeds.
Risk-Based Authentication
RBA combines advanced authentication techniques (such as multi-factor authentication) and behavioral analytics (based on machine learning / AI algorithms) used to model and monitor risk with dynamic and flexible rules to authorize transactions and prevent fraud for financial institutions. As a result, RBA enables financial institutions to detect and measure risky transactions more accurately, while reducing friction on end users.
Our RBA solution also enables customer choice of deployment options. RBA can be deployed wholly into customer environments for local integration, or into an Appgate-managed cloud environment for simpler deployment and management, as shown below.

We offer several authentication methods depending on our client’s customer friction and interaction preferences. RBA can provide authentication through push technologies, SMS text, One-Time-Passwords, email verification two-step responses, and QR code enrollment.
RBA utilizes a risk orchestration tool in our back end to allow for simplified integrations of multiple solutions, and to map conditional workflows to enable authentication challenges through device identification when fraud risk is determined within our transaction anomaly detection solution. Our behavioral biometrics and device analytics also provide a level of authentication and can tie into step-up authentication methods as required.
Our Customers
We serve over 600 customers globally including Fortune 500 enterprises, the U.S. Departments of Defense and Homeland Security, and large financial institutions. Although our solutions can help organizations regardless of industry, we serve many customers in the following industries: financial services, manufacturing, energy, media & entertainment, technology, telecommunications, consumer goods and services, and the public sector. We serve at least one of the top-five largest companies in the defense contracting, telecommunications, and oil and gas sectors. As of October 12, 2021, our customers independently ranked us 4.7/5.0 stars on Gartner Peer Insights, a peer-driven ratings and reviews platform for enterprise IT solutions and services covering over 300+ technology markets and 3,000 vendors. In addition to our strong overall customer ratings, another indicator of our strong customer relationships is our Customer Advisory Board, comprised of 13 of our most strategic customers who provide quarterly feedback on our solutions. This feedback, primarily received from technologists involved in the purchase, implementation, and ongoing management of Appgate solutions, helps drive our product innovations and validate our strategies. Our Customer Advisory Board members are also among our biggest advocates and frequently provide referrals to prospective customers. In the fiscal years ended in 2019, 2020, and the six months ended June 30, 2021, no customer contributed more than 10% of revenue.
Customer Case Studies
The customer examples below illustrate how customers from different industries benefit from Appgate’s solutions.
Chewy
Situation: Chewy’s mission is to be the most trusted and convenient online destination for pet parents (and partners) everywhere. The company believes that they are the preeminent online source for pet products, supplies, and prescriptions as a result of their broad selection of high-quality products, which they offer at competitive prices and deliver with an exceptional level of care and a personal touch. Chewy continually develops innovative ways for their customers to engage with them, and partner with approximately 2,500 of the best and most trusted brands in the pet industry, to bring a high-bar, customer-centric experience to their customers.
Solution: Chewy selected Appgate as its preferred partner due to both our high-quality software, as well as our agility and ability to scale with their rapidly growing business. During the onset of the COVID-19 pandemic, Chewy worked with Appgate to rapidly implement Appgate SDP to authenticate and authorize Chewy’s team members prior to allowing access to any resources from remote locations. After a successful initial deployment, Chewy chose Appgate SDP for its Zero Trust solution to enable secure and seamless work-from-anywhere in a post-COVID world.
Secureworks
Situation: Secureworks is a leading global cybersecurity firm that protects customer progress with cloud-native threat detection and response products focused on endpoint security. In 2017, Secureworks embarked upon a strategic Zero Trust journey to transform beyond a legacy perimeter-based approach to secure its own network. Secureworks needed to unlock constraints to productivity and innovation while providing secure, transparent and reliable access for team members around the world. While addressing internal needs was important, enabling precise, collaborative access for customers and partners was also a priority.
Solution: After evaluating dozens of vendors and performing a detailed, competitive evaluation, Secureworks selected Appgate as a key provider in its Zero Trust implementation. The initial use case was to replace an unreliable, unfriendly and underperforming global VPN infrastructure with secure, transparent access via Appgate. The results were immediate and transformational, with users demanding faster adoption as teams observed the benefits first-hand. The Appgate SDP implementation increased overall security, reduced business risk and helped transform Secureworks’ closed perimeter security model to a high performing, flexible Zero Trust architecture capable of supporting the dynamic nature of an intensely collaborative work environment. End user satisfaction improved dramatically as related helpdesk tickets dropped by 99%. Secureworks’ technology strategists note that Appgate SDP made it possible for the company to securely innovate at the rate desired by business, unconstrained by the inflexibility of legacy network access security solutions.
Sales
We sell our software and services through a combination of our direct sales team and channel partners. The direct team is composed of business development, inside sales and regional sales representatives responsible for uncovering business problems that can be solved using our solutions. They are supported by sales engineering and customer success specialists that gather customer requirements and design a solution to meet their requirements and vision. Sales engineering team members partner closely with the regional sales representatives to showcase the strength of our solutions and the problems that can be solved for our customers. Customer success members ensure that clients are receiving the full value from our security offerings. They manage the lifecycle of the relationship, from onboarding and implementation through ongoing advocacy. The team conducts formal business reviews with customers to identity and solve for new use cases, which supports our “land and expand” growth model. The direct sales team is organized by geography, enabling us to customize our interactions with prospects and customers.
Our Zero Trust solutions are highly complementary to other security products, and as such, we have built strategic go-to-market partnerships. Our products are easy to deploy and can be distributed by agents and resellers, service providers, systems integrators, cloud consulting partners, and original equipment manufacturers (OEMs). Appgate offers its partners a robust training and certification program to help them capitalize on the market opportunity, advance their technical skills and position them as a Zero Trust specialist. We expect our business through partners to continue to grow as we invest resources in developing a robust, partner-led go-to-market model. For example, we have strong relationships with Lumen, Optiv, Presidio, Guidepoint Security, DXC, TechMatrix, SageNet, Q2, Alkami, GBM, CLM, Kite, and Cybernet, among others, and work closely with federal systems integrators such as Raytheon, Northrop Grumman, and ManTech, who are building solutions around our products for wider distribution. We also work with technology alliance partners to devise leading, “better with” solutions.
Marketing
Our marketing strategy is designed to build brand awareness and reputation, establish ourselves as thought leaders and trusted advisors in Zero Trust security, drive customer demand globally through increasing prospect consideration and conversion, and provide our customers with meaningful ways to engage with us. We have a holistic approach that includes digital and non-digital methods, including: paid digital media, search engine optimization, social media, website marketing, events and sponsorships, live demos, media and analyst relations, speaker’s bureau, and account-based marketing programs. We also work with channel and technology partners on go-to-market activities that highlight the joint value of our solutions. We produce original content in the form of blogs, ebooks, infographics, videos, case studies, surveys, and white papers to help educate our target customers about top-of-mind security concerns. To see the value of our product in-action, prospects can attend regularly scheduled live demos or enroll in our Test Drive program for a hands-on experience. We believe an educated prospect makes the best decisions for their security program and we strive to help them in their journey.
Operations
We primarily utilize Microsoft and AWS cloud environments for our compute and storage needs required to deliver our products and services. Our infrastructure is designed to be highly resilient, have multiple levels of redundancy and provide failover across cloud infrastructures. Our software technology and operational approach, combined with the use of Microsoft and AWS resources, provide us with a distributed and scalable architecture on a global scale.
Professional Services
We provide professional services as part of our Threat Advisory Services. We also offer support installation and training related to our software solutions:
| ● | We offer Threat Advisory Services to help customers identify and defend against exploitable cybersecurity vulnerabilities. Our Threat Advisory Services engage a dedicated, highly pedigreed team of cybersecurity experts who use offensive tactics to simulate the behavior of real-world adversaries. Our team uses highly sophisticated, bespoke customized penetration testing methodologies, simulating nation-state-level and other complex attacks targeting our customers’ networks, applications, and third-party solution providers. These engagements help organizations test and validate their security investments and can lead to the implementation of our software solutions based on remediation recommendations, as we help our customers accelerate their Zero Trust journey. The Threat Advisory Services team utilizes information learned in their services engagements to inform our software product roadmap and future innovation, helping us more rapidly address our customers’ evolving security needs. |
| ● | As a part of our commitment to our customers’ success, we routinely offer professional services to help facilitate a smooth initial software deployment, in-line with industry standards. |
| ● | We also offer training services to teach customers best practices while using our software solutions. |
Research and Development
Our research and development organization is responsible for the design, development, quality, and testing of our software and service offerings. In addition, it is responsible for improving our features, functionality, and scalability, while ensuring our platform is available, reliable, and stable.
Security is at the heart of our business, and our teams of network engineers, software developers, data scientists, security architects, and anti-fraud specialists are passionate about helping our customers protect their environments. We work to continually improve and innovate, striving to offer high-quality, market-leading solutions. We work closely with our customers and partners, and by understanding their approaches and challenges, we gain insight into desired new capabilities and offerings that we can build to deliver value to the broader market. We also leverage key insights and capabilities from our products and services to inform and enhance other products and services in our portfolio.
We invest in and prioritize the quality of our offerings, utilizing both automated and manual testing and verification to ensure our products are functional, scalable, and secure. We regularly utilize both third-party and internal penetration testing experts to ensure our solutions are resilient to potential attacks, and work to continually improve them. We maintain a regular release cadence to deliver updates to our products, and our customer success team works to ensure that customers stay up to date on the latest versions.
Our research and development expenses were equal to approximately 28% of our revenue for the twelve months ended June 30, 2021. Our research and development teams are primarily located in the United States, Sweden, and Colombia. We plan to continue to dedicate significant and increasing resources to research and development.
Competition
The market for our solutions is competitive and characterized by evolving IT environments, customer requirements, industry standards, and frequent new product and service offerings and improvements. We compete with an array of established and emerging security solution vendors. Our competitors include the following by general category:
| ● | Large networking and security vendors such as Cisco Systems, Inc. and Palo Alto Networks, Inc. which offer security appliances and cloud services. |
| ● | Independent security vendors and providers such as Zscaler, Inc. and Netskope, Inc., who provide cloud-based security services. |
| ● | Cloud providers who include Zero Trust security offerings within their platforms, specifically Microsoft Corporation and Google LLC. |
| ● | Anti-Fraud and risk-based authentication providers such as Outseer (RSA Security LLC), Broadcom Inc. (which acquired CA Technologies), Guardian Analytics, Inc., and BioCatch Ltd. who provide advanced, actionable intelligence that allows organizations to secure their customers. |
| ● | Digital Threat protection providers such as RSA Security LLC, PhishLabs, Inc., and ZeroFox, Inc., who provide brand protection against digital attacks across multiple verticals. |
The principal competitive factors in the markets in which we operate include:
| ● | ability to prevent and detect security breaches; |
| ● | platform features, effectiveness and extensibility; |
| ● | ease of use to deploy, manage, and maintain; |
| ● | rapid development and delivery of new capabilities and services; |
| ● | strength of sales, marketing and channel partner relationships; |
| ● | quality of customer support; |
| ● | ability to integrate with other participants in the security and networking ecosystem; |
| ● | brand awareness, reputation and trust in the provider’s services; and |
| ● | time to value, price, and total cost of ownership. |
Although certain of our competitors enjoy greater brand awareness and resources, deeper customer relationships, and larger existing customer bases, we believe that we compete favorably with respect to the factors listed above and that we are well positioned as a leading provider of security solutions.
Intellectual Property
Our success depends in part upon our ability to protect and use our core technology and intellectual property rights. We rely on a combination of patents, copyrights, trademarks, trade secret laws, contractual provisions and confidentiality procedures to protect our intellectual property rights. As of June 30, 2021, we had over 78 total issued and pending patents, including in excess of 60 issued patents, in the United States and other countries. Our issued patents expire between 2033 and 2039 and cover various aspects of our solutions. In addition, we have registered “Appgate” as a trademark in the United States and other jurisdictions, and we have filed other trademark applications in the United States and other jurisdictions. We are also the registered holder of a variety of domestic domain names that include “Appgate” and similar variations. In addition to the protection provided by our intellectual property rights, we enter into confidentiality and invention assignment or similar agreements with our employees, consultants, and contractors. We further control the use of our proprietary technology and intellectual property rights through provisions in our subscription and license agreements. Despite our efforts to protect our trade secrets and proprietary rights through intellectual property rights, licenses and confidentiality agreements, unauthorized parties may still copy or otherwise obtain and use our software and technology. In addition to our internally developed technology, we also license software, including open source software, from third parties that we integrate into or bundle with our solutions.
Employees
We had 423 full-time employees worldwide as of June 30, 2021. We also engage temporary employees and contractors as needed to support our operations. To our knowledge, none of our employees are represented by a labor organization or are a party to any collective bargaining arrangement. We have not experienced any work stoppages and we consider our relations with our employees to be good.
Risk Factors
Risks Related to Our Business and Industry
Our relatively limited operating history makes it difficult to evaluate our current business and prospects and may increase the risk of an investment in us.
Our relatively limited operating history makes it difficult to evaluate our current business and prospects and plan for our future growth. We operated as a subsidiary of Cyxtera Technologies, Inc. (“Cyxtera”) until December 31, 2019, at which time Cyxtera spun out Legacy Appgate to become a standalone company. As a result, our business model has not been fully proven, which subjects us to a number of uncertainties, including our ability to plan for and model future growth. While we have continued to develop our solutions to incorporate multiple security and compliance functions into our software, we have encountered and will continue to encounter risks and uncertainties frequently experienced by rapidly growing companies in developing markets, including our ability to achieve broad market acceptance of our Zero Trust solutions, attract additional customers, grow partnerships, withstand increasing competition and manage increasing expenses as we continue to grow our business. If our assumptions regarding these risks and uncertainties are incorrect or change in response to changes in the market for network security solutions, our operating and financial results could differ materially from our expectations and our business could suffer.
We have a history of losses and may not be able to achieve or sustain profitability in the future.
We have incurred net losses in all periods since our inception, and we expect we will continue to incur net losses for the foreseeable future. We experienced net losses of $50.4 million and $230.5 million for the years ended December 31, 2020 and 2019, respectively. We had an accumulated deficit of $394.7 million as of June 30, 2021 and a net loss from continuing operations of $24.6 million for the six months ended June 30, 2021. Because the market for our products and services is rapidly evolving, it is difficult for us to predict the future results of our operations. Our growth efforts may prove more expensive than we currently anticipate, and we may not succeed in increasing our revenues sufficiently, or at all, to offset increasing expenses. In addition to the expected costs to grow our business, we also expect to incur significant additional legal, accounting and other expenses as a public company. Revenue growth may slow or revenue may decline for a number of possible reasons, including slowing demand for our products or services, increasing competition, a decrease in the growth of, or a demand shift in, our overall market, or a failure to capitalize on growth opportunities. Any failure to increase our revenue as we grow our business could prevent us from achieving or maintaining profitability or maintaining or increasing cash flow on a consistent basis. If we fail to increase our revenue to offset the increases in our operating expenses, we may not achieve or sustain profitability in the future.
We believe our long-term value as a company will be greater if we focus on growth, which may negatively impact our profitability in the near term.
Part of our business strategy is to primarily focus on our long-term growth. As a result, our profitability may be lower in the near term than it would be if our strategy were to maximize short-term profitability. Significant expenditures on sales and marketing efforts, and expenditures on growing our Zero Trust solutions and expanding our research and development, each of which we intend to continue to invest in, may not ultimately grow our business or cause long-term profitability. If we are ultimately unable to achieve profitability at the level anticipated by industry or financial analysts and our stockholders, our stock price may decline.
We face significant competition and could lose market share to our competitors, which could adversely affect our business, financial condition and results of operations.
The market for cybersecurity solutions is competitive and characterized by rapid changes in technology, customer requirements, industry standards and frequent introductions of new and improvements of existing products and services. Our business model of delivering security products through the Zero Trust model has not yet gained widespread market traction as the Zero Trust model is still an emerging solution. Moreover, we compete with many established network and cybersecurity vendors, as well as new entrants. As customer requirements evolve, and as new products, services and technologies are introduced, if we are unable to anticipate or effectively react to these competitive challenges, our competitive position could weaken, and we could experience a decline in revenue or our growth rate that could materially and adversely affect our business and results of operations.
Our competitors and potential competitors include:
| ● | independent security vendors and providers, such as Zscaler, Inc. and Netskope, Inc.; |
| ● | large networking and security vendors, such as Cisco Systems, Inc. and Palo Alto Networks, Inc.; |
| ● | cloud providers who include similar security offerings within their platforms, such as Microsoft Corporation and Google LLC; |
| ● | anti-fraud and risk-based authentication providers, such as Outseer (RSA Security LLC), Broadcom Inc. (which acquired CA Technologies), Guardian Analytics, Inc. and BioCatch Ltd.; |
| ● | digital threat protection providers such as Outseer (RSA Security LLC), PhishLabs, Inc. and ZeroFox, Inc.; and |
| ● | other providers of cybersecurity services that offer, or may leverage related technologies to introduce, products that compete with or are alternatives to our Zero Trust solutions. |
Many of our existing competitors have, and some of our potential competitors could have, substantial competitive advantages such as:
| ● | greater name recognition, longer operating histories and larger customer bases; |
| ● | larger sales and marketing budgets and resources; |
| ● | broader distribution and established relationships with channel partners and customers; |
| ● | greater customer support resources; |
| ● | greater resources to make acquisitions and enter into strategic partnerships; |
| ● | lower labor and research and development costs; |
| ● | larger and more mature intellectual property rights portfolios; and |
| ● | substantially greater financial, technical and other resources. |
In addition, our competitors may develop technology solutions with architectures similar to our products. Our larger competitors have substantially broader and more diverse product and services offerings, which may allow them to leverage their relationships based on other products or incorporate functionality into existing products to gain business in a manner that discourages users from purchasing our products or services, including through selling at zero or negative margins, offering concessions, bundling products or maintaining closed technology platforms. Many competitors that specialize in providing protection from a single type of security threat may be able to deliver these targeted security products to the market more quickly than we can or to convince organizations that these limited products meet their needs.
Conditions in our market could change rapidly and significantly as a result of technological advancements, partnering or acquisitions by our competitors or continuing market consolidation. Start-up companies that innovate and large competitors that are making significant investments in research and development may invent similar or superior products, services and technologies that compete with our Zero Trust and other solutions. Some of our current or potential competitors have made or could make acquisitions of businesses or establish cooperative relationships that may allow them to offer more directly competitive and comprehensive solutions than were previously offered and adapt more quickly to new technologies and customer needs. These competitive pressures in our market or our failure to compete effectively may result in price reductions, fewer orders, reduced revenue and gross margins, increased net losses and loss of market share. Any failure to meet and address these factors could materially harm our business and operating results.
Our operating results may fluctuate significantly, which could make our future results difficult to predict and could cause our operating results to fall below expectations.
Our operating results may fluctuate from quarter to quarter as a result of a number of factors, many of which are outside of our control and may be difficult to predict. Some of the factors that may cause our results of operations to fluctuate from quarter to quarter include:
| ● | broad market acceptance and the level of demand for our products and services; |
| ● | our ability to attract new customers, particularly large enterprises; |
| ● | our ability to retain customers and expand their usage of our Zero Trust solutions, particularly our largest customers; |
| ● | our ability to successfully expand internationally and penetrate key markets; |
| ● | the effectiveness of our sales and marketing programs; |
| ● | the length of our sales cycle, including the timing of renewals; |
| ● | technological changes and the timing and success of new service introductions by us or our competitors or any other change in the competitive landscape of our market; |
| ● | increases in and timing of operating expenses that we may incur to grow and expand our operations and to remain competitive; |
| ● | pricing pressure as a result of competition or otherwise; |
| ● | the quality and level of our execution of our business strategy and operating plan; |
| ● | adverse litigation judgments, settlements or other litigation-related costs; |
| ● | a possible downturn in cybersecurity spending due to a macroeconomic downturn; |
| ● | changes in the legislative or regulatory environment; and |
| ● | general economic conditions in either domestic or international markets, including geopolitical uncertainty and instability and global health crises and pandemics, such as COVID-19, and governmental responses thereto. |
In addition, we generally experience seasonality in terms of when we enter into agreements with customers. We typically enter into a higher percentage of agreements with new customers, as well as renewal agreements with existing customers, in the first and fourth quarters of our fiscal year. This seasonality is reflected to a much lesser extent, and sometimes is not immediately apparent, in revenue, due to the fact that we recognize subscription revenue with respect to term-based and perpetual licenses up-front, which is generally one to three years. We expect that seasonality will continue to affect our operating results in the future and may reduce our ability to predict cash flow and optimize the timing of our operating expenses.
Any one or more of the factors above may result in significant fluctuations in our results of operations. As a result, our historical operating results are not a reliable indicator of future performance.
Additionally, the variability and unpredictability of our quarterly results of operations or other operating metrics could result in our failure to meet our expectations or those of industry or financial analysts. If we fail to meet or exceed such expectations for these or any other reasons, the market price of our Common Stock could fall substantially.
Future acquisitions, strategic investments, partnerships or alliances could be difficult to identify and integrate, divert the attention of key management personnel, disrupt our business, dilute stockholder value and adversely affect our operating results, financial condition and prospects.
Our business strategy may, from time to time, include acquiring other complementary solutions, technologies or businesses. We have in the past acquired, and may in the future acquire, businesses that we believe will complement or augment our existing business. In order to expand our security offerings and features, we also may enter into relationships with other businesses, which could involve preferred or exclusive licenses, additional channels of distribution or investments in other companies. Negotiating these transactions can be time-consuming, difficult and costly, and our ability to close these transactions may be subject to third-party approvals, such as government regulatory approvals, which are beyond our control. Consequently, we cannot assure you that these transactions, once undertaken and announced, will close.
These kinds of acquisitions or investments may result in unforeseen operating difficulties and expenditures. In particular, we may encounter difficulties assimilating or integrating the businesses, technologies, products and services, personnel or operations of companies that we may acquire, particularly if the key personnel of an acquired business choose not to work for us. We may have difficulty retaining the customers of any acquired business or using or continuing the development of the acquired technologies. Acquisitions may also disrupt our ongoing business, divert our resources and require significant management attention that would otherwise be available for development of our business. We may not successfully evaluate or utilize the acquired technology or personnel, or accurately forecast the financial impact of an acquisition transaction, including accounting charges. Any acquisition or investment could expose us to unknown liabilities. Moreover, we cannot assure you that the anticipated benefits of any acquisition or investment would be realized or that we would not be exposed to unknown liabilities. In connection with these types of transactions, we may:
| ● | issue additional equity securities that would dilute our stockholders; |
| ● | use cash that we may need in the future to operate our business; |
| ● | incur debt on terms unfavorable to us or that we are unable to repay; |
| ● | incur large charges or substantial liabilities; |
| ● | encounter difficulties integrating diverse business cultures; |
| ● | become subject to adverse tax consequences, substantial depreciation or deferred compensation charges. |
These challenges related to acquisitions or investments could adversely affect our business, operating results, financial condition and prospects.
False positive or false negative detection of risk, application tampering, viruses, spyware, vulnerability exploits, data patterns, or URL categories could adversely affect our business.
Our risk level determinations of application integrity, web-injections, potential vulnerability exploits, data leaks, or phishing and pharming URL categories may falsely report and alert on fraud risk threats that do not actually exist or fail to detect legitimate threats. Appgate determines risk threats using classifiers, analyzers, and machine learning model features in our products, which attempt to identify indicators of fraud risk and other threats both based on known indicators and characteristics or unknown anomalies which indicate that a particular item may be a threat. Due to customer configurable risk and threat tolerance thresholds, our customers may perceive false positive detections or false negative missed detections as system unreliability, thereby adversely impacting market acceptance of our products. If our products are used by customers to restrict consumer access to applications based on falsely determining fraud risk, this could adversely affect end-customers’ user experience and result in damage to our reputation, negative publicity and decreased sales.
If our software does not interoperate with our customers’ network and security infrastructure or with third-party products, websites or services, our products may become less competitive and our results of operations may be harmed.
Our products and services must interoperate with our customers’ existing network and security infrastructure. These complex systems are developed, delivered and maintained by the customer and a myriad of vendors and service providers. As a result, the components of our customers’ infrastructure have different specifications, rapidly evolve, utilize multiple protocol standards, include multiple versions and generations of products and may be highly customized. We must be able to interoperate and provide our security products and services to customers with highly complex and customized networks, which requires careful planning and execution between our customers, our customer support teams and our channel partners. Further, when new or updated elements of our customers’ infrastructure or new industry standards or protocols are introduced, we may have to update or enhance our software to allow us to continue to provide service to customers. Any changes in such technologies that degrade the functionality of our products or give preferential treatment to competitive services could adversely affect adoption and usage of our products and services. Our competitors or other vendors may refuse to work with us to allow their products to interoperate with our solutions, which could make it difficult for our software to function properly in customer networks that include these third-party products.
We may not deliver or maintain interoperability quickly or cost-effectively, or at all. These efforts require capital investment and engineering resources. If we fail to maintain compatibility of our products and services with our customers’ network and security infrastructures, our customers may not be able to fully utilize our solutions, and we may, among other consequences, lose or fail to increase our market share and experience reduced demand for our services, which would materially harm our business, operating results and financial condition.
If we fail to develop or introduce new enhancements to our products on a timely basis, our ability to attract and retain customers, remain competitive and grow our business could be impaired. Our current research and development efforts may not produce successful products that result in significant revenue, cost savings or other benefits in the near future, if at all.
The industry in which we compete is characterized by rapid technological change, frequent introductions of new products and services, evolving industry standards and changing regulations, as well as changing customer security needs, technology requirements and preferences. Our ability to attract new customers and increase revenue from existing customers will depend in significant part on our ability to anticipate and respond effectively to these changes on a timely basis and continue to introduce enhancements to our products and services.
The success of our products depends on our continued investment in our research and development organization to increase the functionality, reliability, availability and scalability of our existing solutions. Our investments in research and development may not result in significant design improvements, marketable products, subscriptions, or features, or may result in products or services that are more expensive than anticipated. Additionally, we may not achieve the cost savings or the anticipated performance improvements we expect, and we may take longer to generate revenue, or generate less revenue, than we anticipate. Our future plans include significant investments in research and development and related product and service opportunities. We believe that we must continue to dedicate a significant amount of resources to our research and development efforts to maintain our competitive position. However, we may not receive significant revenue from these investments in the near future, if at all, or these investments may not yield the expected benefits, either of which could adversely affect our business and operating results.
The success of any enhancement depends on several factors, including the timely completion and market acceptance of the enhancement. Any new product or service that we develop might not be introduced in a timely or cost-effective manner and might not achieve the broad market acceptance necessary to generate significant revenue. If new technologies emerge that deliver competitive products and services at lower prices, more efficiently, more conveniently or more securely, these technologies could adversely impact our ability to compete effectively. Any delay or failure in the introduction of enhancements could materially harm our business, results of operations and financial condition.
If we are not able to maintain and enhance our brand, our business and results of operations may be adversely affected.
We believe that maintaining and enhancing our reputation as a provider of high-quality cybersecurity solutions is critical to our relationship with our existing customers and channel partners and our ability to attract new customers and channel partners. Furthermore, we believe that the importance of brand recognition will increase as competition in our market increases. The successful promotion of our brand will depend on several factors, including our marketing efforts, our ability to continue to develop high-quality features and enhancements for our technology solutions and our ability to successfully differentiate our solutions from competitive products and services. Our brand promotion activities may not be successful or yield increased revenue. In addition, independent industry or financial analysts often provide reviews of our products and services, as well as products and services of our competitors, and perception of our Zero Trust solutions in the marketplace may be significantly influenced by these reviews. If these reviews are negative, or less positive as compared to those of our competitors’ products and services, our brand may be adversely affected. In addition, we have been named as a “Leader” in the Forrester New Wave™ for Zero Trust Network Access (Q3 2021) report. Our failure to maintain our “Leader” status in the future may also adversely affect our brand. Additionally, the performance of our channel partners may affect our brand and reputation if customers do not have a positive experience with our channel partners’ services. The promotion of our brand requires us to make substantial expenditures, and we anticipate that the expenditures will increase as our market becomes more competitive, we expand into new markets and more sales are generated through our channel partners. To the extent that these activities yield increased revenue, this revenue may not offset the increased expenses we incur. If we do not successfully maintain and enhance our brand, our business may not grow, we may have reduced pricing power relative to competitors and we could lose customers or fail to attract potential customers, all of which would materially and adversely affect our business, results of operations and financial condition.
Our business and growth partially depend on the success of our relationships with our existing channel partners and adding new channel partners over time.
We currently derive a portion of our revenue from sales through our channel partner network, and we expect future revenue growth will also be driven through this network. Not only does our joint sales approach require additional investment to grow and train our sales force, but we believe that continued growth in our business is dependent upon identifying, developing and maintaining strategic relationships with our existing and potential channel partners, including global systems integrators and managed service providers that will in turn drive substantial revenue and provide additional value-added services to our customers. Our channel partners’ operations may also be negatively impacted by other effects the COVID-19 pandemic is having on the global economy, such as increased credit risk of end customers and the uncertain credit markets. Our agreements with our channel partners are generally non-exclusive, meaning our channel partners may offer customers the products of several different companies, including products that compete with our technology solutions. In general, our channel partners may also cease marketing or reselling our products and services with limited or no notice and without penalty. If our channel partners do not effectively market and sell subscriptions to our products and services, choose to promote our competitors’ products or fail to meet the needs of our customers, our ability to grow our business and sell subscriptions to our products and services may be adversely affected. In addition, our channel partner structure could subject us to lawsuits or reputational harm if, for example, a channel partner misrepresents the functionality of our products and services to customers or violates applicable laws or our corporate policies. Our ability to achieve revenue growth in the future will depend in large part on our success in maintaining successful relationships with our channel partners, identifying additional channel partners and training our channel partners to independently sell and deploy our products and services. If we are unable to maintain our relationships with our existing channel partners or develop successful relationships with new channel partners or if our channel partners fail to perform, our business, financial position and results of operations could be materially and adversely affected.
Our business depends, in part, on sales to government organizations, and significant changes in the contracting or fiscal policies of such government organizations could have an adverse effect on our business and operating results.
Our future growth depends, in part, on increasing sales to government organizations. Demand from government organizations is often unpredictable, subject to budgetary uncertainty and typically involves long sales cycles. We have made significant investments to address the government sector, but we cannot assure you that these investments will be successful, or that we will be able to maintain or grow our revenue from the government sector. Although we anticipate that they may increase in the future, sales to governmental organizations have not accounted for, and may never account for, a significant portion of our revenue. Sales to governmental organizations are subject to a number of challenges and risks that may adversely impact our business. Sales to such government entities include the following risks:
| ● | selling to governmental agencies can be highly competitive, expensive and time consuming, often requiring significant upfront time and expense without any assurance that such efforts will generate a sale; |
| | | |
| ● | government certification requirements applicable to our solutions may change and, in doing so, restrict our ability to sell into the governmental sector until we have attained the revised certification; |
| | | |
| ● | government demand and payment for our solutions may be impacted by public sector budgetary cycles and funding authorizations, with funding reductions or delays adversely affecting public sector demand for our solutions; |
| | | |
| ● | governments routinely investigate and audit government contractors’ administrative processes, and any unfavorable audit could result in the government refusing to continue buying our solutions, which would adversely impact our revenue and operating results, or institute fines or civil or criminal liability if the audit were to uncover improper or illegal activities; and |
| | | |
| ● | governments may require certain products to be manufactured, produced, hosted or accessed solely in their country or in other relatively high-cost locations, and we may not produce or host all products in locations that meet these requirements, affecting our ability to sell these products to governmental agencies. |
The occurrence of any of the foregoing could cause governmental organizations to delay or refrain from purchasing our solutions in the future or otherwise have an adverse effect on our business, operating results and financial condition.
Our international operations expose us to risks, and failure to manage those risks could materially and adversely impact our business.
Historically, we have derived a significant portion of our revenue from outside the United States. For the year ended December 31, 2020 and six-month period ended June 30, 2021, we derived approximately 52% and 56%, respectively, of our revenue from our international customers. As of June 30, 2021, approximately 59.5% of our full-time employees were located outside of the United States. We are continuing to adapt to and develop strategies to address international markets and our growth strategy includes expansion into target geographies, such as the Middle East, Africa, Japan and the Asia-Pacific regions, but there is no guarantee that such efforts will be successful. We expect that our international activities will continue to grow in the future, as we continue to pursue opportunities in international markets. These international operations will require significant management attention and financial resources and are subject to substantial risks, including:
| ● | political, economic and social uncertainty; |
| ● | unexpected costs for the localization of our services, including translation into foreign languages and adaptation for local practices and regulatory requirements; |
| ● | greater difficulty in enforcing contracts and accounts receivable collection, and longer collection periods, which may be further lengthened by the COVID-19 pandemic and governmental responses thereto; |
| ● | reduced or uncertain protection for intellectual property rights in some countries; |
| ● | greater risk of unexpected changes in regulatory practices, tariffs and tax laws and treaties; |
| ● | greater risk of a failure of foreign employees, partners, distributors and resellers to comply with both U.S. and foreign laws, including antitrust regulations, anti-bribery laws, export and import control laws, and any applicable trade regulations ensuring fair trade practices; |
| ● | requirements to comply with foreign privacy, data protection and information security laws and regulations and the risks and costs of noncompliance; |
| ● | increased expenses incurred in establishing and maintaining office space and equipment for our international operations; |
| ● | greater difficulty in identifying, attracting and retaining local qualified personnel, and the costs and expenses associated with such activities; |
| ● | differing employment practices and labor relations issues; |
| ● | difficulties in managing and staffing international offices and increased travel, infrastructure and legal compliance costs associated with multiple international locations, which has been made more difficult by our inability to travel to certain international offices due to COVID-19; and |
| ● | fluctuations in exchange rates between the U.S. dollar and foreign currencies in markets where we do business, including but not limited to, the British Pound and Euro, and related impact on sales cycles. |
Following a referendum in June 2016 in which voters in the United Kingdom approved an exit from the EU, the government of the United Kingdom initiated a process to leave the EU (often referred to as “Brexit”) without an agreement in place. This has led to legal uncertainty in the region and could adversely affect the tax, operational, legal and regulatory regimes to which our business is subject. In addition, any continued or further uncertainty, weakness or deterioration in global macroeconomic and market conditions may cause our UK or EU customers to modify spending priorities or delay purchasing decisions, and may result in lengthened sales cycles, any of which could harm our business and operating results.
As we continue to develop and grow our business globally, our success will depend, in part, on our ability to anticipate and effectively manage these risks. The expansion of our existing international operations and entry into additional international markets will require management attention and financial resources. Our failure to successfully manage our international operations and the associated risks could limit the future growth of our business.
We have grown rapidly in recent periods. If we fail to effectively manage our growth, our business, financial condition and results of operations would be harmed.
Our growth may place a significant strain on our management and our administrative, operational and financial infrastructure. Our organizational structure is becoming more complex as we improve our administrative, operational and financial infrastructure as well as our reporting systems and procedures. Our success will depend in part on our ability to manage this growth effectively, which will require that we continue to improve our administrative, operational, financial and management systems and controls by, among other things:
| ● | effectively attracting, training and integrating, including collaborating with, a large number of new employees; |
| ● | further improving our key business applications, processes and security and IT infrastructure to support our business needs; |
| ● | enhancing our information and communication systems to ensure that our employees and offices around the world are well coordinated and can effectively communicate with each other and our growing base of channel partners, customers and users; and |
| ● | appropriately documenting and testing our security and IT systems and business processes. |
These and other improvements in our systems and controls may require significant capital expenditures and the allocation of management and employee resources. If we fail to implement these improvements effectively, our ability to manage our expected growth, ensure uninterrupted operation of our software and key business systems and comply with the rules and regulations applicable to public companies could be impaired, the quality of our products and services could suffer and we may not be able to adequately address competitive challenges. Failure to manage any future growth effectively could result in increased costs, disrupt our existing customer relationships, reduce demand for or limit us to smaller deployments of our products and services, or harm our business performance and operating results.
In addition, as we expand our business, it is important that we continue to maintain a high level of customer service and satisfaction. As our customer base continues to grow, we will need to expand our account management, customer service and other personnel to provide personalized account management and customer service. If we are not able to continue to provide high levels of customer service, our reputation, as well as our business, results of operations and financial condition, could be harmed.
In addition, we believe that our corporate culture has been a contributor to our success, which we believe fosters innovation, teamwork and an emphasis on customer-focused results. We also believe that our culture creates an environment that drives and perpetuates our strategy and cost-effective distribution approach. As we grow and develop the infrastructure of a public company, we may find it difficult to maintain our corporate culture. Any failure to preserve our culture could harm our future success, including our ability to retain and recruit personnel, innovate and operate effectively and execute on our business strategy. If we experience any of these effects in connection with future growth, it could materially impair our ability to attract new customers, retain existing customers and expand their use of our Zero Trust solutions, all of which would materially and adversely affect our business, financial condition and results of operations.
Our sales cycles can be long and unpredictable, and our sales efforts can require considerable time and expense.
The timing of our sales and related revenue recognition is difficult to predict because of the length and unpredictability of the sales cycle for our products and services, particularly with respect to large organizations. Our sales efforts typically involve educating our prospective customers about the uses, benefits and the value proposition of our products and services, and often include a detailed Proof of Concept (POC) deployment in the prospect’s environment. Customers often view the subscription to our products as a significant decision as part of a strategic transformation initiative and, as a result, frequently require considerable time to evaluate, test and qualify our Zero Trust solutions prior to entering into or expanding a relationship with us. Large enterprises and government entities in particular often undertake a significant evaluation process that further lengthens the sales cycle. The ongoing COVID-19 pandemic may further extend sales cycles for some of our products and services.
Our sales force develops relationships directly with our customers, and together with our channel account teams, works with our channel partners on account penetration, account coordination, sales and overall market development. We spend substantial time and resources on our sales efforts, especially with larger customers, without any assurance that our efforts will produce a sale. Product purchases are frequently subject to budget constraints, multiple approvals and unanticipated administrative, processing and other delays. As a result, it is difficult to predict whether and when a sale will be completed and when revenue from a sale will be recognized.
The failure of our efforts to secure sales after investing resources in a lengthy sales process could materially and adversely affect our business and operating results.
The sales prices of our solutions may decrease, or the mix of our sales may change, which may reduce our gross profits and adversely impact our financial results.
We have limited experience with respect to determining the optimal prices for our solutions. As the market for our solutions matures, or as new competitors introduce new products or services that are similar to or compete with ours, we may be unable to attract new customers at the same price or based on the same pricing model as we have used historically. Further, competition continues to increase in the market segments in which we participate, and we expect competition to further increase in the future, thereby leading to increased pricing pressures. Larger competitors with more diverse product and service offerings may reduce the price of products or services that compete with ours or may bundle them with other products and services. This could lead customers to demand greater price concessions or additional functionality at the same price levels. As a result, in the future we may be required to reduce our prices or provide more features without corresponding increases in price, which would adversely affect our business, operating results, and financial condition.
The impact of the ongoing COVID-19 pandemic, including the resulting global economic uncertainty, is fluid, very unclear and difficult to predict at this time, but it may have a material adverse impact on our business, results of operations, financial condition, liquidity and cash flows.
The COVID-19 pandemic has caused general business disruption worldwide beginning in January 2020. The full extent to which the COVID-19 pandemic will directly or indirectly impact our business, operating results, cash flows, and financial condition will depend on future developments that are highly uncertain and cannot be accurately predicted.
However, as economic activity has been recovering, the impact of the COVID-19 pandemic on our business has been more reflective of greater economic and marketplace dynamics, which include minimal supply chain disruptions, rather than pandemic-related issues such as mandated restrictions and employee illness. Notwithstanding the recent resurgence of economic activity, in light of variant strains of the virus that have emerged, the COVID-19 pandemic could once again impact our operations and the operations of our customers and suppliers as a result of quarantines, location closures, illnesses, and travel restrictions. We do not yet know the full extent of potential impacts on our business, operations or on the global economy as a whole, particularly if the COVID-19 pandemic continues and persists for an extended period of time. Potential impacts include:
| ● | our customer prospects and our existing customers may experience slowdowns in their businesses, which in turn may result in reduced demand for our solutions, lengthening of sales cycles, loss of customers, and difficulties in collections; |
| ● | we continue to incur fixed costs, particularly for certain real estate office leases, and are deriving reduced benefit from those costs; |
| ● | we may be subject to legal liability for safe workplace claims; |
| ● | our critical vendors could go out of business; |
| ● | substantially all of our in-person marketing events, including conferences, have been canceled and we may continue to experience prolonged delays in our ability to reschedule or conduct in-person events and other related activities; and |
| ● | our marketing, sales, and support organizations are accustomed to extensive face-to-face customer and partner interactions, and our ability to conduct business remotely is largely unproven. |
Any of the foregoing could adversely affect our business, financial condition, and operating results.
While we have not to date experienced a significant impact to our business, operations or financial results as a result of the COVID-19 pandemic, there can be no assurance that these events will not have a material adverse impact on our business, operations or financial results in subsequent quarters or years.
We provide service level commitments under some of our customer contracts. If we fail to meet these contractual commitments, we could be obligated to provide credits for future service and our business could suffer.
Certain of our customer agreements contain service level commitments, which contain specifications regarding the availability and performance of our products and services. Any failure of or disruption to our infrastructure could impact the performance of our products and the availability of services to customers. If we are unable to meet our stated service level commitments or if we suffer extended periods of poor performance or unavailability of our products, we may be contractually obligated to provide affected customers with service credits for future subscriptions, and, in certain cases, refunds. To date, there has not been a material failure to meet our service level commitments, and we do not currently have any material liabilities accrued on our balance sheet for such commitments. Our revenue, other results of operations and financial condition could be harmed if we suffer performance issues or downtime that exceeds the service level commitments under our agreements with our customers.
Our business is subject to the risks of warranty claims, product returns and product defects from real or perceived defects in our solutions or their misuse by our customers or third parties and indemnity provisions in various agreements potentially expose us to substantial liability for intellectual property infringement and other losses.
We may be subject to liability claims for damages related to errors or defects in our solutions. A material liability claim or other occurrence that harms our reputation or decreases market acceptance of our solutions will harm our business and operating results. Although we generally have limitation of liability provisions in our terms and conditions of sale, they may not fully or effectively protect us from claims as a result of federal, state or local laws or ordinances, or unfavorable judicial decisions in the United States or other countries. The sale and support of our solutions also entails the risk of product liability claims.
Additionally, we typically provide indemnification to customers for certain losses suffered or expenses incurred as a result of third-party claims arising from our infringement of a third party’s intellectual property. We also provide unlimited liability for certain breaches of confidentiality, as defined in our terms of service. We also provide limited liability in the event of certain breaches of our terms of service. Certain of these contractual provisions survive termination or expiration of the applicable agreement.
If our customers or other third parties we do business with make intellectual property rights or other indemnification claims against us, we will incur significant legal expenses and may have to pay damages, license fees and/or stop using technology found to be in violation of the third party’s rights. We may also have to seek a license for the technology. Such license may not be available on reasonable terms, if at all, and may significantly increase our operating expenses or may require us to restrict our business activities and limit our ability to deliver certain solutions or features. We may also be required to develop alternative non-infringing technology, which could require significant effort and expense and/or cause us to alter our solutions, which could harm our business. Large indemnity obligations, whether for intellectual property or in certain limited circumstances, other claims, would harm our business, operating results and financial condition.
Additionally, our solutions may be used by our customers and other third parties who obtain access to our solutions for purposes other than for which our solutions were intended.
Under certain circumstances our employees may have access to our customers’ solutions. An employee may take advantage of such access to conduct malicious activities. Any such misuse of our solutions could result in negative press coverage and negatively affect our reputation, which could result in harm to our business, reputation and operating results.
We maintain insurance to protect against certain claims associated with the use of our solutions, but our insurance coverage may not adequately cover any claim asserted against us. In addition, even claims that ultimately are unsuccessful could result in our expenditure of funds in litigation, divert management’s time and other resources, and harm our business and reputation.
If organizations do not adopt a Zero Trust model for cybersecurity, our ability to grow our business and operating results may be adversely affected.
Cybersecurity technologies are still evolving, and it is difficult to precisely predict customer demand and adoption rates for our services generally. We believe that our Zero Trust model for cybersecurity offers superior protection to our customers, who are becoming increasingly aware of the importance of implementing cybersecurity measures beyond a perimeter-centric model to secure access to their network. Following the 2020 SolarWinds attack, guidance was released by the National Institute of Standards and Technology, the National Security Agency, and the Cybersecurity and Infrastructure Security Agency recommending a Zero Trust security approach. Additionally, on May 12, 2021, President Joe Biden issued an Executive Order explicitly calling for the adoption of a Zero Trust Architecture to improve the nation’s response to “persistent and increasingly sophisticated malicious cyber campaigns that threaten the public sector, the private sector, and ultimately the American people’s security and privacy.” The federal government continues to lead the industry in setting standards with the September 2021 release of a Zero Trust maturity model and Zero Trust strategy documents. We also believe that our products and services represent a major shift from perimeter-centric cybersecurity models.
However, traditional perimeter-centric cybersecurity models are entrenched in the infrastructure of many of our potential customers, particularly large enterprises, because of their prior investment in and the familiarity of their IT personnel with such cybersecurity solutions. As a result, our sales process often involves extensive efforts to educate our customers on the benefits and capabilities of Zero Trust solutions, particularly as we continue to pursue customer relationships with large organizations. Even with these efforts, we cannot predict market acceptance of our products and services, or the development of competing products or services based on other technologies. If we fail to achieve market acceptance of our products and services or are unable to keep pace with industry changes, our ability to grow our business and our operating results will be materially and adversely affected.
If we are unable to attract new customers or if our existing customers do not renew their subscriptions for our services or add additional users and services to their subscriptions the future results of our operations could be harmed.
Our growth is substantially dependent on adding new customers and expanding our relationships with existing customers. Potential clients that use legacy products and services may believe that these products and services are sufficient to meet their security needs or that our offerings only serve the needs of a portion of the enterprise security market. Accordingly, these organizations may continue allocating their information technology budgets for legacy products and services and may not adopt our security offerings. Further, many organizations have invested substantial personnel and financial resources to design and operate their networks and have established deep relationships with other providers of networking and security products. As a result, these organizations may prefer to purchase from their existing suppliers rather than add or switch to a new supplier such as us regardless of product performance, features, or greater services offerings. They may also be more willing to incrementally add solutions to their existing security infrastructure from existing suppliers rather than to replace some or all of their existing security infrastructure with our solutions. In addition, numerous other factors, many of which are out of our control, may now or in the future impact our ability to add new customers, including our failure to expand, retain and motivate our sales and marketing personnel, our failure to develop or expand relationships with our channel partners or to attract new channel partners, failure by us to help our customers to successfully deploy our software and expertise, negative media or industry or financial analyst commentary regarding us or our solutions, litigation and deteriorating general economic conditions, including as a result of the COVID-19 pandemic. Our success in attracting new customers also depends on our ability to develop innovative, high-quality, and appealing new products, including alternatives to products introduced by our competitors, and to effectively communicate and market the benefits of such new products. Our ability to attract new customers also depends on the effectiveness of our sales and marketing efforts. We plan to dedicate significant resources to sales and marketing programs and to expand our sales and marketing capabilities to target additional potential customers, but there is no guarantee that we will be successful in attracting and maintaining additional customers. Furthermore, our ability to achieve growth will partially depend on our success in hiring, integrating, training and retaining a sufficient number of sales personnel to support our growth. If we are unable to find efficient ways to deploy our sales and marketing programs, are unable to hire and train a sufficient number of effective sales personnel, or our efforts to attract new customers are not successful, our revenue and rate of revenue growth may decline, we may not achieve profitability and the future results of our operations could be materially harmed.
Our growth is also partially dependent on our customers renewing their subscriptions for our products when existing contract terms expire and expanding our commercial relationships with our existing customers. Our customers have no obligation to renew their subscriptions for our services after the expiration of their contractual subscription period, which is typically one to three years, and in the normal course of business, some customers have elected not to renew. In addition, in certain cases, customers may cancel their subscriptions without cause either at any time or upon advance written notice (typically ranging from 30 days to 60 days), typically subject to an early termination penalty for unused services. In addition, our customers may renew for fewer users, renew for shorter contract lengths or switch to a lower-cost suite. If our customers do not renew their subscription services, if our revenues decline or if we fail to grow our business, we could incur impairment losses on our assets. Our customer retention and expansion may decline or fluctuate as a result of a number of factors, including our customers’ satisfaction with our services, our customers’ ability to adopt our solutions correctly, our prices and pricing plans, our customers’ spending levels, decreases in the number of users to which our customers deploy our solutions, mergers and acquisitions involving our customers, competition and deteriorating general economic conditions.
Our future success also depends in part on the rate at which our current customers add additional users to their subscriptions or expand to utilize additional products, which is driven by a number of factors, including customer satisfaction with our services, customer security and networking issues and requirements, including demand for our products and services, general economic conditions and customer reaction to the price per additional user or of additional services. If our efforts to expand our relationship with our existing customers are not successful, our business may materially suffer.
Our business is subject to the risks of hurricanes, earthquakes, fire, floods and other natural catastrophic events, and to interruption by man-made problems such as power disruptions, computer viruses, data security breaches or terrorism effecting our operations or the operations of our third-party cloud service providers.
Our success depends, in part, on our ability to maintain the integrity of our systems and infrastructure, including website, information and related systems. We also currently host some of our products and serve our customers from third-party cloud service providers. While we have electronic access to the components and infrastructure of our software that are hosted by these third parties, we do not control the operation of these environments. Consequently, we may be subject to service disruptions as well as failures to provide adequate support for reasons that are outside of our direct control. Our corporate headquarters are located in Coral Gables, FL, a region known for hurricane activity. A significant natural disaster, such as a hurricane, fire, flood or public health emergency, such as COVID-19, or a significant man-made problem, such as acts of terrorism and other geopolitical unrest, occurring at our headquarters, at one of our other facilities or where a key channel partner, data center or third-party cloud service provider, component supplier or other third-party provider is located, could adversely affect our business, results of operations and financial condition. Although we maintain incident management and disaster response plans, disaster recovery planning by its nature cannot be sufficient for all eventualities. Though it is difficult to determine what, if any, harm may directly result from any specific interruption or attack, any failure to maintain performance, reliability, security and availability of our products and services to the satisfaction of our users may materially harm our reputation and our ability to retain existing customers and attract new customers.
If the delivery of our services to our customers is interrupted or delayed for any reason, our business could suffer.
Any interruption or delay in the delivery of our services may negatively impact our customers. Certain of our products are deployed via the internet, and our customers’ access to network resources is dependent on the continuous availability of the internet and our services to utilize such products. If an interruption in our services were to occur, our customers’ users could lose access to network resources (including private on-premises resources, public cloud IaaS-deployed resources, or public cloud SaaS resources, depending on customer configuration) until such disruption is resolved or customers deploy disaster recovery options that allow them to remediate the problem. The adverse effects of any service interruptions on our reputation and financial condition may be disproportionately heightened due to the nature of our business and the fact that our customers expect continuous and uninterrupted access to resources and may have a low tolerance for interruptions of any duration. While we do not consider them to have been material, we have experienced, and may in the future experience, service disruptions and other performance problems due to a variety of factors.
The following factors, many of which are beyond our control, can affect the delivery and availability of our services and the performance of our products:
| ● | the development and maintenance of the infrastructure of the internet; |
| ● | the performance and availability of cloud service providers or third-party telecommunications services with the necessary speed, data capacity and security for providing reliable internet access and services; |
| ● | decisions by the owners and operators of the cloud infrastructures or data centers where our infrastructure is deployed to terminate our contracts, discontinue services to us, shut down operations or facilities, increase prices, change service levels, limit bandwidth, declare bankruptcy or prioritize the traffic of other parties; |
| ● | the occurrence of earthquakes, floods, fires, pandemics, power loss, system failures, physical or electronic break-ins, acts of war or terrorism, human error or interference (including by disgruntled employees, former employees or contractors) and other catastrophic events; |
| ● | cyberattacks, including ransomware, denial of service attacks, targeted at us, our cloud service providers, data centers or the infrastructure of the internet; |
| ● | failure by us to maintain and update our infrastructure to meet customer requirements; |
| ● | errors, defects or performance problems in our software, including third-party software incorporated in our software, which we use to operate our products; |
| ● | improper classification of websites or known-bad phishing domains by our vendors who provide us with lists of malicious sites; |
| ● | improper deployment or configuration of our services; |
| ● | the failure of our redundancy systems, in the event of a service disruption at one of our cloud service providers, to provide failover to other regions in our cloud service provider environment network; and |
| ● | the failure of our disaster recovery and business continuity arrangements. |
The occurrence of any of these factors, or if we are unable to efficiently and cost-effectively fix such errors or other problems that may be identified, could damage our reputation, negatively impact our relationship with our customers or otherwise materially harm our business, results of operations and financial condition.
A network or data security incident against us, whether actual, alleged, or perceived, could harm our reputation, create liability, and regulatory exposure, and adversely impact our business, operating results, and financial condition.
Increasingly, companies are subject to a wide variety of attacks on their networks on an ongoing basis, including traditional computer hackers, malicious code (such as viruses and worms), distributed denial-of-service attacks, sophisticated attacks conducted or sponsored by nation-states, advanced persistent threat intrusions, ransomware, software supply chain attacks, and theft or misuse of intellectual property or business or personal data, including by disgruntled employees, former employees or contractors. Cybersecurity companies face particularly intense attack efforts, and we have faced and will continue to face cyber threats and attacks from a variety of sources. Although we have implemented security measures to prevent such attacks, our networks and systems may be breached due to the actions of outside parties, employee error, malfeasance, a combination of these, or otherwise, and as a result, an unauthorized party may obtain access to our systems, networks, or data. We may face difficulties or delays in identifying or otherwise responding to any attacks or actual or potential security breaches or threats. A breach in our data security or an attack against our platform could impact our networks or the networks of our customers that are secured by our platform, creating system disruptions or slowdowns and providing access to malicious parties to information stored on our networks or the networks of our customers, resulting in data being publicly disclosed, altered, lost, or stolen, which could subject us to liability and adversely impact our financial condition.
In addition, any actual, alleged or perceived security breach in our systems or networks, or any other actual, alleged or perceived data security incident we suffer, could result in damage to our reputation, negative publicity, loss of customers and sales, loss of competitive advantages over our competitors, increased costs to remedy any problems and otherwise respond to any incident, regulatory investigations and enforcement actions, costly litigation, and other liability. We would also be exposed to a risk of loss or litigation and potential liability under laws, regulations and contracts that protect the privacy and security of personal information.
In addition, we may incur significant financial and operational costs to investigate, remediate, eliminate and put in place additional tools and devices designed to prevent actual or perceived security breaches and other security incidents, as well as costs to comply with any notification obligations resulting from any security incidents. Any of these negative outcomes could adversely impact the market perception of our platform and customer and investor confidence in our company, and would adversely impact our business, operating results, and financial condition.
The actual or perceived failure of our technology solutions to prevent a security breach or address targeted security threats could harm our reputation and adversely impact our business, financial condition and results of operations.
Our Zero Trust solutions may fail to prevent security breaches for any number of reasons. Our products are complex and may be misconfigured by customers or contain performance or functional issues that are not detected until after deployment. We also provide frequent solution updates and enhancements, which increase the possibility of errors, and our reporting, tracking, monitoring and quality assurance procedures may not be sufficient to ensure we detect any such defects in a timely manner. The performance of our products can be negatively impacted by our failure to enhance, expand or update our products, errors or defects in our software, improper deployment or configuration of our services and many other factors.
In addition, because the techniques used by computer hackers to access or sabotage networks change frequently and generally are not recognized until launched against a target, there is a risk that a cyber threat could emerge that our services are unable to detect or prevent until after some of our customers are impacted. Moreover, as our services are adopted by an increasing number of enterprises, it is possible that the individuals and organizations behind cyber threats will focus on finding ways to defeat our services. If this happens, our products could be targeted by attacks specifically designed to disrupt our Zero Trust model and create the perception that our technology is not capable of providing superior cybersecurity, which, in turn, could have a serious impact on our reputation as a provider of cybersecurity solutions. Further, if a high-profile security breach occurs with respect to another similar cybersecurity services provider, our customers and potential customers may lose trust in cybersecurity solutions generally, and with respect to Zero Trust security in particular, which could materially and adversely impact our ability to retain existing customers or attract new customers.
No security solution, including our Zero Trust solutions, can address all possible security threats or block all methods of penetrating a network or otherwise perpetrating a security incident. Our customers must rely on complex network and security infrastructures, which include products and services from multiple vendors, to secure their networks. If any of our customers becomes infected with malware or experiences a security breach, they could be disappointed with our services or products, regardless of whether our services or products are intended to block the attack or would have blocked the attack if the customer had properly configured our product or engaged our services in time. Additionally, if any enterprises that are publicly known to use our services or products are the subject of a cyberattack that becomes publicized, our current or potential customers may look to our competitors for alternatives to our services.
From time to time, industry or financial analysts and research firms evaluate our solutions against other security products. Our services may fail to prevent threats in any particular test for a number of reasons, including misconfiguration. To the extent potential customers, industry or financial analysts or testing firms believe that the occurrence of a failure to prevent any particular threat is a flaw or indicates that our services do not provide significant value, our reputation and business could be materially harmed.
Any real or perceived flaws in our products or services, any real or perceived security breaches or other security incidents of our customers or loss of compliance attestations required by customer contracts, could result in:
| ● | a loss of existing or potential customers or channel partners; |
| ● | delayed or lost sales and harm to our financial condition and results of operations; |
| ● | a delay in attaining, or the failure to attain, market acceptance; |
| ● | the expenditure of significant financial resources in efforts to analyze, correct, eliminate, remediate or work around errors or defects, to address and eliminate vulnerabilities and to address any applicable legal or contractual obligations relating to any actual or perceived security breach; |
| ● | negative publicity and damage to our reputation and brand; and |
| ● | legal claims and demands (including for stolen assets or information, repair of system damages, and compensation to customers and business partners), litigation, regulatory inquiries or investigations and other liability. |
Any of the above results could materially and adversely affect our business, financial condition and results of operations.
Additionally, with product effectiveness a critical competitive factor in our industry, we make public statements, including on our website, in marketing materials and elsewhere, describing the effectiveness of our products and the performance of our solutions. As a result, we may face claims, including claims of unfair or deceptive trade practices, brought by the U.S. Federal Trade Commission, state, local, or foreign regulators, and private litigants.
Risks Related to Our People
We rely on our key technical, sales and management personnel to grow our business, and the loss of one or more key employees or the inability to attract and retain qualified personnel could harm our business.
Our future success is substantially dependent on our ability to attract, retain and motivate the members of our management team and other key employees throughout our organization. We rely on our leadership team in the areas of operations, security, marketing, sales, support and general and administrative functions, and on individual contributors on our research and development team. Although we have entered into employment agreements and other arrangements with certain of our key personnel, our employees, including our executive officers, may terminate their employment with us at any time. We do not maintain key person life insurance policies on any of our employees. The loss of one or more of our executive officers or key employees could seriously harm our business.
To execute our growth plan, we must attract and retain highly qualified personnel. Competition for these personnel is intense, especially for experienced sales professionals and for engineers experienced in designing and developing cybersecurity applications and security software. We have from time to time experienced, and we expect to continue to experience, difficulty in hiring and retaining employees with appropriate qualifications. For example, in recent years, recruiting, hiring and retaining employees with expertise in the cybersecurity industry has become increasingly difficult as the demand for cybersecurity professionals has increased as a result of the recent cybersecurity attacks on global corporations and governments. Many of the companies with which we compete for experienced personnel have greater resources than we have, which provides those companies an advantage in, among other things, recruiting and retaining foreign employees on Visas for work in the U.S. In addition, job candidates and existing employees often consider the value of the equity awards they receive in connection with their employment. Volatility or lack of performance in our stock price may also affect our ability to attract and retain our key employees. Any failure to successfully attract, integrate or retain qualified personnel to fulfill our current or future needs could materially and adversely affect our business, operating results and financial condition.
Our ability to maintain customer satisfaction depends in part on the quality of our customer support, including the quality of the support provided on our behalf by certain channel partners. Failure to maintain high-quality customer support could have an adverse effect on our business, financial condition and results of operations.
If we do not provide adequate support to our customers, our ability to renew subscriptions, increase the number of users and sell additional services to customers will be adversely affected. We believe that successfully delivering our Zero Trust solutions often require a high level of customer support and engagement. We or our channel partners must successfully assist our customers in deploying our Zero Trust solutions, resolving performance issues, and addressing interoperability challenges with a customer’s existing network and security infrastructure. Many enterprises, particularly large organizations, have very complex networks and require high levels of focused support, including premium support offerings, to fully realize the benefits of our products and services. We believe our service is of high quality and a key competitive advantage. Any failure by us to maintain the expected level of support could reduce customer satisfaction and hurt our customer retention, particularly with respect to our large enterprise customers. Additionally, if our channel partners do not provide support to the satisfaction of our customers, we may be required to provide this level of support to those customers, which would require us to hire additional personnel and to invest in additional resources. We may not be able to hire such resources fast enough to keep up with demand, particularly if the sales of our products and services exceed our internal forecasts. Prior to the COVID-19 pandemic, we transitioned to a remote work environment for the majority of our employees. We may not be successful in our efforts to fully onboard new hires and provide adequate training to our employees who are working remotely as a result of our shift to a remote work environment. To the extent that we or our channel partners are unsuccessful in hiring, training and retaining adequate support resources, our ability and the ability of our channel partners to provide adequate and timely support to our customers will be negatively impacted, and our customers’ satisfaction with our products or services could be adversely affected. Furthermore, as we sell our solutions internationally, our support organization faces additional challenges, including those associated with delivering support, training and documentation in languages other than English. Any failure to maintain high-quality customer support, or a market perception that we do not maintain high-quality support, could materially harm our reputation, adversely affect our ability to sell our solutions to existing and prospective customers and could harm our business, financial condition and results of operations.
Risks Related to Our Intellectual Property
It may be difficult to enforce our intellectual property rights, which could enable others to copy or use aspects of our solutions without compensating us.
We believe our intellectual property is a key competitive advantage. We rely on a combination of patent, copyright, trademark and trade secret laws, as well as confidentiality procedures and contractual provisions, to establish and protect our intellectual property rights, all of which provide only limited protection. The efforts we have taken to protect our intellectual property rights may not be sufficient or effective, and our patents, trademarks and copyrights may be held invalid or unenforceable. Moreover, we cannot assure you that any patents will be issued with respect to our currently pending patent applications in a manner that gives us adequate defensive protection or competitive advantages, or that any patents issued to us will not be challenged, invalidated or circumvented. We have filed for patents in the United States and in certain non-U.S. jurisdictions, but such protections may not be available in all countries in which we operate or in which we seek to enforce our intellectual property rights or may be difficult to enforce in practice. For example, many foreign countries have compulsory licensing laws under which a patent owner must grant licenses to third parties. In addition, many countries limit the enforceability of patents against certain third parties, including government agencies or government contractors. In these countries, patents may provide limited or no benefit. Moreover, we may need to expend additional resources to defend our intellectual property rights in these countries, and our inability to do so could impair our business or adversely affect our international expansion. Our currently issued patents and any patents that may be issued in the future with respect to pending or future patent applications may not provide sufficiently broad protection, or they may not prove to be enforceable in actions against alleged infringers. Additionally, the U.S. Patent and Trademark Office and various foreign governmental patent agencies require compliance with a number of procedural, documentary, fee payment and other similar provisions during the patent application process and to maintain issued patents. There are situations in which noncompliance can result in abandonment or lapse of the patent or patent application, resulting in partial or complete loss of patent rights in the relevant jurisdiction. If this occurs, it could materially harm our business, operating results, financial condition and prospects.
We may not be effective in policing unauthorized use of our intellectual property rights, and even if we do detect violations, litigation may be necessary to enforce our intellectual property rights. In addition, our intellectual property may be stolen, including by cybercrimes, and we may not be able to identify the perpetrators or prevent the exploitation of our intellectual property by our competitors or others. Protecting against the unauthorized use of our intellectual property rights, technology and other proprietary rights is expensive and difficult, particularly outside of the United States. Any enforcement efforts we undertake, including litigation, could be time-consuming and expensive and could divert management’s attention, either of which could harm our business, operating results and financial condition. Further, attempts to enforce our rights against third parties could also provoke these third parties to assert their own intellectual property or other rights against us, or result in a holding that invalidates or narrows the scope of our rights, in whole or in part. The inability to adequately protect and enforce our intellectual property and other proprietary rights could seriously harm our business, operating results, financial condition and prospects. Even if we are able to secure our intellectual property rights, we cannot assure you that such rights will provide us with competitive advantages or distinguish our services from those of our competitors or that our competitors will not independently develop similar technology, duplicate any of our technology, or design around our patents.
We incorporate technology from third parties into our products, and our inability to obtain or maintain rights to the technology could harm our business.
We license software and other technology from third parties that we incorporate into or integrate with, our products. We cannot be certain that our licensors are not infringing the intellectual property rights of third parties or that our licensors have sufficient rights to the licensed intellectual property in all jurisdictions in which we may sell our services. In addition, many licenses are non-exclusive, and therefore our competitors may have access to the same technology licensed to us. Some of our agreements with our licensors may be terminated for convenience by them, or otherwise provide for a limited term. If we are unable to continue to license any of this technology for any reason, our ability to develop and sell our services containing such technology could be harmed. Similarly, if we are unable to license necessary technology from third parties now or in the future, we may be forced to acquire or develop alternative technology, which we may be unable to do in a commercially feasible manner or at all, and we may be required to use alternative technology of lower quality or performance standards. This could limit and delay our ability to offer new or competitive products and services. As a result, our business and results of operations could be significantly harmed.
Some of our technology incorporates “open source” software, and we license some of our software through open source projects, which could negatively affect our ability to sell our products and subject us to possible litigation.
Some of our solutions incorporate software licensed by third parties under open source licenses, including open source software embedded in software we receive from third-party commercial software vendors. Use of open source software may entail greater risks than use of third-party commercial software, as open source licensors generally do not provide support, updates or warranties or other contractual protections regarding infringement claims or the quality of the code. In addition, the wide availability of open source software used in our solutions could expose us to security vulnerabilities. Furthermore, the terms of many open source licenses have not been interpreted by U.S. courts, and there is a risk that such licenses could be construed in a manner that imposes unanticipated conditions or restrictions on our ability to market or commercialize our solutions. As a result, we could be subject to lawsuits by parties claiming ownership of what we believe to be open source software. Litigation could be costly for us to defend, have a negative effect on our results of operations and financial condition or require us to devote additional research and development resources to change our solutions. In addition, by the terms of some open source licenses, under certain conditions we could be required to release the source code of our proprietary software, and to make our proprietary software available under open source licenses, including authorizing further modification and redistribution. In the event that portions of our proprietary software are determined to be subject to such requirements by an open source license, we could be required to publicly release the affected portions of our source code, re-engineer all or a portion of our products or services or otherwise be limited in the licensing of our services, each of which provide an advantage to our competitors or other entrants to the market, create security vulnerabilities in our solutions and could reduce or eliminate the value of our services. Further, if we are held to have breached or otherwise failed to comply with the terms of an open source software license, we could be required to release certain of our proprietary source code under open source licenses, pay monetary damages, seek licenses from third parties to continue offering our services on terms that are not economically feasible or be subject to injunctions that could require us to discontinue the sale of our services if re-engineering could not be accomplished on a timely basis. Many of the risks associated with use of open source software cannot be eliminated and could negatively affect our business. Moreover, we cannot assure you that our processes for controlling our use of open source software in our products will be effective. Responding to any infringement or noncompliance claim by an open source vendor, regardless of its validity, or discovering open source software code in our software could harm our business, operating results and financial condition by, among other things:
| ● | resulting in time-consuming and costly litigation; |
| ● | diverting management’s time and attention from developing our business; |
| ● | requiring us to pay monetary damages or enter into royalty and licensing agreements that we would not normally find acceptable; |
| ● | causing delays in the deployment of our products or service offerings to our customers; |
| ● | requiring us to stop offering certain services on or features of our products; |
| ● | requiring us to redesign certain components of our software using alternative non-infringing or non-open source technology, which could require significant effort and expense; |
| ● | requiring us to disclose our software source code and the detailed program commands for our software; and |
| ● | requiring us to satisfy indemnification obligations to our customers. |
Claims by others that we infringe their proprietary technology or other rights, or other lawsuits asserted against us, could result in significant costs and substantially harm our business, financial condition, results of operations and prospects.
A number of companies in our industry hold a large number of patents and also protect their copyright, trade secret and other intellectual property rights, and companies in the networking and security industry frequently enter into litigation based on allegations of patent infringement or other violations of intellectual property rights. In addition, patent holding companies seek to monetize patents they previously developed, have purchased or otherwise obtained. Many companies, including our competitors, may now, and in the future, have significantly larger and more mature patent, copyright, trademark and trade secret portfolios than we have, which they may use to assert claims of infringement, misappropriation and other violations of intellectual property rights against us. In addition, future litigation may involve non-practicing entities or other patent owners who have no relevant product offerings or revenue and against whom our own patents may therefore provide little or no deterrence or protection. As we face increasing competition and gain an increasingly higher profile, including as a result of becoming a public company, the possibility of intellectual property rights claims against us grows. Third parties have asserted in the past and may in the future assert claims of infringement of intellectual property rights against us and these claims, even without merit, could harm our business, including by increasing our costs, reducing our revenue, creating customer concerns that result in delayed or reduced sales, distracting our management from the running of our business and requiring us to cease use of important intellectual property. In addition, because patent applications can take years to issue and are often afforded confidentiality for some period of time, there may currently be pending applications, unknown to us, that later result in issued patents that could cover one or more of our services. Moreover, in a patent infringement claim against us, we may assert, as a defense, that we do not infringe the relevant patent claims, that the patent is invalid or both. The strength of our defenses will depend on the patents asserted, the interpretation of these patents, and our ability to invalidate the asserted patents. However, we could be unsuccessful in advancing non-infringement and/or invalidity arguments in our defense. In the United States, issued patents enjoy a presumption of validity, and the party challenging the validity of a patent claim must present clear and convincing evidence of invalidity, which is a high burden of proof. Conversely, the patent owner need only prove infringement by a preponderance of the evidence, which is a lower burden of proof. Furthermore, because of the substantial amount of discovery required in connection with patent and other intellectual property rights litigation, there is a risk that some of our confidential information could be compromised by the discovery process.
As the number of products and competitors in our market increases and overlaps occur, claims of infringement, misappropriation and other violations of intellectual property rights may increase. Our insurance may not cover intellectual property rights infringement claims. Third parties may in the future also assert infringement claims against our customers or channel partners, with whom our agreements may obligate us to indemnify against these claims. In addition, to the extent we hire personnel from competitors, we may be subject to allegations that such employees have divulged proprietary or other confidential information to us.
From time to time, the U.S. Supreme Court, other U.S. federal courts and the U.S. Patent and Trademark Appeals Board, and their foreign counterparts, have made and may continue to make changes to the interpretation of patent laws in their respective jurisdictions. We cannot predict future changes to the interpretation of existing patent laws or whether U.S. or foreign legislative bodies will amend such laws in the future. Any changes may lead to uncertainties or increased costs and risks surrounding the outcome of third-party infringement claims brought against us and the actual or enhanced damages, including treble damages, that may be awarded in connection with any such current or future claims and could have a material adverse effect on our business and financial condition.
We are unable to predict the likelihood of success in defending against future infringement claims. In the event that we fail to successfully defend ourselves against an infringement claim, a successful claimant could secure a judgment or otherwise require payment of legal fees, settlement payments, ongoing royalties or other costs or damages; or we may agree to a settlement that prevents us from offering certain services or features; or we may be required to obtain a license, which may not be available on reasonable terms, or at all, to use the relevant technology. If we are prevented from using certain technology or intellectual property, we may be required to develop alternative, non-infringing technology, which could require significant time, during which we could be unable to continue to offer our affected services or features, effort and expense and may ultimately not be successful. Any of these outcomes could result in a material adverse effect on our business. Even if we were to prevail, third-party infringement lawsuits could be costly and time-consuming, divert the attention of our management and key personnel from our business operations, deter channel partners from selling or licensing our services and dissuade potential customers from purchasing our services, which would also materially harm our business. In addition, any public announcements of the results of any proceedings in third-party infringement lawsuits could be negatively perceived by industry or financial analysts and investors and could cause our stock price to experience volatility or decline. Further, the expense of litigation and the timing of this expense from period to period are difficult to estimate, subject to change and could adversely affect our results of operations. Any of these events could materially and adversely harm our business, financial condition and results of operations.
Risks Related to Legal and Regulatory Matters
Failure to comply with laws and regulations applicable to our business could subject us to fines and penalties and could also cause us to lose customers in the public sector or negatively impact our ability to contract with the public sector.
Our business is subject to regulation by various federal, state, local and foreign governmental agencies, including agencies responsible for monitoring and enforcing privacy and data protection laws and regulations, employment and labor laws, workplace safety, anti-bribery laws, import and export controls, federal securities laws and tax laws and regulations. In certain jurisdictions, these regulatory requirements may be more stringent than in the United States. These laws and regulations impose added costs on our business. Noncompliance with applicable regulations or requirements could subject us to:
| ● | investigations, enforcement actions and sanctions; |
| ● | mandatory changes to our Zero Trust solutions; |
| ● | disgorgement of profits, fines and damages; |
| ● | civil and criminal penalties or injunctions; |
| ● | claims for damages by our customers or channel partners; |
| ● | termination of contracts; |
| ● | loss of intellectual property rights; and |
| ● | temporary or permanent debarment from sales to government organizations. |
If any governmental sanctions are imposed, or if we do not prevail in any possible civil or criminal litigation, our business, operating results and financial condition could be adversely affected. In addition, responding to any action will likely result in a significant diversion of management’s attention and resources and an increase in professional fees. Enforcement actions and sanctions could materially harm our business, operating results and financial condition.
We endeavor to properly classify employees as exempt versus non-exempt under applicable law. Although there are no pending or threatened material claims or investigations against us asserting that some employees are improperly classified as exempt, the possibility exists that some of our current or former employees could have been incorrectly classified as exempt employees.
In addition, we must comply with laws and regulations relating to the formation, administration and performance of contracts with the public sector, including U.S. federal, state and local governmental organizations, which affect how we and our channel partners do business with governmental agencies. Selling our solutions to the U.S. government, whether directly or through channel partners, also subjects us to certain regulatory and contractual requirements. Failure to comply with these requirements by either us or our channel partners could subject us to investigations, fines and other penalties, which could have an adverse effect on our business, operating results, financial condition and prospects. As an example, the U.S. Department of Justice, or DOJ, and the General Services Administration, or GSA, have in the past pursued claims against and financial settlements with IT vendors under the False Claims Act and other statutes related to pricing and discount practices and compliance with certain provisions of GSA contracts for sales to the federal government. The DOJ and GSA continue to actively pursue such claims. Violations of certain regulatory and contractual requirements could also result in us being suspended or debarred from future government contracting. Any of these outcomes could have a material adverse effect on our revenue, operating results, financial condition and prospects.
We are also subject to the U.S. Foreign Corrupt Practices Act of 1977, the U.K. Bribery Act 2010 and other anti-corruption, anti-bribery, anti-money laundering and similar laws in the United States and other countries in which we conduct activities. Anti-corruption and anti-bribery laws, which have been enforced aggressively and are interpreted broadly, prohibit companies and their employees and agents from promising, authorizing, making or offering improper payments or other benefits to government officials and others in the private sector. We leverage third parties, including channel partners, to sell subscriptions to our products and conduct our business abroad. We and these third-party intermediaries may have direct or indirect interactions with officials and employees of government agencies or state-owned or affiliated entities and we may be held liable for the corrupt or other illegal activities of these third-party business partners and intermediaries, our employees, representatives, contractors, channel partners and agents, even if we do not explicitly authorize such activities. While we have policies and procedures to address compliance with such laws, we cannot assure you that all of our employees and agents will not take actions in violation of our policies and applicable law, for which we may be ultimately held responsible. As we increase our international sales and business, our risks under these laws may increase. Noncompliance with these laws could subject us to investigations, severe criminal or civil sanctions, settlements, prosecution, loss of export privileges, suspension or debarment from U.S. government contracts, other enforcement actions, disgorgement of profits, significant fines, damages, other civil and criminal penalties or injunctions, whistleblower complaints, adverse media coverage and other consequences. Any investigations, actions or sanctions could materially harm our reputation, business, results of operations and financial condition.
These laws and regulations impose added costs on our business, and failure to comply with these or other applicable regulations and requirements could lead to claims for damages from our channel partners or customers, penalties, termination of contracts, loss of exclusive rights in our intellectual property and temporary suspension or permanent debarment from government contracting. Any such damages, penalties, disruptions or limitations in our ability to do business with the public sector could have a material adverse effect on our business and operating results.
We may become involved in litigation that may adversely affect us.
From time to time, we have been subject to claims, suits and other proceedings. Regardless of the outcome, legal proceedings can have an adverse impact on us because of legal costs and diversion of management attention and resources, and could cause us to incur significant expenses or liability, adversely affect our brand recognition or require us to change our business practices. The expense of litigation and the timing of this expense from period to period are difficult to estimate, subject to change and could adversely affect our business, operating results and financial condition. It is possible that a resolution of one or more such proceedings could result in substantial damages, settlement costs, fines and penalties that would adversely affect our business, financial condition, operating results or cash flows in a particular period. These proceedings could also result in reputational harm, sanctions, consent decrees or orders requiring a change in our business practices. Because of the potential risks, expenses and uncertainties of litigation, we may, from time to time, settle disputes, even where we have meritorious claims or defenses, by agreeing to settlement agreements. Because litigation is inherently unpredictable, we cannot assure you that the results of any of these actions will not have a material adverse effect on our business, financial condition, operating results and prospects. Any of these consequences could adversely affect our business, operating results and financial condition.
We could be subject to securities class action litigation. In the past, securities class action litigation has often been instituted against companies following periods of volatility in the market price of a company’s securities.
This type of litigation, if instituted, could result in substantial costs and a diversion of management’s attention and resources, which could adversely affect our business, operating results, or financial condition. Additionally, the dramatic increase in the cost of directors’ and officers’ liability insurance may cause us to opt for lower overall policy limits or to forgo insurance that we may otherwise rely on to cover significant defense costs, settlements, and damages awarded to plaintiffs.
If we were not able to satisfy data protection, security, privacy and other government- and industry-specific requirements or regulations, our business, results of operations and financial condition could be harmed.
Personal privacy, data protection and information security are significant issues in the United States, Europe and in other jurisdictions where we offer our cybersecurity solutions. The regulatory framework for privacy, data protection, and cybersecurity matters is rapidly evolving and is likely to remain uncertain for the foreseeable future. Our handling of data is subject to a variety of laws and regulations, including regulation by various government agencies. Evolving and changing definitions of personal data and personal information, within the E.U., the United States, and elsewhere, may limit or inhibit our ability to operate or expand our business, including limiting strategic partnerships that may involve the sharing or uses of personal data and personal information, and may require significant expenditures and efforts in order to comply.
The U.S. federal government, and various state and foreign governments, have adopted or proposed limitations on the collection, distribution, use and storage of information relating to individuals. Such laws and regulations may require companies to implement privacy and security policies, permit customers to access, correct and delete information stored or maintained by such companies, inform individuals of security breaches that affect their information, and, in some cases, obtain individuals’ consent to use information for certain purposes. Laws and regulations outside the United States, and particularly in Europe, often are more restrictive than those in the United States. In addition, some foreign governments require that certain information collected in a country be retained within that country. We also may find it necessary or desirable to join industry or other self-regulatory bodies or other information security or data protection-related organizations that require compliance with their rules pertaining to information security and data protection. We also may be bound by additional, more stringent contractual obligations relating to our collection, use and disclosure of personal, financial and other data.
We also expect that there will continue to be new proposed laws, regulations and industry standards concerning privacy, data protection and information security in the United States, the European Union and other jurisdictions in which we operate or may operate, and we cannot yet determine the impact such future laws, regulations and standards may have on our business. For example, the European Union implemented the General Data Protection Regulation in May 2018, which imposes stringent data protection requirements and provides for significant penalties for noncompliance. In addition, data protection laws in Europe impose requirements with respect to the cross-border transfer of certain personal data. We historically relied upon data transfer mechanisms such as the EU-U.S. Privacy Shield and the Swiss-U.S. Privacy Shield frameworks, and the use of certain standard contractual clauses approved by the European Commission, to address these requirements. In July 2020, the CJEU, Europe’s highest court, held that the EU-U.S. Privacy Shield was invalid, and imposed additional obligations in connection with the use of contractual clauses governing cross-border transfers of personal data. As a result, we may need to implement different or additional measures to establish or maintain legitimate means for the transfer and receipt of personal data from the European Union to the U.S. In addition, due to the UK’s departure from the European Union, we are subject to requirements for personal data transfers to and from the UK, which continue to evolve following Brexit. If the measures we implement are later determined to be insufficient, we may face enforcement actions by data protection authorities.
In addition, California adopted the California Consumer Privacy Act in 2018, which took effect in January 2020 and seeks to provide California consumers with increased privacy rights and protections for their personal information. The 2018 Act will be further modified by the California Privacy Rights Act, which becomes effective January 1, 2023. Similar laws in Virginia and Colorado take effect on January 1, 2023, and July 1, 2023, respectively. We expect that existing laws, regulations and standards may be interpreted in new manners in the future. Future laws, regulations, standards and other obligations, and changes in the interpretation of existing laws, regulations, standards and other obligations could require us to modify our solutions, restrict our business operations, increase our costs and impair our ability to maintain and grow our customer base and increase our revenue.
Although we work to comply with applicable laws and regulations, industry standards, contractual obligations and other legal obligations, those laws, regulations, standards and obligations are evolving and may be modified, interpreted and applied in an inconsistent manner from one jurisdiction to another, and may conflict with one another. In addition, they may conflict with other requirements or legal obligations that apply to our business or the security features and services that our customers expect from our solutions and may require us to make changes to our solutions or other practices in an effort to comply with them. As such, we cannot assure ongoing compliance with all such laws, regulations, standards and obligations. Any failure or perceived failure by us to comply with applicable laws, regulations, standards or obligations, or any actual or suspected security breach or other security incident, whether or not resulting in unauthorized access to, or acquisition, release or transfer of information relating to individuals or other data, may result in governmental investigations, enforcement actions and other proceedings, private litigation, fines and penalties or adverse publicity, and could cause our customers to lose trust in us, which could have an adverse effect on our reputation and business. Any inability to adequately address privacy and security concerns, even if unfounded, or comply with applicable laws, regulations, standards and obligations, could result in additional cost and liability to us, damage our reputation, inhibit sales, and materially and adversely affect our business and operating results.
Claims for indemnification by our directors and officers may reduce our available funds to satisfy successful third-party claims against us and may reduce the amount of money available to us.
Our A&R Charter and A&R Bylaws provide that we will indemnify our directors and officers, in each case, to the fullest extent permitted by Delaware law. Our A&R Charter also allows our Board to indemnify other employees. This indemnification will extend to the payment of judgments in actions against officers and directors and to reimbursement of amounts paid in settlement of such claims or actions and may apply to judgments in favor of the Company or amounts paid in settlement to the Company. This indemnification will also extend to the payment of attorneys’ fees and expenses of officers and directors in suits against them where the officer or director acted in good faith and in a manner he or she reasonably believed to be in, or not opposed to, the best interests of the Company, and, with respect to any criminal action or proceeding, he or she had no reasonable cause to believe his or her conduct was unlawful. This right of indemnification is not exclusive of any right to which the officer or director may be entitled as a matter of law and shall extend and apply to the estates of deceased officers and directors.
Risks Related to Financial, Tax and Accounting Matters
If we fail to maintain an effective system of disclosure controls and internal control over financial reporting, our ability to produce timely and accurate financial statements or comply with applicable regulations could be impaired.
As a public company, we are subject to the reporting requirements of the Securities Exchange Act of 1934, as amended, or the Exchange Act, the Sarbanes-Oxley Act of 2002, or the Sarbanes-Oxley Act. We expect that the requirements of these rules and regulations will continue to increase our legal, accounting, and financial compliance costs, make some activities more difficult, time-consuming, and costly, and place significant strain on our personnel, systems, and resources.
The Sarbanes-Oxley Act requires, among other things, that we maintain effective disclosure controls and procedures and internal control over financial reporting. We are continuing to develop and refine our disclosure controls and other procedures that are designed to ensure that information required to be disclosed by us in the reports that we will file with the SEC is recorded, processed, summarized, and reported within the time periods specified in SEC rules and forms and that information required to be disclosed in reports under the Exchange Act is accumulated and communicated to our principal executive and financial officers. We are also continuing to improve our internal control over financial reporting, which includes hiring additional accounting and financial personnel to implement such processes and controls.
In connection with the preparation of Legacy Appgate’s consolidated financial statements as of and for the year ended December 31, 2020, Legacy Appgate’s management identified material weaknesses in internal controls over financial reporting over the design of Legacy Appgate’s information technology general controls related to user access and change management as well as certain financial reporting transaction level controls including account reconciliations, related party transactions and journal entries. Our management is responsible for the internal control over financial reporting of the Company and is taking steps to address the material weaknesses, which include engaging external advisors to document the design and implementation of the Company’s internal controls, including the evaluation of the operating effectiveness of these internal controls. We will also continue to expend significant resources, including accounting-related costs and significant management oversight. If any of these new or improved controls and systems do not perform as expected, we may experience additional deficiencies in our controls.
Our current controls and any new controls that we develop may become inadequate because of changes in conditions in our business. Further, weaknesses in our disclosure controls and internal control over financial reporting may be discovered in the future. Any failure to develop or maintain effective controls or any difficulties encountered in their implementation or improvement could harm our results of operations or cause us to fail to meet our reporting obligations and may result in a restatement of our financial statements for prior periods. Any failure to implement and maintain effective internal control over financial reporting also could adversely affect the results of periodic management evaluations and annual independent registered public accounting firm attestation reports regarding the effectiveness of our internal control over financial reporting that we will eventually be required to include in our periodic reports that will be filed with the SEC. Ineffective disclosure controls and procedures and internal control over financial reporting could also cause investors to lose confidence in our reported financial and other information, which would likely have a negative effect on the trading price of our Common Stock. In addition, if we are unable to continue to meet these requirements, we may not be able to remain listed on any national securities exchange on which our Common Stock may be listed in the future. We are not currently required to comply with the SEC rules that implement Section 404 of the Sarbanes-Oxley Act and are therefore not required to make a formal assessment of the effectiveness of our internal control over financial reporting for that purpose. As a public company, we will be required to provide an annual management report on the effectiveness of our internal control over financial reporting with our annual reports on Form 10-K.
Our independent registered public accounting firm is not required to formally attest to the effectiveness of our internal control over financial reporting until after we are no longer a smaller reporting company as defined under Regulation S-K promulgated by the SEC. At such time, our independent registered public accounting firm may issue a report that is adverse in the event it is not satisfied with the level at which our internal control over financial reporting is documented, designed, or operating. Any failure to maintain effective disclosure controls and internal control over financial reporting could have an adverse effect on our business and results of operations and could cause a decline in the price of our Common Stock.
The requirements of being a public company will increase our costs, may divert our resources and management’s attention and may affect our ability to attract and retain executive management and qualified Board members.
As a public company, we are subject to the reporting and corporate governance requirements of the Exchange Act, and other applicable securities rules and regulations, including the Sarbanes-Oxley Act and the Dodd-Frank Wall Street Reform and Consumer Protection Act. Compliance with these rules and regulations will increase our legal and financial compliance costs, make some activities more difficult, time-consuming or costly and increase demand on our systems and resources. Among other things, the Exchange Act requires that we file annual, quarterly and current reports with respect to our business and results of operations and maintain effective disclosure controls and procedures and internal control over financial reporting. In order to improve our disclosure controls and procedures and internal control over financial reporting to meet this standard, additional resources and management oversight may be required. As a result, management’s attention may be diverted from other business concerns, which could harm our business, financial condition, results of operations and prospects. Although we have hired additional personnel to help comply with these requirements, we may need to further expand our legal and finance departments in the future, which will increase our costs and expenses. In addition, changing laws, regulations and standards relating to corporate governance and public disclosure are creating uncertainty for public companies, increasing legal and financial compliance costs and making some activities more time-consuming. These laws, regulations and standards are subject to varying interpretations, in many cases due to their lack of specificity, and, as a result, their application in practice may evolve over time as new guidance is provided by regulatory and governing bodies. This could result in continuing uncertainty regarding compliance matters and higher costs necessitated by ongoing revisions to disclosure and governance practices. We intend to invest resources to comply with evolving laws, regulations and standards, and this investment may result in increased general and administrative expense and a diversion of management’s time and attention from revenue-generating activities to compliance activities. If our efforts to comply with new laws, regulations and standards differ from the activities intended by regulatory or governing bodies, regulatory authorities may initiate legal proceedings against us and our business and prospects may be harmed.
As a result of disclosure of information in the filings required of a public company, our business and financial condition have become more visible, which could result in threatened or actual litigation, including by competitors and other third parties. If such claims are successful, our business, financial condition, results of operations and prospects could be harmed, and even if the claims do not result in litigation or are resolved in our favor, these claims, and the time and resources necessary to resolve them, could divert the resources of our management and harm our business, financial condition, results of operations and prospects. These factors could also make it more difficult for us to attract and retain qualified employees, executive officers and members of our Board.
Our ability to use our net operating loss carryforwards and certain other tax attributes may be limited.
As of December 31, 2020, we had aggregate U.S. federal and state net operating loss carryforwards of $259.0 million and $88.9 million, respectively, which may be available to offset future taxable income for U.S. income tax purposes. If not utilized, $154.1 million of the federal net operating loss carryforwards will begin to expire in 2022 with the remainder carried forward indefinitely, and $85.0 million of the state net operating loss carryforwards will begin to expire in 2021 with the remainder carried forward indefinitely. We also had foreign net operating loss carryforwards of $5.5 million, which do not expire. Realization of these net operating loss carryforwards depends on future income, and there is a risk that certain of our existing carryforwards could expire unused and be unavailable to offset future income tax liabilities, which could adversely affect our operating results and financial condition. In addition, under Sections 382 and 383 of the Internal Revenue Code, if a corporation undergoes an “ownership change,” generally defined as a greater than 50% change (by value) in ownership by “5 percent shareholders” over a rolling three-year period, the corporation’s ability to use its pre-change net operating loss carryovers and other pre-change tax attributes to offset its post-change income or taxes may be limited. Similar rules apply under U.S. state tax laws. We have experienced ownership changes in the past and we may experience an ownership change in the future as a result of shifts in our stock ownership. As a result, if we earn net taxable income, our ability to use our pre-change U.S. net operating loss carryforwards to offset U.S. federal taxable income may be subject to limitations, which could potentially result in increased future tax liability to us.
We could be subject to additional tax liabilities and United States federal income tax reform could adversely affect us.
We are subject to U.S. federal, state, local and sales taxes in the United States and foreign income taxes, withholding taxes and transaction taxes in numerous foreign jurisdictions. Significant judgment is required in evaluating our tax positions and our worldwide provision for income taxes. During the ordinary course of business, there are many activities and transactions for which the ultimate tax determination is uncertain. In addition, our future income tax obligations could be adversely affected by changes in, or interpretations of, tax laws in the United States or in other jurisdictions in which we operate. For example, in December 2017, the United States adopted new tax law legislation commonly referred to as the Tax Cuts and Jobs Act of 2017, or the Tax Act (as modified by the Coronavirus Aid, Relief, and Economic Security Act), which significantly reforms the Internal Revenue Code of 1986, as amended, or the Internal Revenue Code. The Tax Act, among other things, includes changes to U.S. federal tax rates, imposes significant additional limitations on the deductibility of interest and the use of net operating losses generated in tax years beginning after December 31, 2017, allows for the expensing of certain capital expenditures, and puts into effect the migration from a “worldwide” system of taxation to a largely territorial system. Further changes to U.S. tax laws, including limitations on the ability of taxpayers to claim and utilize foreign tax credits, as well as changes to U.S. tax laws that may be enacted in the future, could impact the tax treatment of our foreign earnings. Due to expansion of our international business activities, any changes in the U.S. taxation of such activities may increase our worldwide effective tax rate and adversely affect our operating results and financial condition. The enactment of legislation implementing changes in the U.S. taxation of international business activities or the adoption of other tax reform policies could adversely impact our operating results and financial condition.
We could be required to collect additional sales, use, value added, digital services, or other similar taxes or be subject to other liabilities that may increase the costs our customers would have to pay for our solutions and adversely affect our business, operating results, and financial condition.
We collect sales, use, value added, digital services, and other similar taxes in a number of jurisdictions. One or more U.S. states or countries may seek to impose incremental or new sales, use, value added, digital services, or other tax collection obligations on us. Further, an increasing number of U.S. states have considered or adopted laws that attempt to impose tax collection obligations on out-of-state companies. Additionally, the Supreme Court of the United States ruled in South Dakota v. Wayfair, Inc. et al, or Wayfair, that online sellers can be required to collect sales and use tax despite not having a physical presence in the state of the customer. In response to Wayfair, or otherwise, U.S. states or local governments may adopt, or begin to enforce, laws requiring us to calculate, collect, and remit taxes on sales in their jurisdictions. A successful assertion by one or more U.S. states requiring us to collect taxes where we presently do not do so, or to collect more taxes in a jurisdiction in which we currently do collect some taxes, could result in substantial liabilities, including taxes on past sales, as well as interest and penalties. Furthermore, certain jurisdictions, such as the U.K. and France, have recently introduced a digital services tax, which is generally a tax on gross revenue generated from users or customers located in in those jurisdictions, and other jurisdictions have enacted or are considering enacting similar laws. A successful assertion by a U.S. state or local government, or other country or jurisdiction that we should have been or should be collecting additional sales, use, value added, digital services or other similar taxes could, among other things, result in substantial tax payments, create significant administrative burdens for us, discourage potential customers from subscribing to our solutions due to the incremental cost of any such sales or other related taxes, or otherwise harm our business.
Our corporate structure and intercompany arrangements are subject to the tax laws of various jurisdictions, and we could be obligated to pay additional taxes, which would harm our results of operations.
We are expanding our international operations and staff to support our business in international markets. Our corporate structure and associated transfer pricing policies contemplate the business flows and future growth into the international markets, and consider the functions, risks and assets of the various entities involved in the intercompany transactions. The amount of taxes we pay in different jurisdictions may depend on the application of the tax laws of the various jurisdictions, including the United States, to our international business activities, changes in tax rates, new or revised tax laws or interpretations of existing tax laws and policies, and our ability to operate our business in a manner consistent with our corporate structure and intercompany arrangements. For example, certain jurisdictions have recently introduced a digital services tax, which is generally a tax on gross revenue generated from users or customers located in those jurisdictions, and other jurisdictions are considering enacting similar laws. The taxing authorities of the jurisdictions in which we operate may challenge our methodologies for pricing intercompany transactions pursuant to the intercompany arrangements or disagree with our determinations as to the income and expenses attributable to specific jurisdictions. If such a challenge or disagreement were to occur, and our position was not sustained, or if there are changes in tax laws or the way existing tax laws are interpreted or applied, we could be required to pay additional taxes, interest and penalties, which could result in one-time tax charges, higher effective tax rates, reduced cash flows and lower overall profitability of our operations. Our financial statements could fail to reflect adequate reserves to cover such a contingency.
Our revenue recognition policy and other factors may distort our financial results in any given period and make them difficult to predict.
Under accounting standards update No. 2014-09 (Topic 606), Revenue from Contracts with Customers (“ASC 606”), we recognize revenue when our customer obtains control of goods or services in an amount that reflects the consideration that we expect to receive in exchange for those goods or services. Our revenue includes subscription term-based license revenue and perpetual license revenue, each of which is recognized when we transfer control of such license to the customer, and subscription SaaS and support and maintenance revenue, which is recognized ratably over the contract period. Because subscription term-based and perpetual license revenue is recognized upfront, a single, large license in a given period may distort our operating results for that period. In contrast, the impact of agreements that are recognized ratably may take years to be fully reflected in our financial statements. Consequently, a significant increase or decline in our subscription SaaS and support and maintenance contracts in any one quarter will not be fully reflected in the results for that quarter, but will affect our revenue in future quarters. This also makes it challenging to forecast our revenue for future periods, as both the mix of solutions, solution packages and services we will sell in a given period, as well as the size of contracts, is difficult to predict.
Furthermore, the presentation of our financial results requires us to make estimates and assumptions that may affect revenue recognition. In some instances, we could reasonably use different estimates and assumptions, and changes in estimates are likely to occur from period to period. See “Exhibit 99.2, Audited consolidated financial statements of Legacy Appgate as of and for the years ended December 31, 2020 and 2019 — Note 1. Business and Summary of Significant Accounting Policies – Revenue Recognition.” Given the foregoing factors, our actual results could differ significantly from our estimates, comparing our revenue and operating results on a period-to-period basis may not be meaningful, and our past results may not be indicative of our future performance.
If our estimates or judgments relating to our critical accounting policies prove to be incorrect or financial reporting standards or interpretations change, our results of operations could be adversely affected.
The preparation of financial statements in conformity with U.S. GAAP requires management to make estimates and assumptions that affect the amounts reported in our consolidated financial statements and accompanying notes. We base our estimates on historical experience and on various other assumptions that we believe to be reasonable under the circumstances, as provided in the section titled “Management’s Discussion and Analysis of Financial Condition and Results of Operations” and in our consolidated financial statements and related notes included elsewhere in this Report. The results of these estimates form the basis for making judgments about the carrying values of assets, liabilities and equity, and the amount of revenue and expenses that are not readily apparent from other sources. Significant assumptions and estimates used in preparing our consolidated financial statements include those related to the determination of revenue recognition, and more specifically, the estimation and allocation of the transaction price to each performance obligation based on a relative standalone selling price, allowance for doubtful accounts, valuation and impairment of intangible assets and goodwill, impairment of other long-lived assets, useful lives of property and equipment and definite-lived intangible assets and the period of benefit generated from our deferred contract acquisition costs. Our results of operations may be adversely affected if our assumptions change or if actual circumstances differ from those in our assumptions, which could cause our results of operations to fall below the expectations of industry or financial analysts and investors, resulting in a decline in the trading price of our Common Stock.
Additionally, we regularly monitor our compliance with applicable financial reporting standards and review new pronouncements and drafts thereof that are relevant to us. As a result of new standards, changes to existing standards and changes in their interpretation, we might be required to change our accounting policies, alter our operational policies and implement new or enhance existing systems so that they reflect new or amended financial reporting standards, or we may be required to restate our published financial statements. Such changes to existing standards or changes in their interpretation may have an adverse effect on our reputation, business, financial position and profit, or cause an adverse deviation from our revenue and operating profit target, which may negatively impact our financial results.
We are exposed to fluctuations in currency exchange rates, which could negatively affect our business, operating results and financial condition.
Our sales contracts are primarily denominated in U.S. dollars, and therefore our revenue is not subject to significant foreign currency risk. However, strengthening of the U.S. dollar increases the real cost of our solutions to our customers outside of the United States, which could lead to delays in the purchase of our solutions and the lengthening of our sales cycle. If the U.S. dollar continues to strengthen, this could adversely affect our financial condition and operating results. In addition, increased international sales in the future, including through our channel partners and other partnerships, may result in greater foreign currency denominated sales, increasing our foreign currency risk. Our operating expenses incurred outside the U.S. are primarily denominated in the currency of the country in which such expenses are incurred. As our business continues to grow globally, our exposure to currency exchange rates may increase, which could negatively affect our business, operating results and financial condition. We do not currently hedge against the risks associated with currency fluctuations but may do so in the future.
We may require additional capital to expand our operations and invest in new solutions, and failure to do so could reduce our ability to compete and could harm our business and financial condition.
We expect that our existing cash, cash equivalents and short-term investments will be sufficient to meet our anticipated cash needs for working capital and capital expenditures for at least the next 12 months. We may, however, need to raise additional funds in the future to fund our operating expenses, make capital purchases and acquire or invest in business or technology, and we may not be able to obtain those funds on favorable terms, or at all. If we raise additional equity financing, our stockholders may experience significant dilution of their ownership interests and the per share value of our Common Stock could decline. Furthermore, if we engage in additional debt financing, the holders of our debt would have priority over the holders of our Common Stock, and we may be required to accept terms that restrict our ability to incur additional indebtedness or our ability to pay any dividends on our Common Stock, though we do not intend to pay dividends in the foreseeable future. We may also be required to take other actions, any of which could harm our business and operating results. In addition, the actions taken by state, local, and foreign governments in response to the COVID-19 pandemic or variants of the virus have significantly disrupted economic activity in the jurisdictions in which we operate and may cause volatility in capital markets. If we need to access the capital markets, there can be no assurance that financing may be available on attractive terms, if at all. If we are unable to obtain adequate financing, or financing on terms satisfactory to us, when we require it, our ability to continue to support our business growth and to respond to business challenges could be significantly limited, and our business, operating results, financial condition and prospects could be materially and adversely affected. See also “We have indebtedness, which may increase risk to our business and your investment in us.”
Our Company may have undisclosed liabilities and any such liabilities could negatively impact our revenues, business, prospects, financial condition and results of operations.
Before the Closing, Legacy Appgate conducted due diligence on the Company customary and appropriate for a transaction similar to the Merger. However, the due diligence process may not reveal all material liabilities of our Company currently existing or which may be asserted in the future against our Company relating to its activities before the Closing. In addition, the Merger Agreement contains representations with respect to the absence of any liabilities. However, there can be no assurance that our Company will not have any liabilities upon Closing that we are unaware of or that we will be successful in enforcing any indemnification provisions or that such indemnification provisions will be adequate to reimburse us. Any such liabilities of our Company that survive the Closing could negatively impact our revenues, business, prospects, financial condition and results of operations.
Risks Related to the Ownership of Our Common Stock
The market price of our Common Stock may be volatile, and you could lose all or part of your investment.
Prior to the closing of the Merger, there has not been a public trading market for shares of Legacy Appgate’s Common Stock. It is possible that after the closing of the Merger an active trading market will not develop or continue or, if developed, that any market will be sustained, which could make it difficult for you to sell your shares of Common Stock at an attractive price or at all.
Many factors, which are outside our control, may cause the market price for shares of our Common Stock to fluctuate significantly, including those described elsewhere in this “Risk Factors” section, as well as the following:
| ● | actual or anticipated changes or fluctuations in our operating results; |
| ● | the financial projections we may provide to the public, any changes in these projections or our failure to meet these projections; |
| ● | announcements by us or our competitors of new products or new or terminated significant contracts, commercial relationships or capital commitments; |
| ● | industry or financial analyst or investor reaction to our press releases, other public announcements and filings with the SEC; |
| ● | rumors and market speculation involving us or other companies in our industry; |
| ● | price and volume fluctuations in the overall stock market from time to time; |
| ● | volume fluctuations in the trading of our Common Stock from time to time; |
| ● | changes in operating performance and stock market valuations of other technology companies generally, or those in our industry in particular; |
| ● | the sales of shares of our Common Stock by us or our stockholders; |
| ● | failure of industry or financial analysts to maintain coverage of us, changes in financial estimates by any analysts who follow our company, or our failure to meet these estimates or the expectations of investors; |
| ● | actual or anticipated developments in our business or our competitors’ businesses or the competitive landscape generally; |
| ● | litigation involving us, our industry or both, or investigations by regulators into our operations or those of our competitors; |
| ● | developments or disputes concerning our intellectual property rights or our solutions, or third-party proprietary rights; |
| ● | announced or completed acquisitions of businesses or technologies by us or our competitors; |
| ● | actual or perceived privacy, data protection, or information security incidents or breaches; |
| ● | new laws or regulations or new interpretations of existing laws or regulations applicable to our business; |
| ● | any major changes in our management or our Board; |
| ● | general economic conditions and slow or negative growth of our markets; and |
| ● | other events or factors, including those resulting from war, incidents of terrorism, global pandemics or responses to these events. |
In addition, the stock market in general, and the market for technology companies in particular, has experienced price and volume fluctuations that have often been unrelated or disproportionate to the operating performance of those companies. Broad market and industry factors may affect the market price of our Common Stock, regardless of our actual operating performance.
Our Common Stock has been thinly traded, liquidity is limited, and we may be unable to obtain listing of our Common Stock on a more liquid market.
Our Common Stock has been thinly traded and is currently quoted on the OTC Markets, which provide significantly less liquidity than a national securities exchange such as the New York Stock Exchange (“NYSE”) or the Nasdaq Stock Market (“NASDAQ”). In addition, as of the date of this Report, holders of approximately 95.9% of our Common Stock entered into lock-up agreements that, subject to certain exceptions, prohibit the signing party from selling, contracting to sell or otherwise disposing of any Common Stock or securities that are convertible or exchangeable for Common Stock or entering into any arrangement that transfers the economic consequences of ownership of our Common Stock for a period of up to twelve months from the Closing. Without a large public float, our Common Stock is less liquid than the stock of companies with broader public ownership, and, as a result, the trading prices of our Common Stock may be more volatile. Moreover, we may never be accepted for a listing on a national securities exchange.
For the foregoing reasons, purchasers of our Common Stock may be subject to price volatility risk given the price of our Common Stock may change dramatically from a relatively small trading volume, which may also make our Common Stock more vulnerable to price manipulation attempts. In addition, purchasers of our Common Stock may have less ability to efficiently dispose of their shares at acceptable prices given the lower liquidity in the OTC Markets. We cannot predict the prices at which our Common Stock will trade in the future, if at all.
SIS Holdings can significantly influence our business and affairs and may have conflicts of interest with us in the future.
As of the date of this Report, SIS Holdings, through which, among others, BC Partners and Medina Capital (the “Investors”) hold an indirect interest in our Common Stock, collectively own approximately 89% of our Common Stock. As a result, so long as the Investors and/or their affiliates remain our controlling stockholders they will be able to control, directly or indirectly, and subject to applicable law, all matters affecting us, including:
| ● | any determination with respect to our business direction and policies, including the appointment and removal of officers and directors; |
| ● | any determinations with respect to mergers, business combinations or disposition of assets; |
| ● | compensation and benefit programs and other human resources policy decisions; |
| ● | the payment of dividends on our Common Stock; and |
| ● | determinations with respect to tax matters. |
In addition, the Investors are in the business of making investments in companies and may from time to time acquire and hold interests in businesses that compete directly or indirectly with us. One or more of the Investors may also pursue acquisition opportunities that may be complementary to our business and, as a result, those acquisition opportunities may not be available to us. So long as the Investors, or their respective affiliates, continue to own a significant amount of the outstanding shares of our Common Stock, even if such amount is less than 50%, the Investors will continue to be able to strongly influence us. Certain of our directors are affiliates of the Investors, and our A&R Charter provides that, subject to certain limitations, none of our directors or officers, or any of their affiliates, will have any duty to refrain from (i) engaging in a corporate opportunity in the same or similar lines of business in which we or our affiliates now engage or propose to engage or (ii) otherwise competing with us or our affiliates. See the section “Amendments to Articles of Incorporation or Bylaws—Corporate Opportunity Doctrine” under Item 5.03 of this Report.
If we list our Common Stock on the NYSE or NASDAQ we will be considered a “controlled company” within the meaning of the rules of the NYSE and NASDAQ stock markets and, as a result, will qualify for exemptions from certain corporate governance requirements.
The OTC Markets do not prescribe corporate governance requirements for companies who trade on those markets. We intend to list our stock on either the NYSE or NASDAQ stock markets. As of the date of this Report, SIS Holdings, through which the other Investors hold an indirect interest in our Common Stock, collectively own approximately 89% of our Common Stock. As a result, we are considered as a “controlled company” within the meaning of the corporate governance standards of the NYSE and NASDAQ. Under these rules, a listed company of which more than 50% of the voting power is held by an individual, group or another company is a “controlled company” and may elect not to comply with certain corporate governance requirements, including:
| ● | the requirement that a majority of the board of directors consist of independent directors; |
| ● | the requirement that our nominating and corporate governance committee be composed entirely of independent directors with a written charter addressing the committee’s purpose and responsibilities; |
| ● | the requirement that our compensation committee be composed entirely of independent directors with a written charter addressing the committee’s purpose and responsibilities; and |
| ● | the requirement for an annual performance evaluation of our corporate governance and compensation committees. |
While the Investors control a majority of the voting power of our outstanding Common Stock, we may elect to rely on these exemptions and, as a result, may not have a majority of independent directors on our Board. When established, our nominating and corporate governance and compensation committees may also not consist entirely of independent directors. Accordingly, holders of our Common Stock do not have the same protections afforded to stockholders of companies that are subject to all of the corporate governance requirements of the NYSE or NASDAQ.
Future sales, or the perception of future sales, by us or our existing stockholders in the public market following the Merger could cause the market price for our Common Stock to decline.
The sale of substantial amounts of shares of our Common Stock in the public market, or the perception that such sales could occur, could harm the prevailing market price of shares of our Common Stock. These sales, or the possibility that these sales may occur, also might make it more difficult for us to sell equity securities in the future at a time and at a price that we deem appropriate.
In connection with the Closing, holders of approximately 95.9% of our outstanding Common Stock entered into lock-up agreements that, subject to certain exceptions, prohibit the signing party from selling, contracting to sell or otherwise disposing of any Common Stock or securities that are convertible or exchangeable for Common Stock or entering into any arrangement that transfers the economic consequences of ownership of our Common Stock for a period of up to twelve months from the Closing.
As restrictions on resale end, the market price of our shares of Common Stock could drop significantly if the holders of these restricted shares sell them or are perceived by the market as intending to sell them. These factors could also make it more difficult for us to raise additional funds through future offerings of our shares of Common Stock or other securities.
In addition, certain holders of our Common Stock and the Notes (as defined below) are entitled to rights with respect to registration of their shares under the Securities Act pursuant to certain registration rights agreements. If these holders of our Common Stock, by exercising their registration rights, sell a large number of shares, they could adversely affect the market price for our Common Stock.
We may also issue our shares of Common Stock or securities convertible into shares of our Common Stock from time to time in connection with a financing, acquisition, investments or otherwise. Any such issuance could result in substantial dilution to our existing stockholders and cause the market price of our Common Stock to decline.
We do not intend to pay dividends in the foreseeable future. As a result, your ability to achieve a return on your investment will depend on appreciation in the price of our Common Stock.
We have never declared or paid any cash dividends on our Common Stock. We currently intend to retain all available funds and any future earnings for use in the operation of our business and do not anticipate paying any dividends on our Common Stock in the foreseeable future. Any determination to pay dividends in the future will be at the discretion of our Board. Accordingly, investors must rely on sales of their Common Stock after price appreciation, which may never occur, as the only way to realize any future gains on their investments.
If industry or financial analysts do not publish research about our business, or if they issue inaccurate or unfavorable research regarding our Common Stock, our stock price and trading volume could decline. Moreover, because we were engaged in a transaction that can generally be characterized as a “reverse merger,” we may not be able to attract attention of major brokerage firms.
The trading market for our Common Stock is influenced by the research and reports that industry or financial analysts publish about us or our business. We do not control these analysts, or the content and opinions included in their reports. As a new public company, we may be slow to attract research coverage and the analysts who publish information about our Common Stock will have had relatively little experience with our company, which could affect their ability to accurately forecast our results and make it more likely that we fail to meet their estimates. Moreover, because we were engaged in a transaction that can generally be characterized as a “reverse merger,” we may not be able to attract attention of major brokerage firms. If any of the analysts who cover us issues an inaccurate or unfavorable opinion regarding our stock price, our stock price would likely decline. In addition, the stock prices of many companies in the technology industry have declined significantly after those companies have failed to meet, or significantly exceed, the expectations of analysts. If our financial results fail to meet, or significantly exceed, the expectations of analysts or public investors, analysts could downgrade our Common Stock or publish unfavorable research about us. If one or more of these analysts cease coverage of our company or fail to publish reports on us regularly, our visibility in the financial markets could decrease, which in turn could cause our stock price or trading volume to decline.
If our operating and financial performance in any given period does not meet or exceed the guidance that we provide to the public, the market price of our Common Stock may decline.
We may, but are not obligated to, provide public guidance on our expected operating and financial results for future periods. If we elect to issue such guidance, it will be composed of forward-looking statements subject to the risks and uncertainties described in this Report. Our actual results may not always be in line with or exceed any guidance we have provided, especially in times of economic uncertainty. If, in the future, our operating or financial results for a particular period do not meet any guidance we provide or the expectations of investment analysts, or if we reduce our guidance for future periods, the market price of our Common Stock may decline.
Our A&R Charter designates specific courts as the exclusive forum for certain litigation that may be initiated by our stockholders, which could limit our stockholders’ abilities to obtain a favorable judicial forum for disputes with us or our directors, officers or employees.
Our A&R Charter provides that, unless we consent in writing to the selection of an alternative forum, the sole and exclusive forum, to the fullest extent permitted by law, for (1) any derivative action or proceeding brought on our behalf, (2) any action asserting a claim of breach of a fiduciary duty owed by any of our current or former directors, officers or other employees or stockholders to us or our stockholders, creditors or other constituents, or a claim of aiding and abetting any such breach of fiduciary duty, (3) any action asserting a claim against us or any of our directors or officers or other employees or stockholders arising pursuant to, or any action to interpret, apply, enforce any right, obligation or remedy under or determine the validity of, any provision of the DGCL or our A&R Charter or A&R Bylaws or as to which the DGCL confers jurisdiction on the Court of Chancery of the State of Delaware, (4) any action asserting a claim that is governed by the internal affairs doctrine, or (5) any other action asserting an “internal corporate claim” under the DGCL shall be the Court of Chancery of the State of Delaware (or, if and only if the Court of Chancery does not have subject matter jurisdiction, another state court sitting in the State of Delaware or, if and only if neither the Court of Chancery nor any state court sitting in the State of Delaware has subject matter jurisdiction, then the federal district court for the District of Delaware) (the “Delaware Forum Provision”). Notwithstanding the foregoing, our A&R Charter provides that the Delaware Forum Provision will not apply to any actions arising under the Securities Act or the Exchange Act. Section 27 of the Exchange Act creates exclusive federal jurisdiction over all suits brought to enforce any duty or liability created by the Exchange Act or the rules and regulations thereunder. Our A&R Charter further provides that unless we consent in writing to the selection of an alternative forum, the federal district court for the District of Delaware shall, to the fullest extent permitted by law, be the sole and exclusive forum for resolving any complaint asserting a cause of action arising under the Securities Act (the “Federal Forum Provision”).
The Delaware Forum Provision and the Federal Forum Provision may limit a stockholder’s ability to bring a claim in a judicial forum that it finds favorable for disputes with us or our directors, officers or other employees, which may discourage lawsuits against us and our directors, officers and other employees. Alternatively, if a court were to find the Delaware Forum Provision or the Federal Forum Provision to be inapplicable or unenforceable in an action, we may incur additional costs associated with resolving such action in other jurisdictions, which could harm our business, financial condition or results of operations. Any person or entity purchasing or otherwise acquiring any interest in our shares of capital stock shall be deemed to have notice of and consented to the Delaware Forum Provision and the Federal Forum Provision, but will not be deemed to have waived our compliance with the federal securities laws and the rules and regulations thereunder.
We may issue preferred stock whose terms could adversely affect the voting power or value of our Common Stock.
Our A&R Charter authorizes us to issue, without the approval of our stockholders, one or more classes or series of preferred stock having such designations, preferences, limitations and relative rights, including preferences over our Common Stock with respect to dividends and distributions, as our Board may determine. The terms of one or more classes or series of preferred stock could adversely impact the voting power or value of our Common Stock. For example, we might grant holders of preferred stock the right to elect some number of our directors in all events or on the happening of specified events or the right to veto specified transactions. Similarly, the repurchase or redemption rights or liquidation preferences we might assign to holders of preferred stock could affect the residual value of the Common Stock.
Anti-takeover provisions in our governing documents and under Delaware law could make an acquisition of our company more difficult, limit attempts by our stockholders to replace or remove our current management or directors and limit the market price of our Common Stock.
Our A&R Charter, A&R Bylaws and Delaware law contain provisions that could have the effect of rendering more difficult, delaying or preventing an acquisition deemed undesirable by our Board. Among other things, our A&R Charter and/or A&R Bylaws include the following provisions:
| ● | a staggered board, which means that our Board is classified into three classes of directors with staggered three-year terms and, from and after a Trigger Event, directors are only able to be removed from office for cause and only upon the affirmative vote of the holders of at least 66 2/3% in voting power of all of the then outstanding shares of our Common Stock entitled to vote thereon; |
| ● | limitations on convening special stockholder meetings, which could make it difficult for our stockholders to adopt desired governance changes; |
| ● | a prohibition on stockholder action by written consent from and after the Trigger Event; |
| ● | a forum selection clause, which means certain litigation against us can only be brought in Delaware; |
| ● | from and after the Trigger Event, require the affirmative vote of holders of at least 75% of the voting power of all of the then outstanding shares of Common Stock to amend provisions of the A&R Charter relating to the management of our business, the Board, stockholder action by written consent, competition and corporate opportunities, Section 203 of the DGCL, forum selection and the liability of our directors, or to amend, alter, rescind or repeal our A&R Bylaws; |
| ● | the authorization of undesignated preferred stock, the terms of which may be established and shares of which may be issued without further action by our stockholders; and |
| ● | advance notice procedures, which apply for stockholders to nominate candidates for election as directors or to bring matters before an annual meeting of stockholders. |
These provisions, alone or together, could delay or prevent hostile takeovers and changes in control or changes in our management. We have opted out of Section 203 of the DGCL. However, our A&R Charter contains similar provisions providing that we many not engage in certain “business combinations” with any “interested stockholder” for a three-year period following the time that the stockholder became an interested stockholder, unless (i) prior to the time such stockholder became an interested stockholder, the Board approved the transaction that resulted in such stockholder becoming an interested stockholder, (ii) upon consummation of the transaction that resulted in such stockholder becoming an interested stockholder, the interested stockholder owned at least 85% of the Common Stock or (iii) following Board approval, the business combination receives the approval of the holders of at least two-thirds of our outstanding Common Stock not held by such interested stockholder at an annual or special meeting of stockholders. Our A&R Charter provides that the Investors and their respective affiliates, and any of their respective direct or indirect transferees and any group as to which such persons are a party, do not constitute “interested stockholders” for purposes of this provision.
In addition, our A&R Charter provides that the federal district courts of the United States will be the exclusive forum for resolving any complaint asserting a cause of action arising under the Securities Act but that the forum selection provision will not apply to claims brought to enforce a duty or liability created by the Exchange Act.
Any provision of our A&R Charter, A&R Bylaws or Delaware law that has the effect of delaying, preventing or deterring a change in control could limit the opportunity for our stockholders to receive a premium for their shares of our Common Stock and could also affect the price that some investors are willing to pay for our Common Stock. See the section “Amendments to Articles of Incorporation or Bylaws—Anti-Takeover Provisions” under Item 5.03 of this Report.
Risks Related to Our Outstanding Notes
We have indebtedness, which may increase risk to our business and your investment in us.
Concurrently with the execution of the Merger Agreement, Legacy Appgate entered into the Note Purchase Agreement with the Initial Holders (as defined in the Note Agreements) and the Note Issuance Agreement with Legacy Appgate’s wholly-owned domestic subsidiaries and Magnetar (the Note Purchase Agreement and the Note Issuance Agreement, collectively, the “Note Agreements”). Pursuant to the Note Agreements, Legacy Appgate issued and sold to the Initial Holders $50.0 million aggregate principal amount of Initial Notes on February 9, 2021 and agreed to issue and sell to the Initial Holders $25.0 million aggregate principal amount of Additional Notes on the date of the consummation of the Merger and, at the election of Magnetar, up to $25.0 million Notes in one or more subsequent transactions, on or prior to February 8, 2022. Interest on the Notes is payable either entirely in cash or entirely in kind (“PIK Interest”), or a combination of cash and PIK Interest at our option. The Notes bear interest at the annual rate of 5.0% with respect to interest payments made in cash and 5.5% with respect to PIK Interest. In connection with the consummation of the Merger, Legacy Appgate issued the Additional Notes and Newtown Lane entered into a Supplemental Agreement, providing for the assumption or guarantee by the Newtown Lane of all of Legacy Appgate’s obligations under the Note Agreements and the substitution of the Company’s Common Stock for Legacy Appgate’s capital stock thereunder in all respects. For additional details on the Notes see “Magnetar Convertible Senior Notes” under Item 1.01 of this Report. Our ability to make scheduled payments of the principal of, to pay cash interest on the Notes, if we desire to do so, or to refinance the Notes, or any other indebtedness we may incur, depends on our future performance, which is subject to economic, financial, competitive and other factors beyond our control. Our business may not generate cash flow from operations in the future sufficient to service our debt and make necessary capital expenditures. The Note Agreements contain customary restrictive covenants that limit our ability to engage in activities that may be in our long-term best interest. Those covenants include restrictions on our ability to, among other things, incur additional debt and issue disqualified stock; create liens; pay dividends, acquire shares of capital stock, or make certain investments; issue guarantees; sell certain assets and enter into transactions with affiliates. Our failure to comply with those covenants could result in an event of default which, if not cured or waived, could result in the acceleration of our debt issued under the Note Agreements. Any such event of default or acceleration could have an adverse effect on the trading price of our Common Stock. Furthermore, the terms of any future debt we may incur could have further additional restrictive covenants. We may not be able to maintain compliance with these covenants in the future, and in the event that we are not able to maintain compliance, we cannot assure you that we will be able to obtain waivers from the lenders or amend the covenants.
If we are unable to generate such cash flow, we may be required to adopt one or more alternatives, such as selling assets, restructuring debt or obtaining additional debt financing or equity capital on terms that may be onerous or highly dilutive. Pursuant to the Note Purchase Agreement, Magnetar has certain rights of first offer to purchase no less than 25% of the amount issued by us in certain debt financings, subject to certain exceptions and certain preemptive rights in connection with equity issuances by us, subject to certain exceptions, which may make obtaining additional debt financing or raising equity capital more difficult. Our ability to refinance any future indebtedness will depend on the capital markets, contractual restrictions and our financial condition at such time. We may not be able to engage in any of these activities or engage in these activities on desirable terms, which could result in a default on our debt obligations. In addition, any of our future debt agreements may contain restrictive covenants that may prohibit us from adopting any of these alternatives. Our failure to comply with these covenants could result in an event of default which, if not cured or waived, could result in the acceleration of our debt.
We may not have the ability to raise the funds necessary to repurchase the Notes for cash upon occurrence of certain events, and conversion of the Notes may affect the value of our Common Stock by causing dilution to our existing stockholders.
Holders of the Notes have the right to require us to repurchase their Notes upon the occurrence of (i) a fundamental change (as defined in the Note Issuance Agreement) at a repurchase price equal to 100% of the principal amount of the Notes to be repurchased, plus accrued and unpaid interest, if any, or (ii) upon a change of control (as defined in the Note Issuance Agreement) at a repurchase price equal to 102% of the principal amount of the Notes to be repurchased, plus accrued and unpaid interest, if any. We may not have enough available cash or be able to obtain financing at the time we are required to make such repurchases of Notes. In addition, our ability to repurchase the Notes or to pay cash upon conversions of the Notes may be limited by law, by regulatory authority or by agreements governing our future indebtedness. Our failure to repurchase Notes at a time when the repurchase is required by the Note Issuance Agreement would constitute a default under the Note Issuance Agreement. A default under the Note Issuance Agreement or the fundamental change itself could also lead to a default under agreements governing our future indebtedness. If the repayment of the related indebtedness were to be accelerated after any applicable notice or grace periods, we may not have sufficient funds to repay the indebtedness and repurchase the Notes or make cash interest or principal payments.
In addition, our indebtedness, combined with our other financial obligations and contractual commitments, could have other important consequences. For example, it could:
| ● | make us more vulnerable to adverse changes in general U.S. and worldwide economic, industry and competitive conditions and adverse changes in government regulation; |
| ● | limit our flexibility in planning for, or reacting to, changes in our business and our industry; |
| ● | place us at a disadvantage compared to our competitors who have less debt; |
| ● | limit our ability to borrow additional amounts to fund acquisitions, for working capital and for other general corporate purposes; and |
| ● | make an acquisition of our company less attractive or more difficult. |
Any of these factors could harm our business, results of operations and financial condition. In addition, if we incur additional indebtedness, the risks related to our business and our ability to service or repay our indebtedness would increase.
Subject to certain exceptions, prior to maturity, each holder of Notes shall have the option to convert all or any portion of such Notes into our Common Stock in accordance with the terms of the Note Issuance Agreement. If holders of our Notes elect to convert their notes, we may be obligated to deliver them a significant number of shares of our Common Stock, which would cause dilution to our existing stockholders.
Financial Information
Reference is made to the disclosure set forth in Item 9.01 of this Report relating to the financial information of Legacy Appgate, including:
| ● | the audited consolidated financial statements of Legacy Appgate as of and for the years ended December 31, 2020 and 2019 (Exhibit 99.2 which is incorporated herein by reference); |
| ● | the unaudited condensed consolidated financial statements of Legacy Appgate for the three and six months ended June 30, 2021 and 2020, and as of June 30, 2021 and December 31, 2020 (Exhibit 99.3 which is incorporated herein by reference); and |
| ● | Legacy Appgate’s Management’s Discussion and Analysis of Financial Condition and Results of Operation for the above mentioned periods (Exhibit 99.4 which is incorporated herein by reference). |
Reference is made to the disclosure set forth in Item 9.01 of this Report relating to the pro forma financial information of the Company and Exhibit 99.5, all of which are incorporated herein by reference.
Properties
Our corporate headquarters are located in Coral Gables, Florida. We also have additional offices in multiple other locations in the United States, as well as locations internationally, including in Colombia, Sweden, Argentina and Japan. We do not own any real estate. We believe our current facilities are adequate to meet our needs for the immediate future and that, should it be needed, suitable additional space will be available to accommodate expansion of our operations.
Security Ownership of Certain Beneficial Owners and Management
The following table sets forth information known to the Company regarding the beneficial ownership of the Company’s Common Stock immediately following consummation of the Transactions by:
| | ● | each person who is the beneficial owner of more than 5% of the outstanding shares of Common Stock; |
| | ● | each of the Company’s named executive officers and directors; and |
| | ● | all of the Company’s executive officers and directors as a group. |
Beneficial ownership is determined according to the rules of the SEC, which generally provide that a person has beneficial ownership of a security if he, she or it possesses sole or shared voting or investment power over that security, which includes the power to dispose of or to direct the disposition of the security or has the right to acquire such powers within 60 days. In computing the number of shares of the Company’s Common Stock beneficially owned by a person or entity and the percentage ownership, the Company deemed outstanding shares of its common stock subject to options held by that person or entity that are currently exercisable or exercisable within 60 days of the Closing Date. The Company did not deem these shares outstanding, however, for the purpose of computing the percentage ownership of any other person or entity.
Unless otherwise noted in the footnotes to the following table, and subject to applicable community property laws, the Company believes that the persons and entities named in the table have sole voting and investment power with respect to their beneficially owned Common Stock.
Unless otherwise noted, the address of each beneficial owner is c/o Appgate, Inc., 2333 Ponce De Leon Blvd., Suite 900, Coral Gables, FL 33134.
The beneficial ownership of the Company’s Common Stock is based on 131,793,870 shares of Common Stock issued and outstanding immediately following consummation of the Transactions.
Beneficial Ownership Table
| Name and Address of Beneficial Owner(1) | | Number of
shares of
Common
Stock | | | Percent of Class(2) | |
| Directors and Executive Officers | | | | | | |
| Manuel D. Medina(3) | | | 24,446,660 | | | | 18.5 | % |
| Jonathan J. Ledecky(4) | | | 9,291,013 | | | | 7.0 | % |
| Fahim Ahmed | | | — | | | | — | |
| Barry Field | | | — | | | | — | |
| Raymond Svider | | | — | | | | — | |
| Rene A. Rodriguez | | | — | | | | — | |
| Jeremy M. Dale | | | — | | | | — | |
| Jawahar Sivasankaran | | | — | | | | — | |
| All Directors and Executive Officers as a Group (8 individuals) | | | 33,737,673 | | | | 25.6 | % |
| | | | | | | | | |
| Five Percent Holders: | | | | | | | | |
| SIS Holdings LP(5) | | | 117,149,920 | | | | 89 | % |
| Ironbound Partners Fund, LLC(4) | | | 9,291,013 | | | | 7.0 | % |
| (1) | Unless otherwise noted, the address of each beneficial owner is c/o Appgate, Inc., 2333 Ponce De Leon Blvd., Suite 900, Coral Gables, FL 33134. |
| (2) | Does not give effect to any conversion of the Notes by Magnetar. |
| (3) | Represents the pro rata ownership interest of Medina Capital Fund II – SIS Holdco, LP (the “Medina Stockholder”) in the Common Stock held by SIS Holdings. The Medina Stockholder has the right to nominate certain members of the board of directors of SIS Holdings GP, LLC (“SIS GP”) subject to majority control of the board by BCEC - SIS Holdings L.P. (“BC Partners”), the general partners of which are BCEC Management X Limited and CIE Management IX Limited, which are controlled by their boards of directors, which are appointed by BC Partners Group Holdings Limited, which is a majority-owned subsidiary of BC Partners Holdings Limited, which is controlled by Lee Clark, Karen Jamieson, Mark Rodliffe and Nikos Stathopoulos. The general partner of the Medina Stockholder is Medina Capital Fund II – SIS Holdco GP, LLC (“Medina GP”). Medina GP is controlled through certain affiliates of Medina Capital that are ultimately controlled by Manuel D. Medina. The business address of the Medina Stockholder, Medina GP and Manuel D. Medina is 2333 Ponce De Leon Blvd., Suite 900, Coral Gables, Florida 33134. Mr. Medina disclaims beneficial ownership of all shares of Common Stock owned by the Medina Stockholder, through its interest in SIS Holdings, except to the extent of his pecuniary interest therein. |
| (4) | Represents shares held by Ironbound. Jonathan J. Ledecky, the Company’s former president and a current director, controls Ironbound and therefore is the beneficial owner of the shares held by this entity. The business address of Ironbound is c/o Graubard Miller, 405 Lexington Avenue, 11th Floor, New York, NY 10174. |
| (5) | SIS Holdings is the record holder of 117,149,920 shares of Common Stock. The general partner of SIS Holdings is SIS GP, which is managed by a board of directors, a majority of which is appointed by BC Partners. The general partners of BC Partners are CIE Management IX Limited and BCEC Management X Limited, which are controlled by their boards of directors, which are appointed by BC Partners Group Holdings Limited, which is a majority-owned subsidiary of BC Partners Holdings Limited, which is controlled by Lee Clark, Karen Jamieson, Mark Rodliffe and Nikos Stathopoulos. As a result, each of the foregoing entities may be deemed to share voting and investment power over the shares of Common Stock held by SIS Holdings. The business address of SIS Holdings and SIS GP is 2333 Ponce De Leon Boulevard, Suite 900, Coral Gables, Florida 33134. The business address of BC Partners Holdings Ltd. and BC Partners Group Holdings Ltd. is West Wing, Floor 2, Trafalgar Court, Les Banques, St. Peter, Port Guernsey. The business address of BC Partners, BCEC Management X Ltd. and CIE Management IX Ltd. is Arnold House P.O. Box 273, St. Julian’s Avenue, St. Peter, Port Guernsey. |
Directors and Executive Officers
The following sets forth information regarding the Company’s directors and executive officers upon Closing.
| Name | | Age | | Position Upon Closing |
| Manuel D. Medina | | 69 | | Director and Executive Chairman |
| Jonathan J. Ledecky | | 63 | | Director |
| Fahim Ahmed | | 42 | | Director |
| Barry Field | | 51 | | Director and Chief Executive Officer |
| Raymond Svider | | 59 | | Director |
| Jawahar Sivasankaran | | 44 | | President and Chief Operating Officer |
| Rene A. Rodriguez | | 45 | | Chief Financial Officer |
| Jeremy M. Dale | | 36 | | General Counsel and Secretary |
Manuel D. Medina currently serves as a Director and our Executive Chairman. Prior to the Closing, Mr. Medina served as Executive Chairman of Legacy Appgate. Prior to that, Mr. Medina was Chief Executive Officer of Cyxtera Technologies, Inc. from May 2017 to December 2019 and President from May 2017 to February 2018. Mr. Medina is also the Founder and Managing Partner of Medina Capital, a private equity investment firm that he founded in 2012. Mr. Medina has more than 30 years of experience as a highly successful businessman and entrepreneur in the IT infrastructure and cybersecurity industries. Mr. Medina was the Founder, Chairman of the Board and CEO of Terremark until April of 2011, when Terremark was acquired by Verizon Communications Inc. (NYSE: VZ). Under his leadership, Terremark distinguished itself as a leading global provider of managed IT infrastructure services for Fortune 500 enterprises and federal government agencies. At Terremark, Mr. Medina brought his vision to deliver a comprehensive set of best-of-breed IT infrastructure services from purpose-built, carrier-neutral data center facilities to fruition. Mr. Medina is also the founder and chairman of the board of eMerge Americas, the premier B2B technology event connecting the U.S., Latin America, and Europe. Mr. Medina currently serves on the board of Cyxtera Technologies, Inc. (NASDAQ: CYXT). He received his B.S. in Accounting from Florida Atlantic University. Mr. Medina’s qualifications to serve on the Board include his extensive business and entrepreneurial experience in the technology sector, as well as his strong executive leadership experience and in-depth knowledge of Appgate.
Jonathan J. Ledecky has served as a Director of the Company since October 2015. Mr. Ledecky previously served as the Company’s president from October 2015 through the Closing, where he resigned upon Closing. Mr. Ledecky has been a co-owner of the National Hockey League’s New York Islanders franchise since October 2014. He also serves as an Alternate Governor on the Board of Governors of the NHL and as President of NY Hockey Holdings LLC. Mr. Ledecky has served as chairman of Ironbound Partners Fund, LLC, a private investment management fund, since March 1999. He served as the President and Chief Operating Officer of Northern Star Acquisition Corp. from September 2020 until it consummated an initial business combination with Barkbox, Inc. in June 2021 (NYSE: BARK), at which time it was renamed The Original Bark Company and he has continued to serve as a director since such date. He is the President, Chief Operating Officer and director of Northern Star Investment Corp. II (NYSE: NSTB), a blank check company that has entered into a definitive agreement for a business combination with Apex Fintech Solutions LLC, the parent company of Apex Clearing Corporation, a custody and clearing engine that’s powering the future of digital wealth management. Mr. Ledecky is also the President, Chief Operating Officer and director of Northern Star Investment Corp. III (NYSE: NSTC) and Northern Star Investment Corp. IV (NSTD), each since November 2020, and Chairman of the Board of Pivotal Investment Corporation III (NYSE: PICC), since October 2020, each of which companies is a blank check company that is currently searching for an initial business combination. From July 2019 to December 2020, he was also the Chief Executive Officer and Chairman of the Board of Directors of Pivotal Investment Corporation II (NYSE: PIC), a blank check company that consummated an initial business combination with XL Fleet, which is a leading provider of fleet electrification solutions for Class 2-6 commercial vehicles in North America. From August 2018 to December 2019, he served as Chairman and Chief Executive Officer of Pivotal Acquisition Corp. (NYSE: PVT), a blank check company that consummated an initial business combination with KLDiscovery Inc. in December 2019. Since such date, Mr. Ledecky has continued to serve as a member of the board of KLDiscovery. From July 2005 to December 2007, Mr. Ledecky served as President, Secretary and a Director of Endeavor Acquisition Corp., a blank check company that completed its initial business combination with American Apparel, Inc. From January 2007 to May 2009, he served as President, Secretary and a Director of Victory Acquisition Corp., a blank check company that was unable to consummate an initial business combination. He also served as President, Secretary and a Director of Triplecrown Acquisition Corp., a blank check company, from June 2007 until it completed its initial business combination with Cullen Agricultural Technologies, Inc. in October 2009. During 2007, he also served as President, Secretary and a Director of Grand Slam Acquisition Corp., Performance Acquisition Corp. and Endeavour International Acquisition Corp., three similarly structured blank check companies that never completed their initial public offerings due to market conditions at the time. Mr. Ledecky founded U.S. Office Products in October 1994 and served as its Chief Executive Officer until November 1997 and as its Chairman until its sale in June 1998. U.S. Office Products was one of the fastest start-up entrants in the history of the Fortune 500 with sales in excess of $3 billion within its first three years of operation. From 1999 to 2001, Mr. Ledecky was vice chairman of Lincoln Holdings, owners of the Washington sports franchises in the NBA, NHL and WNBA. In addition to the foregoing, Mr. Ledecky served as Chairman of the Board and Chief Executive Officer of Consolidation Capital Corporation from its formation in February 1997 until March 2000 when it merged with Group Maintenance America Corporation. Mr. Ledecky also has served as a trustee of George Washington University, a director of the U.S. Chamber of Commerce and a commissioner on the National Commission on Entrepreneurship and currently serves as a trustee of the U.S. Olympic Foundation and the U.S. Paralympic Foundation. In 2004, Mr. Ledecky was elected the Chief Marshal of the 2004 Harvard University Commencement, an honor bestowed by his alumni peers for a 25th reunion graduate deemed to have made exceptional contributions to Harvard and the greater society while achieving outstanding professional success. Mr. Ledecky received a B.A. (cum laude) from Harvard University in 1979 and an M.B.A. from the Harvard Business School in 1983. We believe Mr. Ledecky’s qualifications to serve on the Board include his extensive executive leadership and business and entrepreneurial experience, including experience in the technology sector.
Fahim Ahmed currently serves as a Director of the Company. Mr. Ahmed currently serves as Partner at BC Partners. BC Partners is a leading international investment firm that specializes in the investment of assets under management in private equity. Before joining BC Partners in 2006, from 2004 to 2006 and from 2000 to 2002, Mr. Ahmed served as a consultant of the Boston Consulting Group. Mr. Ahmed currently serves on the boards of Chewy Inc. (NYSE: CHWY), an online pet retailer company, Cyxtera Technologies, Inc. (NASDAQ: CYXT), Presidio Inc. and PetSmart. Mr. Ahmed previously served as a director of Suddenlink Communications, and was involved in investments in Office Depot, Inc., Intelsat S.A., Dometic Corporation, and Foxtons. Mr. Ahmed holds a Master of Philosophy degree in economics from Oxford University, where he was a Rhodes Scholar, and a B.A. from Harvard University. Mr. Ahmed’s qualifications to serve on the Board include his outside board experience as a director of public and private entities, his extensive finance expertise and his in-depth knowledge of the technology sector.
Raymond Svider currently serves as a Director of the Company. Mr. Svider currently serves as Partner and Chairman of BC Partners and as Chairman of the Executive Committee of BC Partners. He joined BC Partners in 1992 and is currently based in New York. Since Mr. Svider joined BC Partners in 1992, he has led investments in a number of sectors including TMT, healthcare, industrials, business services, consumer and retail. He is currently Executive Chairman of PetSmart, Inc., a pet supply company, since March 2015, Chairman of the Board of Chewy, Inc. (NYSE: CHWY) since April 2019, Chairman of the Advisory Board of The Aenova Group, a pharmaceutical manufacturing company, since April 2019 and also serves on the boards of Altice USA (NYSE: ATUS), a cable television provider, since June 2017, Intelsat, a communications satellite services provider, since June 2007, Navex Global, a software company, since September 2018, GFL Environmental (NYSE: GFL), a waste management company, since May 2018, GardaWorld, a private security firm, since October 2019, Presidio, Inc., a technology services company, since December 2019, and Cyxtera Technologies, Inc. (NASDAQ: CYXT), a data center company, since February 2020. Mr. Svider previously served as a director of Office Depot, an office supply company, from June 2009 to November 2013, as well on boards of various domestic and international private companies. He is also on the boards of the Mount Sinai Children’s Center Foundation in New York and the Polsky Center Private Equity Council at the University of Chicago. Mr. Svider received an MBA from the University of Chicago and an MS in Engineering from both Ecole Polytechnique and Ecole Nationale Superieure des Telecommunications in France. Mr. Svider’s qualifications to serve on the Board include his outside board experience as a director of public and private entities, and his in-depth knowledge of private equity, finance, corporate governance, and executive compensation and the technology sector.
Barry Field currently serves as a Director and Chief Executive Officer of the Company. Prior to the Closing, Mr. Field served as Chief Executive Officer of Legacy Appgate, a position he held since May 2020. Previously, Mr. Field was Chief Revenue Officer of Legacy Appgate from January 2020 to May 2020, and Chief Revenue Officer of Cyxtera Technologies, Inc., Legacy Appgate’s former parent company, from May 2017 to January 2020. Mr. Field has also been a Partner at Medina Capital, a private equity investment firm, since May 2013. Mr. Field has extensive experience as a sales executive leading successful IT infrastructure and software-enabled technology sales organizations. Mr. Field previously served as CEO of Cryptzone, where he led the strategic vision, product development, international growth and expansion into new markets. He received his B.S. in Marketing from Fairfield University. Mr. Field’s qualifications to serve on the Board include his familiarity with Appgate’s business and operations, as well as his leadership, management and technology experience, particularly in Appgate’s industry.
Jawahar Sivasankaran currently serves as President and Chief Operating Officer of the Company. Prior to the Closing, Mr. Sivasankaran served as President and Chief Operating Officer of Legacy Appgate, a position he held since August 2021. Previously, Mr. Sivasankaran was Group Vice President, Head of Global Security Specialization Sales at Splunk from July 2019 to August 2021. Before that, Mr. Sivasankaran held various positions at Cisco, including, but not limited to, Head of Sales & Business Development, Alliances, Strategic Partners & Managed Services, Global Security Sales Organization from July 2017 to July 2019, Global Security Sales, Senior Director, Head of Business Development and Go-to-Market Strategy from April 2015 to June 2017 and Global Field CTO, Senior Director from December 2012 to April 2015. Mr. Sivasankaran has more than 23 years of industry experience in sales, consulting, business development, and various past technical leadership roles. He received his B.S. in Engineering from the University of Madras, his Masters in Information Systems Management from the University of Phoenix and his MBA from the University of Pennsylvania’s Wharton School.
Rene A. Rodriguez currently serves as Chief Financial Officer of the Company. Prior to the Closing, Mr. Rodriguez served as Chief Financial Officer of Legacy Appgate, a position he held since March 2020. Previously, Mr. Rodriguez was Chief Financial Officer of Cyxtera Technologies, Inc., Legacy Appgate’s former parent company, from May 2017 to January 2020. Mr. Rodriguez has also been the Chief Financial Officer and a partner of Medina Capital, a private equity investment firm, since July 2011. Before that, Mr. Rodriguez served as VP of Financial Planning and Corporate Controller of Terremark Worldwide, Inc., a publicly traded data center company that was sold in 2011, where Mr. Rodriguez was responsible for accounting, financial and regulatory reporting, compliance, cash management, mergers and acquisitions and integration. Mr. Rodriguez has more than 20 years of experience as a finance executive with expertise in managing financial operations, capital markets, investor relations, financial analysis, and mergers and acquisitions. He received his B.B.A. in Accounting from the University of Notre Dame and his MBA in Finance from the University of Miami.
Jeremy M. Dale currently serves as General Counsel and Secretary of the Company. Prior to the Closing, Mr. Dale served as General Counsel of Legacy Appgate, a position he held since January 2020. Previously, Mr. Dale was Associate General Counsel of Cyxtera Technologies, Inc., Legacy Appgate’s former parent company, from May 2017 to January 2020, and Associate General Counsel of 3Cinteractive from July 2014 to April 2017. Prior to that, Mr. Dale was a corporate and securities associate at Greenberg Traurig, LLP from September 2010 to June 2014. He received his B.S. in Finance, B.A. in Economics, and M.S. in Finance from the University of Florida, and his Juris Doctorate from the University of Virginia.
Directors, Director Independence and Board Committees
Effective upon Closing, the Board currently consists of five individuals: Manuel D. Medina, Jonathan J. Ledecky, Fahim Ahmed, Barry Field and Raymond Svider. Upon Closing, Manuel D. Medina and Raymond Svider were appointed Class I directors, with each of their terms expiring at the Company’s 2022 annual meeting of stockholders; Fahim Ahmed and Barry Field were appointed Class II directors, with each of their terms expiring at the Company’s 2023 annual meeting of stockholders; and Jonathan J. Ledecky was appointed as a Class III director, with his term expiring at the Company’s 2024 annual meeting of stockholders.
The Company is currently not subject to any independence requirements with respect to the Board. However, utilizing the definition of “independent” set forth in both the NASDAQ Stock Market’s and New York Stock Exchange’s listing standards, the Company believes that Fahim Ahmed and Raymond Svider are independent.
As a “controlled company”, the Company currently does not have separate or independent audit, nominating or compensation committees. The Board has determined that the Company does not have an “audit committee financial expert,” as that term is defined in Item 407(d)(5) of Regulation S-K.
Our A&R Bylaws (as defined herein) set forth the procedures by which the Company’s stockholders may recommend nominees to the Board.
Family Relationships
There are no family relationships among the Company’s existing directors or officers.
Involvement in Certain Legal Proceedings
During the past ten years, no existing officer or director of the Company has:
(1) Petitioned for bankruptcy under the federal bankruptcy laws or had a petition under the federal bankruptcy laws or any state insolvency law filed by or against, or had a receiver, fiscal agent or similar officer appointed by a court, any business of which such person was a general partner or executive officer either at the time of the bankruptcy or proceeding or within two years prior to that time;
(2) Been convicted in a criminal proceeding or is a named subject of any pending criminal proceeding (excluding traffic violations and other minor offenses);
(3) Been subject to any order, judgment or decree, not subsequently reversed, suspended, or vacated, of any court of competent jurisdiction, permanently or temporarily enjoining him/her from, or otherwise limiting his/her involvement in the following activities:
(a) Acting as a futures commission merchant, introducing broker, commodity trading advisor, commodity pool operator, floor brokerage, leverage transaction merchant, any other person regulated by the Commodity Futures Trading Commission, or an associated person of any of the foregoing, or as an investment adviser, underwriter, broker or dealer in securities, or as an affiliated person, director or employee of any investment company, bank, savings and loan association or insurance company, or engaging in or continuing to conduct or practice in connection with such activity;
(b) Engaging in any type of business practice; or
(c) Engaging in any activity in connection with the purchase or sale of any security or commodity or in connection with any violation of federal or state securities laws or federal commodities laws;
(4) Been subject to any order, judgment or decree, not subsequently reversed, suspended, or vacated, of any federal or state authority barring, suspending, or otherwise limiting for more than 60 days his/her right to engage in any type of activity described in 3(a) above, or to be associated with persons engaged in any such activity;
(5) Been found by a court of competent jurisdiction in a civil action or by the SEC to have violated any federal or state securities law, and the judgment in such civil action or finding by the SEC has not been subsequently reversed, suspended, or vacated;
(6) Been found by a court of competent jurisdiction in a civil action or by the Commodity Futures Trading Commission to have violated a federal commodities law, and the judgment in such civil action or finding by the Commodity Futures Trading Commission has not been subsequently reversed, suspended, or vacated;
(7) Been the subject of, or a party to, any federal or state judicial or administrative order, judgment, decree, or fining, not subsequently reversed, suspended or vacated, relating to an alleged violation of:
(a) Any federal or state securities or commodities law or regulation;
(b) Any law or regulation respecting financing institutions or insurance companies including, but not limited to, a temporary or permanent injunction, order of disgorgement or restitution, civil money penalty or temporary or permanent cease-and-desist order, or removal or prohibition order; or
(c) Any law or regulation prohibiting mail or wire fraud or fraud in connection with any business entity; or
(8) Been the subject of, or a party to, any sanction or order, not subsequently reversed, suspended or vacated, of any self-regulatory organization (as defined in Section 3(a)(26) of the Exchange Act, any registered entity (as defined in Section 1(a)(29) of the Commodity Exchange Act), or any equivalent exchange, association, entity or organization that has disciplinary authority over its members or persons associated with a member.
Executive Compensation
Overview
This section discusses the material components of our executive compensation program for our named executive officers (“Named Executive Officers”) during our fiscal years ended December 31, 2020 and December 31, 2019. As a “smaller reporting company,” we are required to provide executive compensation information for the following individuals: (i) all individuals who served as the Company’s principal executive officer (“PEO”), during the last completed fiscal year, regardless of compensation; (ii) the two most highly compensated executive officers (other than the PEO) who were serving as executive officers of the Company at the end of the last completed fiscal year and whose total compensation was greater than $100,000; and (iii) up to two additional persons who served as executive officers (other than as the PEO) during the last completed fiscal year but were not serving in that capacity at the end of the fiscal year if their total compensation is higher than any of the other two Named Executive Officers in the preceding group.
In 2020, our Named Executive Officers and their positions were as follows:
| ● | Barry Field, our Chief Executive Officer; |
| ● | Michael Aiello, Legacy Appgate’s former Chief Executive Officer; |
| ● | Manuel D. Medina, our Executive Chairman; and |
| ● | Rene A. Rodriguez, our Chief Financial Officer. |
This discussion may contain forward-looking statements that are based on the Company’s current plans, considerations, expectations and determinations regarding future compensation programs. The actual compensation programs that the Company adopts following the filing of this Report may differ materially from the currently planned programs summarized in this discussion.
Summary Compensation Table
The following table sets out the compensation for the Named Executive Officers for the years ended December 31, 2020 and December 31, 2019:
| | | | | | | | | | | | | | | | | Non-Equity Incentive Plan Compensation (US$) | | | | | | | | | | |
| Name and Principal Position | | Fiscal
Year | | Salary
(US$)(3) | | | Bonus
(US$)(4) | | | Stock-Based
Awards
(US$) | | | Option-Based
Awards
(US$) | | | Annual
Incentive
Plans | | | Long-Term
Incentive
Plans(5) | | | Nonqualified
deferred
compensation
earnings
(US$) | | | All Other
Compensation
(US$)(6) | | | Total
Compensation
(US$) | |
| Barry Field, Chief Executive Officer (1) | | 2020 | | | 415,385 | | | | 240,000 | | | | - | | | | - | | | | - | | | | - | | | | - | | | | 7,065 | | | $ | 662,450 | |
| | | 2019 | | | 400,000 | | | | 192,000 | | | | - | | | | - | | | | - | | | | - | | | | - | | | | 6,648 | | | $ | 598,648 | |
| Michael Aiello, former Chief Executive Officer (2) | | 2020 | | | 138,462 | | | | - | | | | - | | | | - | | | | - | | | | - | | | | - | | | | 561,961 | | | $ | 700,423 | |
| | | 2019 | | | 40,385 | | | | - | | | | - | | | | - | | | | - | | | | - | | | | - | | | | 80 | | | $ | 40,465 | |
| Manuel D. Medina, Executive Chairman | | 2020 | | | 207,692 | | | | 120,000 | | | | - | | | | - | | | | - | | | | - | | | | - | | | | 100,457 | | | $ | 428,149 | |
| | | 2019 | | | 600,000 | | | | - | | | | - | | | | - | | | | - | | | | - | | | | - | | | | 240,487 | | | $ | 840,487 | |
| Rene A. Rodriguez, Chief Financial Officer | | 2020 | | | 232,692 | | | | 137,500 | | | | - | | | | - | | | | - | | | | - | | | | - | | | | 3,154 | | | $ | 373,346 | |
| | | 2019 | | | 400,000 | | | | 192,000 | | | | - | | | | - | | | | - | | | | 1,209,478 | | | | - | | | | 5,717 | | | $ | 1,807,195 | |
| (1) | Prior to being appointed as our Chief Executive Officer upon Closing, Mr. Field served as Chief Executive Officer of Legacy Appgate. Mr. Field was elected as Legacy Appgate’s Chief Executive Officer in May 2020. |
| (2) | Mr. Aiello served as Legacy Appgate’s Chief Executive Officer from October 2019 to May 2020, when he exited Legacy Appgate. |
| (3) | Salary amounts represent actual amounts paid to each Named Executive Officer in the applicable year. |
| (4) | Bonus amounts represent actual amounts of cash bonuses earned during the applicable year. The bonuses were paid to the Named Executive Officers in cash in the following year. |
| (5) | The amount reported for 2019 in this column for Mr. Rodriguez reflects the grant date fair value of profit interest units (“PIUs”) in SIS Holdings, LP (“SIS Holdings”) determined in accordance with FASB ASC Topic 718 using a Black-Scholes option pricing model based on the assumptions described in Note 11 to the Company’s Consolidated Financial Statements. As discussed below, Mr. Rodriguez forfeited the 2019 PIUs in 2020 in connection with his transition from being an employee of Cyxtera, Legacy Appgate’s former parent company, or an affiliate of Cyxtera, to becoming an employee of Legacy Appgate. |
| (6) | Amounts represent matching contributions paid in the applicable year to a 401(k) retirement savings plan maintained by an affiliate of Cyxtera, and the dollar value of premiums paid in the applicable year for life and disability insurance. In the case of Mr. Medina for 2020, this column includes $43,743 paid by Legacy Appgate for Mr. Medina’s personal assistant and $53,077 paid by Legacy Appgate for Mr. Medina’s personal driver. In the case of Mr. Medina for 2019, this column includes $107,875 paid by Cyxtera or an affiliate thereof for Mr. Medina’s personal assistant and $110,397 paid by Cyxtera or an affiliate thereof for Mr. Medina’s personal driver. In the case of Mr. Aiello for 2020, this column also includes $577,822 in severance payments associated with his separation from Legacy Appgate. |
Narrative to the Summary Compensation Table
Cyxtera Spin-Off Transaction
Prior to December 31, 2019, Legacy Appgate was a wholly-owned subsidiary of Cyxtera. On December 31, 2019, Cyxtera completed the Cyxtera Spin-Off of Legacy Appgate into a separate, standalone company. For 2019, amounts disclosed in the Summary Compensation Table include all compensation paid to our Named Executive Officers by Cyxtera and its affiliates, including Legacy Appgate. For 2020, amounts disclosed in the Summary Compensation Table include all compensation paid to our Named Executive Officers by Legacy Appgate. Amounts disclosed for 2020 do not include any compensation paid to the Named Executive Officers by Cyxtera and its affiliates, as Legacy Appgate was no longer a subsidiary of Cyxtera.
Base Salaries
We use base salaries to recognize the experience, skills, knowledge, and responsibilities required of all our employees, including our Named Executive Officers. Base salaries are reviewed annually, typically in connection with our annual performance review process, and adjusted from time to time to realign salaries with market levels after taking into account individual responsibilities, performance, and experience. For 2020, the annual base salaries of our Named Executive Officers were: $400,000 for Mr. Field; $300,000 for Mr. Aiello; $200,000 for Mr. Medina and $275,000 for Mr. Rodriguez.
Annual Bonus/Non-Equity Incentive Plan Compensation
During fiscal year 2020, our Named Executive Officers were eligible to earn a cash bonus based upon achievement of both corporate and individual goals determined by Legacy Appgate’s board of directors based on a target percentage of annual base salary. For 2020, the bonus targets for Messrs. Field, Medina, and Rodriguez were each 60% of their respective base salaries. In 2021, Legacy Appgate’s board of directors determined that corporate performance goals were achieved at 100% of target levels. No adjustment was to be made for individual performance with respect to any of the Named Executive Officers, therefore, 2020 annual bonuses were paid to Named Executive Officers at 100% of their individual targets. Mr. Aiello did not receive a bonus for 2020.
Equity-Based Compensation
None of the Company’s Named Executive Officers received awards or grants of equity or equity-based compensation during 2020. However, Messrs. Field, Medina and Rodriguez were previously granted PIUs in SIS Holdings, which at the time owned 100% of the then outstanding common stock of Cyxtera, pursuant to the Cyxtera Stockholder Class B Unit Plan and the Amended and Restated Limited Partnership Agreement of SIS Holdings, dated May 1, 2017. Messrs. Field and Medina were granted PIUs in 2017 and Mr. Rodriguez was granted PIUs in 2017 and 2019. The PIUs are intended to align the interests of such Named Executive Officers with those of SIS Holdings, Cyxtera’s equity sponsor, and provide a retention incentive for such Named Executive Officers.
The PIUs are intended to constitute profits interests for U.S. federal income tax purposes that allow Messrs. Field, Medina and Rodriguez to participate in the increase in value of SIS Holdings from and after the date of grant of such interests based on SIS Holding’s ownership of Legacy Appgate and Cyxtera. The PIUs are subject to time-vesting provisions and generally vest as to 25% of such PIUs on the first anniversary of the date of grant and as to 75% of such PIUs in substantially equal monthly installments over 42 months thereafter, subject generally to continued employment and subject to accelerated vesting upon certain liquidity events, which do not include the Merger.
Notwithstanding the foregoing, under the Cyxtera Class B Unit Plan, if Mr. Field, Medina or Rodriguez’s employment terminates other than (i) by SIS Holdings or its subsidiaries for “Cause” (as defined in the Cyxtera Class B Unit Plan) or (ii) by Mr. Field, Medina or Rodriguez without “Good Reason” (as defined in the Cyxtera Class B Unit Plan) and a third-party adjudication makes a final binding determination that the applicable Named Executive Officer breached applicable restrictive covenants (such event, a “Specified Termination”), then vested PIUs with respect to such Named Executive Officer will be subject to a repurchase right at fair market value. In the event that Mr. Field, Medina or Rodriguez’s employment is terminated by SIS Holdings or its subsidiaries for Cause or by the applicable Named Executive Officer upon a Specified Termination, then the vested PIUs will be subject to a repurchase right at the lower of fair market value or the purchase price paid by the applicable Named Executive Officer. In all such instances, unvested PIUs are forfeited.
On September 6, 2021, the Company adopted an incentive compensation plan (the “2021 Plan”), which became effective upon the Closing, under which equity-based incentive awards may be granted in the future. The terms of the Company’s 2021 Plan are described below under Item 5.02 of this Report, which is incorporated herein by reference. The description therein of the 2021 Plan is qualified in its entirety by the full text of the 2021 Plan, a copy of which is filed as Exhibit 10.11 to this Report, and incorporated herein by reference.
Retirement Plan
An affiliate of Cyxtera maintained a 401(k) retirement savings plan for employees of Cyxtera and its subsidiaries, including Legacy Appgate’s employees, who satisfied certain eligibility requirements. The Company’s Named Executive Officers were eligible to participate in the 401(k) plan in 2019 and 2020 on the same terms as other Legacy Appgate full-time employees. Under this plan, Cyxtera or its subsidiaries provided employer matching contributions equal to 100% of the first 1% of eligible compensation contributed by employees and 50% of the next 5% of eligible compensation contributed by employees.
Effective January 1, 2021, Legacy Appgate established a new 401(k) retirement savings plan for its employees.
The Company does not maintain, sponsor, contribute to or otherwise have any liability with respect to any single or multiemployer defined benefit pension plan or nonqualified deferred compensation plan.
Employee Benefits
For 2019 and 2020, the Company’s Named Executive Officers were eligible to participate in Cyxtera’s employee benefit plans and programs, including medical and dental benefit plans, to the same extent as Legacy Appgate’s other full-time employees, subject to the terms and eligibility requirements of those plans. Effective January 1, 2021, Legacy Appgate established its own employee benefit plans and programs. The Named Executive Officers are eligible to participate in such employee benefit plans and programs to the same extent as the Company’s other full-time employees, subject to the terms and eligibility requirements of those plans.
Outstanding Equity Awards at 2020 Fiscal Year-End
The Company’s Named Executive Officers do not hold equity awards in the Company. However, Messrs. Field, Medina and Rodriguez hold PIUs in SIS Holdings. The following table summarizes the number of outstanding PIUs held by Messrs. Field, Medina and Rodriguez at 2020 fiscal year-end.
| Option Awards |
| Name | | Grant
Date | | Number of
securities
underlying
unexercised
options (#)
exercisable (1) | | | Number of
securities
underlying
unexercised
options (#)
unexercisable (1) | | | Option
exercise
price
($) | | | Option
expiration
date (2) | |
| Barry Field | | 5/1/2017 | | | 50,223 | | | | 12,277 | | | | - | | | | - | |
| Manuel D. Medina | | 5/1/2017 | | | 171,592 | | | | 12,605 | | | | - | | | | - | |
| Rene A. Rodriguez | | 5/1/2017 | | | 31,875 | | | | - | | | | - | | | | - | |
| (1) | The PIUs vest as to 25% of such PIUs on the first anniversary of the date of grant and as to 75% of such PIUs in substantially equal monthly installments over 42 months thereafter, subject generally to continued employment. Upon the completion of either (i) a transaction which results in the sale of all or substantially all of SIS Holdings and its subsidiaries’ assets or (ii) a transaction which results in the change of over 50% of the beneficial ownership of the voting units of SIS Holdings, all such PIUs then unvested shall become fully vested, provided that the applicable Named Executive Officer has remained continuously employed with SIS Holdings or one of its controlled affiliates from the date of grant to the date of such transaction. The Merger will not constitute such transaction and will not cause the vesting of PIUs to be accelerated. |
| (2) | The outstanding PIUs are most similar to option awards in that they share in equity value appreciation from and after the date of grant. However, they do not have an exercise price or expiration date. |
Other Elements of Compensation
Employment Agreements
On October 12, 2021, the Company entered into employment agreements with each of Messrs. Field and Rodriguez, each effective upon Closing. Mr. Medina entered into an employment agreement with Legacy Appgate effective as of January 1, 2020. On October 12, 2021, Mr. Medina’s employment agreement was amended and assigned by Legacy Appgate to the Company.
The employment agreement and subsequent separation agreement and release entered into by Michael Aiello with Legacy Appgate, Legacy Appgate’s former Chief Executive Officer, are filed as Exhibits 10.17 and Exhibit 10.18 to this Report, respectively, and are each incorporated herein by reference.
The following discussion contains a summary of the terms of the Named Executive Officer employment agreements currently in effect.
Field Employment Agreement
The Company entered into an employment agreement with Mr. Field on October 12, 2021, which sets forth the terms and conditions of his employment (the “Field Agreement”). Pursuant to the Field Agreement, Mr. Field serves as our Chief Executive Officer and is entitled to an annual base salary of $410,000 and is eligible to participate in the Company’s annual incentive program with a target annual bonus opportunity of 80% of his annual base salary. The Field Agreement may be terminated by either party at any time, provided that Mr. Field is required to give the Company at least 45 days advance notice of termination.
In the event Mr. Field resigns for “Good Reason” or the Company terminates his employment without “Cause” (each as defined in the Field Agreement) in either case outside of the Change in Control Period, he is entitled to receive the following payments and benefits, in addition to any accrued obligations and subject to his timely execution and non-revocation of a general release of claims in the Company’s favor and continued compliance with the restrictive covenants contained in the Field Agreement: (i) an amount of cash equal to the sum of (a) 12 months of his then-current annual base salary and (b) his target bonus, payable in the form of salary continuation in regular installments, in accordance with our normal payroll practices, over a period of 12 months from the termination date, (ii) an amount of cash equal to a prorated portion of his annual bonus, based on actual performance, for the fiscal year in which the termination or resignation occurs, paid in the following fiscal year as soon as practicable after the completion of the audited financial statements for the year in which the termination or resignation occurs, but not later than 45 days after the completion of such audited financial statements, (iii) reimbursement for his healthcare insurance premiums for a period of up to 12 months, and (iv) any accrued annual bonus amounts with respect to the year prior to the year in which the termination occurs, to the extent unpaid at such time, paid as soon as practicable after the completion of the audited financial statements for the year prior to the year in which the termination occurs, but not later than 45 days after the completion of such audited financial statements.
In the event of Mr. Field’s termination due to his death or disability, in addition to accrued obligations, he or his estate, as applicable, shall be entitled to receive a prorated portion of his annual bonus, based on actual performance, for the fiscal year in which the termination occurs. Such bonus shall be paid in the following fiscal year as soon as practicable after the completion of the audited financial statements for the year in which the termination occurs, but not later than 45 days after the completion of such audited financial statements. In addition, under the Field Agreement, Mr. Field’s outstanding awards under the 2021 Plan will vest in a pro-rata amount up to the date of termination, subject to applicable terms and conditions set forth in the Field Agreement related to any performance awards that are outstanding at such time. Mr. Field shall also receive any accrued annual bonus amounts with respect to the year prior to the year in which the termination occurs, to the extent unpaid at such time, paid as soon as practicable after the completion of the audited financial statements for the year prior to the year in which the termination occurs, but not later than 45 days after the completion of such audited financial statements.
In the event Mr. Field resigns for “Good Reason” or we terminate his employment without “Cause” in either case during the period beginning ninety (90) days prior to and ending on the first (1st) anniversary of the effective date of a Change in Control (as defined in the 2021 Plan) (the “Change in Control Period”), he is entitled to receive the following payments and benefits, in addition to any accrued obligations and subject to his timely execution and non-revocation of a general release of claims in our favor and continued compliance with the restrictive covenants contained in the Field Agreement: (i) an amount of cash equal to the sum of (a) 18 months of his then-current annual base salary and (b) his target bonus, (ii) an amount of cash equal to a prorated portion of his annual bonus, based on actual performance, for the fiscal year in which the termination occurs, (iii) an amount equal to 18 months multiplied by the total applicable monthly premium cost for continued healthcare insurance, and (iv) an amount equal to any accrued annual bonus amounts with respect to the year prior to the year in which the termination occurs, to the extent unpaid at such time, each payable in a lump sum payment within thirty (30) days following his separation from the Company. In addition, under the Field Agreement, 100% of Mr. Field’s outstanding awards under the 2021 Plan will vest, subject to applicable terms and conditions set forth in the Field Agreement related to any performance awards that are outstanding at such time.
The Field Agreement contains a non-disclosure covenant, a mutual non disparagement covenant and non-competition, customer non-solicitation, and employee non-solicitation covenants.
The foregoing description of the Field Agreement is qualified in its entirety by reference to the full text of the Field Agreement, a copy of which is filed as Exhibit 10.13 to this Report, and incorporated herein by reference.
Medina Employment Agreement
Legacy Appgate entered into an employment agreement with Mr. Medina on November 18, 2019, which became effective as of January 1, 2020 and set forth the terms and conditions of his employment (the “Prior Medina Agreement”). On October 12, 2021, Legacy Appgate, the Company and Mr. Medina entered into an amended and restated employment agreement, which became effective the same day (the “Medina Agreement”). Among other things, the Medina Agreement amended and restated the Prior Medina Agreement in its entirety and assigned all rights and obligations of Legacy Appgate to the Company. Pursuant to the Medina Agreement, Mr. Medina serves as the Company’s Executive Chairman and is entitled to, among other things (i) an annual base salary of $200,000, (ii) participate in the annual incentive program with a target annual bonus opportunity of 60% of his annual base salary, (iii) personal office space and administrative support, (iv) a personal driver, and (v) subject to approval of the Board and other conditions, a restricted stock unit award for 2021 in the amount of 1,102,217 shares of the Company’s common stock (the “RSU Award”), with such RSUs to vest, in full, on the later of (a) January 1, 2022 and (b) the date of grant of such RSUs. The RSU Award is in consideration for Mr. Medina’s agreement to waive certain rights to equity awards under the Prior Medina Agreement. The Medina Agreement may be terminated by either party at any time, provided that Mr. Medina is required to give the Company at least 45 days advance notice of termination.
In the event Mr. Medina resigns for “Good Reason” or the Company terminates his employment without “Cause” (each as defined in the Medina Agreement), in either case outside of the Change in Control Period, he is entitled to receive the following payments and benefits, in addition to any accrued obligations and subject to his timely execution and non-revocation of a general release of claims in the Company’s favor and continued compliance with the restrictive covenants contained in the Medina Agreement: (i) an amount of cash equal to the sum of (a) 12 months of his then-current annual base salary and (b) his target bonus, payable in the form of salary continuation in regular installments, in accordance with our normal payroll practices, over a period of 12 months from the termination date, (ii) an amount of cash equal to a prorated portion of his annual bonus, based on actual performance, for the fiscal year in which the termination or resignation occurs, paid when bonuses for such fiscal year are paid in the ordinary course to actively employed senior executives of the Company (but in no event later than the date that is two and half months into the following fiscal year), (iii) reimbursement for his healthcare insurance premiums for a period of up to 12 months and (iv) any accrued annual bonus amounts with respect to the year prior to the year in which the termination occurs, to the extent unpaid at such time, paid as soon as practicable after the end of the year for which it is earned (and, in all events, prior to the later of (i) date that is two and a half months after the end of the year for which it is earned or (ii) 30 days after the completion of the audited financial statements for such year but not later than 120 days after the end of the year).
In the event of Mr. Medina’s termination due to his death or disability, in addition to accrued obligations, he or his estate, as applicable, shall be entitled to receive a prorated portion of his annual bonus, based on actual performance, for the fiscal year in which the termination occurs. Such bonus shall be paid when bonuses for such fiscal year are paid in the ordinary course to actively employed senior executives of the Company (but in no event later than the date that is two and half months into the following fiscal year). In addition, under the Medina Agreement, Mr. Medina’s outstanding awards under the 2021 Plan will vest in a pro-rata amount up to the date of termination, subject to applicable terms and conditions set forth in the Medina Agreement related to any performance awards that are outstanding at such time. Mr. Medina shall also receive any accrued annual bonus amounts with respect to the year prior to the year in which the termination occurs, to the extent unpaid at such time, paid as soon as practicable after the end of the year for which it is earned (and, in all events, prior to the later of (i) date that is two and a half months after the end of the year for which it is earned or (ii) 30 days after the completion of the audited financial statements for such year but not later than 120 days after the end of the year). Finally, in the event of Mr. Medina’s termination due to his disability, Mr. Medina shall be entitled to reimbursement for his healthcare insurance premiums for a period of up to 12 months.
In the event Mr. Medina resigns for “Good Reason” or the Company terminates his employment without “Cause” in either case during the Change in Control Period, he is entitled to receive the following payments and benefits, in addition to any accrued obligations and subject to his timely execution and non-revocation of a general release of claims in our favor and continued compliance with the restrictive covenants contained in the Medina Agreement: (i) an amount of cash equal to the sum of (a) 18 months of his then-current annual base salary and (b) his target bonus, (ii) an amount of cash equal to a prorated portion of his annual bonus, based on actual performance, for the fiscal year in which the termination occurs, (iii) an amount equal to 18 months multiplied by the total applicable monthly premium cost for continued healthcare insurance, and (iv) an amount equal to any accrued annual bonus amounts with respect to the year prior to the year in which the termination occurs, to the extent unpaid at such time, each payable in a lump sum payment within thirty (30) days following his separation from the Company. In addition, under the Medina Agreement, 100% of Mr. Medina’s outstanding awards under the 2021 Plan will vest, subject to applicable terms and conditions set forth in the Medina Agreement related to any performance awards that are outstanding at such time.
The Medina Agreement contains a non-disclosure covenant, a mutual non disparagement covenant and non-competition, customer non-solicitation, and employee non-solicitation covenants.
The foregoing description of the Medina Agreement is qualified in its entirety by reference to the full text of the Medina Agreement, a copy of which is filed as Exhibit 10.12 to this Report, and incorporated herein by reference.
Rodriguez Employment Agreement
The Company entered into an employment agreement with Mr. Rodriguez on October 12, 2021, which sets forth the terms and conditions of his employment (the “Rodriguez Agreement”). Pursuant to the Rodriguez Agreement, Mr. Rodriguez serves as our Chief Financial Officer and is entitled to an annual base salary of $295,000 and is eligible to participate in the Company’s annual incentive program with a target annual bonus opportunity of 60% of his annual base salary. The Rodriguez Agreement may be terminated by either party at any time, provided that Mr. Rodriguez is required to give the Company at least 45 days advance notice of termination.
In the event Mr. Rodriguez resigns for “Good Reason” or the Company terminates his employment without “Cause” (each as defined in the Rodriguez Agreement) in either case outside of the Change in Control Period, he is entitled to receive the following payments and benefits, in addition to any accrued obligations and subject to his timely execution and non-revocation of a general release of claims in the Company’s favor and continued compliance with the restrictive covenants contained in the Rodriguez Agreement: (i) an amount of cash equal to 12 months of his then-current annual base salary, payable in the form of salary continuation in regular installments, in accordance with our normal payroll practices, over a period of 12 months from the termination date, and (ii) reimbursement for his healthcare insurance premiums for a period of up to 12 months.
In the event of Mr. Rodriguez’s termination due to his death or disability, in addition to accrued obligations, he or his estate, as applicable, shall be entitled to receive a prorated portion of his annual bonus, based on actual performance, for the fiscal year in which the termination occurs. Such bonus shall be paid in the following fiscal year as soon as practicable after the completion of the audited financial statements for the year in which the termination or resignation occurs, but not later than 45 days after the completion of such audited financial statements. In addition, under the Rodriguez Agreement, Mr. Rodriguez’s outstanding awards under the 2021 Plan will vest in a pro-rata amount up to the date of termination, subject to applicable terms and conditions set forth in the Rodriguez Agreement related to any performance awards that are outstanding at such time. Mr. Rodriguez shall also receive any accrued annual bonus amounts with respect to the year prior to the year in which the termination occurs, to the extent unpaid at such time, paid as soon as practicable after the completion of the audited financial statements for the year prior to the year in which the termination occurs, but not later than 45 days after the completion of such audited financial statements.
In the event Mr. Rodriguez resigns for “Good Reason” or we terminate his employment without “Cause” in either case during the Change in Control Period, he is entitled to receive the following payments and benefits, in addition to any accrued obligations and subject to his timely execution and non-revocation of a general release of claims in our favor and continued compliance with the restrictive covenants contained in the Rodriguez Agreement: (i) an amount of cash equal to the sum of (a) 12 months of his then-current annual base salary and (b) his target bonus, (ii) an amount of cash equal to a prorated portion of his annual bonus, based on actual performance, for the fiscal year in which the termination occurs, (iii) an amount equal to 12 months multiplied by the total applicable monthly premium cost for continued healthcare insurance, and (iv) an amount equal to any accrued annual bonus amounts with respect to the year prior to the year in which the termination occurs, to the extent unpaid at such time, each payable in a lump sum payment within thirty (30) days following his separation from the Company. In addition, under the Rodriguez Agreement, 100% of Mr. Rodriguez’s outstanding awards under the 2021 Plan will vest, subject to applicable terms and conditions set forth in the Rodriguez Agreement related to any performance awards that are outstanding at such time.
The Rodriguez Agreement contains a non-disclosure covenant, a mutual non disparagement covenant and non-competition, customer non-solicitation, and employee non-solicitation covenants.
The foregoing description of the Rodriguez Agreement is qualified in its entirety by reference to the full text of the Rodriguez Agreement, a copy of which is filed as Exhibit 10.14 to this Report, and incorporated herein by reference.
Director Compensation
Fiscal Year 2020
Rene A. Rodriguez, the Company’s Chief Financial Officer, and Victor Semah, who serves as Cyxtera’s Chief Legal Officer, Chief Compliance Officer & Secretary, served on Legacy Appgate’s board of directors in 2020. As a Named Executive Officer of the Company, information regarding Mr. Rodriguez’s compensation for his services as an executive officer in 2020 is set forth in the section titled “Summary Compensation Table” above. Mr. Rodriguez did not receive additional compensation for his service as a director.
Mr. Semah was an executive officer of Cyxtera in 2020 and did not receive any compensation for his service as a Legacy Appgate director in 2020. Mr. Semah stepped down from Legacy Appgate’s board of directors in July 2021.
The following table provides summary information concerning compensation paid or accrued by us to or on behalf of our directors for services rendered to us during the last fiscal year.
| Name | | | Fees
Earned
or Paid
in
Cash
($) | | | | Stock
Awards
($) | | | | Option
Awards
($) | | | | Non-equity
incentive plan
compensation
($) | | | | Nonqualified
deferred
compensation
earnings
($) | | | | All Other
Compensation ($) | | | | Total
($) | |
| Rene A. Rodriguez (1) | | | - | | | | - | | | | - | | | | - | | | | - | | | | - | | | | - | |
| Victor F. Semah (2) | | | - | | | | - | | | | - | | | | - | | | | - | | | | - | | | | - | |
| (1) | Mr. Rodriguez is a Named Executive Officer of the Company for 2020. The table does not include compensation paid to him in connection with the services as an executive officer. Mr. Rodriguez did not receive additional compensation for his service as a director in 2020. As a Named Executive Officer of the Company, information regarding Mr. Rodriguez’s compensation for his services as an executive officer in 2020 is set forth in the section titled “Summary Compensation Table” above. |
| (2) | Mr. Semah was an executive officer of Cyxtera for 2020. The table does not include compensation paid to him in connection with his services as an executive officer of Cyxtera. Mr. Semah did not receive compensation for his service as a Legacy Appgate director in 2020. |
Compensation of Current Company Directors
Messrs. Field and Medina, who currently serve as directors and executive officers of the Company, do not receive additional compensation owing to their service as directors. None of the Company’s other current directors receive any compensation for their service as directors.
Compensation Committee Interlocks and Insider Participation
None of our executive officers serves as a member of the Board or Compensation Committee (or other committee performing equivalent functions) of any entity that has one or more executive officers serving on our Board.
Certain Relationships and Related Transactions, and Director Independence
Certain Relationships and Related Person Transactions
In addition to the compensation arrangements with directors and executive officers described under “Executive Compensation”, the following is a description of each transaction since January 1, 2019 and each currently proposed transaction in which:
| ● | Appgate has been or is to be a participant; |
| ● | the amount involved exceeds or will exceed $120,000; and |
| ● | any of Appgate’s directors, executive officers or beneficial holders of more than 5% of Appgate’s capital stock, or any immediate family member of, or person sharing the household with, any of these individuals (other than tenants or employees), had or will have a direct or indirect material interest. |
Legacy Cyxtera Related Party Transactions
Prior to December 31, 2019, Legacy Appgate was wholly-owned by Cyxtera. On December 31, 2019, Cyxtera consummated several transactions (the “Cyxtera Spin-Off”), following which Legacy Appgate became a separate, stand-alone entity. The transaction separated Cyxtera’s data center business from Legacy Appgate’s cybersecurity business. Over time, Legacy Appgate has entered into several agreements and transactions with Cyxtera (and/or one or more of its subsidiaries), SIS Holdings, which beneficially owns approximately 89% of our Common Stock, and certain equity owners of SIS Holdings. These agreements, relationships and transactions are described below.
Service Provider Fee
In connection with the formation of Cyxtera in 2017, certain equity owners of SIS Holdings and/or affiliates thereof (collectively, the “Service Providers”) entered into a Services Agreement (the “Services Agreement”), dated May 1, 2017, with Cyxtera and all of Cyxtera’s subsidiaries and controlled affiliates as of such date, including Legacy Appgate (collectively, the “Company Group”). The Service Providers include BC Partners, Inc. (“BC Partners”), Medina Capital Advisors, LLC (“MCA”), LDEF Series B-1 LLC – Series 17 (“LDEF”) and Star Series LLC – Series 38 (“Star” and, together with LDEF, “Longview”). Raymond Svider and Fahim Ahmed, who serve as Appgate directors, also serve as partners of BC Partners. BC Partners indirectly owns an approximately 62.2% equity interest in SIS Holdings. MCA is indirectly owned and controlled by Manual D. Medina, Appgate’s Executive Chairman, and is an affiliate of Medina Capital Partners, LP (“Medina Capital”), which indirectly owns an approximately 20.9% equity interest in SIS Holdings. In addition, (i) Barry Field, who serves as Appgate’s Chief Executive Officer and as a director, is a partner at Medina Capital and (ii) Rene A. Rodriguez, who serves as Appgate’s Chief Financial Officer, is the Chief Financial Officer and partner of Medina Capital. Longview owns an approximately 5.7% equity interest in SIS Holdings.
Under the Services Agreement, the Service Providers agreed to provide members of the Company Group with certain executive and management, financial, consulting, human resources and advisory services as requested by members of the Company Group from time to time. Legacy Appgate agreed to pay the Service Providers an annual service fee to be paid in equal quarterly installments. Legacy Appgate was allocated $0.1 million in each of 2020 and 2019 under the Services Agreement through the Intercompany Master Services Agreement described below. The Service Providers waived all fees under the Services Agreement for 2021. The Services Agreement was terminated on July 29, 2021.
Intercompany Master Services Agreement Fee
In connection with the formation of Cyxtera in 2017, the Company Group entered into the Intercompany Master Services Agreement. Under the Intercompany Master Services Agreement, Cyxtera Management, Inc., a wholly-owned subsidiary of Cyxtera (the “Management Company”), agreed to provide certain services to the other members of the Company Group from time to time, including financial, accounting, administrative, facilities and other services. In 2019, approximately $21.3 million was allocated to Legacy Appgate under the Intercompany Master Services Agreement. The Intercompany Master Services Agreement was terminated on July 29, 2021.
Transition Services Agreement
Upon consummation of the Cyxtera Spin-Off, Legacy Appgate and the Management Company entered into a transition services agreement (the “Transition Services Agreement”), pursuant to which the Management Company provided certain transition services to Legacy Appgate, and Legacy Appgate provided certain transition services to the Management Company. The term under the Transition Services Agreement commenced on January 1, 2020 and ended on June 30, 2021. Substantially all of the obligations under the Transition Services Agreement ceased on December 31, 2020.
During 2020, the Management Company charged Legacy Appgate $4.2 million for services rendered under the Transition Services Agreement. During 2020, Legacy Appgate charged the Management Company $0.3 million of fees for services provided to the Management Company and its affiliates by Legacy Appgate. For January 1, 2021 through June 30, 2021, the Management Company charged Legacy Appgate $2.7 million for services provided to Legacy Appgate and Legacy Appgate charged the Management Company $0.1 million for services provided to the Management Company and its affiliates.
Promissory Notes
On March 31, 2019, Legacy Appgate issued promissory notes to each of Cyxtera and the Management Company (collectively, the “Promissory Notes”) evidencing funds borrowed at such time by Legacy Appgate from each of Cyxtera and the Management Company, as well as potential future borrowings. The Promissory Notes had a combined initial aggregate principal amount of $95.2 million and provided for additional borrowings during the term of the Promissory Notes for additional amounts not to exceed approximately $52.5 million in the aggregate (approximately $147.7 million including the initial aggregate principal amount). Interest accrued on the unpaid principal balance of the Promissory Notes at a rate per annum equal to 3%; provided, that with respect to any day during the period from the date of the Promissory Notes through December 31, 2019, interest was calculated assuming that the unpaid principal balance of the Promissory Notes on such day was the unpaid principal amount of the notes on the last calendar day of the quarter in which such day occurs. Interest was payable upon the maturity date of the Promissory Notes. Each of the Promissory Notes had an initial maturity date of March 30, 2020 and was extended through March 30, 2021 by amendments entered into effective as of March 30, 2020.
During 2019 and 2020, Legacy Appgate received advances of $43.1 million and $19.4 million, respectively, under the Promissory Notes. The outstanding principal and interest under the Promissory Notes was $153.8 million as of December 31, 2020.
On February 8, 2021, Legacy Appgate repaid Cyxtera the full amount of the Promissory Note held by Cyxtera and made a partial repayment to the Management Company on the then accumulated principal and interest under the Promissory Note held by the Management Company. On that same date, the Management Company issued a payoff letter to Legacy Appgate extinguishing the balance remaining unpaid following such repayment.
Related Party Transactions related to the Merger
The Merger
On February 8, 2021, Newtown Lane entered into the Merger Agreement with Merger Sub and Legacy Appgate. Mr. Ledecky, who is an Appgate director, served as President and sole director and held a 69.1% indirect equity ownership interest in Newtown Lane at the time the Merger Agreement was executed. Pursuant to the Merger Agreement, on October 12, 2021, Merger Sub merged with and into Legacy Appgate, with Legacy Appgate being the surviving entity of the Merger and a wholly-owned subsidiary of the Company. Following the Merger, Newtown Lane changed its name to Appgate, Inc.
Merger Registration Rights Agreement
Reference is made to the description of the Merger Registration Rights Agreement set forth under Item 1.01 of this Report, which is incorporated herein by reference. The description of the Merger Registration Rights Agreement therein is qualified in its entirety by the full text of the Merger Registration Rights Agreement, a copy of which is filed as Exhibit 10.1 to this Report, and incorporated herein by reference.
Commercial Related Person Transactions with Cyxtera
Appgate maintains a number of ordinary course commercial relationships, both as a customer and service provider, with Cyxtera. For instance, in 2020 and 2021, Cyxtera purchased certain cybersecurity products and services from Legacy Appgate, including licenses for Legacy Appgate cybersecurity software and training. For 2020 and the six months ended June 30, 2021, Legacy Appgate charged Cyxtera $143,990 and $5,000, respectively, for those products and services. In 2020 and 2021, Cyxtera provided Legacy Appgate certain data center colocation and CXD services. For 2020 and the six months ended June 30, 2021, Cyxtera charged Legacy Appgate $167,960 and $200,490, respectively, for those services. Messrs. Svider, Ahmed and Medina serve on the boards of directors of the Company and Cyxtera and SIS Holdings owns approximately 64.7% of Cyxtera’s outstanding common stock.
Director Related Party Transactions
Transactions with Director Affiliated Companies
Messrs. Svider and Ahmed, who serve as directors of the Company and SIS Holdings GP LLC, the sole general partner of SIS Holdings, are also members of the board of directors of Chewy, Inc. (“Chewy”), an American online retailer of pet food and other pet-related products. During 2020 and the six months ended June 30, 2021, Legacy Appgate charged Chewy $129,600 and $278,100, respectively, under contracts for certain cybersecurity products provided by Legacy Appgate to Chewy.
Other Related Party Transactions
CenturyLink Communications, LLC (“CenturyLink”), an approximate 10.4% owner of SIS Holdings and, as a result, an indirect beneficial owner of the Company, is a reseller of certain of Legacy Appgate’s products and services. During 2020 and the six months ended June 30, 2021, Legacy Appgate charged CenturyLink $207,680 and $389,210, respectively, under contracts for certain cybersecurity products provided by Legacy Appgate to CenturyLink for resale by CenturyLink to end users.
Director and Officer Indemnification
Reference is made to the disclosure set forth under the heading “Indemnification of Directors and Officers” in Item 2.01 of this Report, which is incorporated herein by reference.
Legal Proceedings
From time to time, we may be subject to legal proceedings and claims arising in the ordinary course of business. We are not presently party to any legal proceedings the resolution of which would have a material adverse effect on our financial condition, results of operations or liquidity.
Market Price of and Dividends on the Registrant’s Common Equity and Related Stockholder Matters
Price Range of Securities and Dividends
As of the Closing Date and following the consummation of the Merger, the Company had 131,793,870 shares of Company’s Common Stock issued and outstanding held of record by 52 holders.
Prior to the Closing, the Company’s Common Stock was listed on the OTC Markets under the ticker “NWTN”. Upon the Closing, the Company’s Common Stock was listed on the OTC Markets under the symbol “NTWN”, but was subsequently updated to “APGT” on October 14, 2021.
The Company has not paid any cash dividends on shares of its Common Stock to date. The payment of cash dividends by the Company in the future will be dependent upon the Company’s revenues and earnings, if any, capital requirements and general financial condition. The payment of any cash dividends will be within the discretion of the Board at such time. The Company’s ability to declare dividends may also be limited by restrictive covenants pursuant to any debt financing agreements.
Holders of Record
As of the Closing and following the completion of the Transactions, the Company had 131,793,870 shares of Company’s Common Stock issued and outstanding held of record by 52 holders. Such amounts do not include DTC participants or beneficial owners holding shares through nominee names.
Securities Authorized for Issuance Under Equity Compensation Plans
Effective upon Closing, the Company’s stockholders approved the 2021 Plan and the material terms thereunder, including the authorization of the initial share reserve thereunder.
Reference is made to the description of the 2021 Plan set forth under Item 5.02 of this Report, which is incorporated herein by reference. The description of the 2021 Plan therein is qualified in its entirety by the full text of the 2021 Plan, which is attached hereto as Exhibit 10.11, and is incorporated herein by reference.
Recent Sales of Unregistered Securities
Reference is made to the disclosure set forth under Item 3.02 of this Report, which is incorporated herein by reference.
Description of Registrant’s Securities to be Registered
Reference is made to the summary of the Company’s Common Stock under the headings “A&R Charter and A&R Bylaws—Increase in Authorized Number of Shares of Common Stock” and “A&R Charter and A&R Bylaws— General Description of Common Stock” under Item 5.03 of this Report, all of which is incorporated herein by reference.
Indemnification of Directors and Officers
Section 102(b)(7) of the Delaware General Corporation Law (the “DGCL”) enables a corporation in its certificate of incorporation, or an amendment thereto, to eliminate or limit the personal liability of a director to the corporation or its stockholders for monetary damages for violations of the director’s fiduciary duty as a director, except (i) for any breach of the director’s duty of loyalty to the corporation or its stockholders, (ii) for acts or omissions not in good faith or which involve intentional misconduct or a knowing violation of law, (iii) pursuant to Section 174 of the DGCL (providing for director liability with respect to unlawful payment of dividends or unlawful stock purchases or redemptions) or (iv) for any transaction from which a director derived an improper personal benefit. Our A&R Charter provides for such limitation of liability.
Our A&R Charter and A&R Bylaws (each as defined herein) provide that, to the fullest extent permitted by the DGCL, a member of the Board shall not be personally liable to the Company or its stockholders for monetary damages for breach of fiduciary duty owed to the Company its stockholders.
Reference is also made to the disclosure set forth in Item 1.01 of this Report under the heading “Indemnification Agreements,” which is incorporated herein by reference.
Changes in and Disagreements with Accountants on Accounting and Financial Disclosure
Reference is made to the disclosure set forth under Item 4.01 of this Report relating to the change in Newtown Lane’s certifying accountant, which is incorporated herein by reference.
Item 2.03 Creation of a Direct Financial Obligation or an Obligation under an Off-Balance Sheet Arrangement of a Registrant.
Reference is made to the disclosure set forth under Item 1.01 of this Report relating to Magnetar and the Notes, which is incorporated herein by reference.
Item 3.02 Unregistered Sale of Equity Securities.
On the Closing Date, in connection with the Merger, the Company issued 117,149,920 shares of Common Stock to SIS Holdings, the sole stockholder of Legacy Appgate immediately prior to the Closing. Reference is made to the disclosures relating to the Merger set forth under Item 1.01 and Item 2.01 of this Report, which disclosure is incorporated herein by reference.
Prior to the Closing, Legacy Appgate issued the Notes. The disclosure under Item 1.01 of this Report relating to the Notes is incorporated herein by reference.
The foregoing securities were issued under Section 4(a)(2) of the Securities Act of 1933, as amended (the “Securities Act”), as a transaction not requiring registration under Section 5 of the Securities Act. The parties receiving the securities represented their intentions to acquire the securities for investment only and not with a view to or for sale in connection with any distribution, and appropriate restrictive legends were affixed to the certificates representing the securities (or reflected in restricted book entry with the Company’s transfer agent). The parties also had adequate access, through business or other relationships, to information about the Company and Legacy Appgate, as applicable.
Item 3.03 Material Modification to Rights of Security Holders.
The information set forth in Item 5.03 of this Report is incorporated herein by reference.
Item 4.01 Change in Registrant’s Certifying Accountant.
On October 12, 2021, the Board approved the engagement of BDO USA, LLP (“BDO”) as the Company’s independent registered public accounting firm to audit the Company’s consolidated financial statements for the year ended December 31, 2021. BDO served as the independent registered public accounting firm of Legacy Appgate prior to the Merger. Accordingly, Liggett & Webb P.A. (“Liggett & Webb”), Newtown Lane’s independent registered public accounting firm prior to the Merger, was informed that it would be replaced by BDO as the Company’s independent registered public accounting firm following the consummation of the Merger on October 12, 2021.
Liggett & Webb’s audit reports on the financial statements for the years ended March 31, 2021 and 2020 did not provide an adverse opinion or disclaimer of opinion to the Company’s financial statements, nor modify its opinion as to uncertainty, audit scope or accounting principles except for the inclusion of an explanatory paragraph related to substantial doubt about the Company’s ability to continue as a going concern.
During the fiscal years ended March 31, 2021 and 2020, and the subsequent interim period through October 12, 2021, there were: (i) no disagreements within the meaning of Item 304(a)(1)(iv) of Regulation S-K and the related instructions between the Company and Liggett & Webb on any matters of accounting principles or practices, financial statement disclosure, or auditing scope or procedure which, if not resolved to Liggett & Webb’s satisfaction, would have caused Liggett & Webb to make reference thereto in their reports; and (ii) no “reportable events” within the meaning of Item 304(a)(1)(v) of Regulation S-K.
The Company provided Liggett & Webb with a copy of the foregoing disclosures and has requested that Liggett & Webb furnish the Company with a letter addressed to the SEC stating whether it agrees with the statements made by the Company set forth above. A copy of Liggett & Webb’s letter, dated October 15, 2021, is filed as Exhibit 16.1 to this Report.
Item 5.01 Change in Control of the Registrant.
The information set forth above under Item 1.01 and Item 2.01 of this Report is incorporated herein by reference.
Item 5.02 Departure of Directors or Certain Officers; Election of Directors; Appointment of Certain Officers; Compensatory Arrangements of Certain Officers.
The information set forth above in the sections titled “Directors and Executive Officers,” “Executive Compensation,” “Certain Relationships and Related Transactions, and Director Independence” and “Indemnification of Directors and Officers” in Item 2.01 of this Report is incorporated herein by reference.
2021 Plan
On or about September 6, 2021, Newtown Lane’s then stockholder holding a majority of Newtown Lane’s issued and outstanding shares of Common Stock and Newtown Lane’s then sole director approved the adoption of a new public company equity incentive plan, which we refer to as the 2021 Plan. The 2021 Plan became effective immediately upon the Closing.
The 2021 Plan is designed to allow the Company to make equity-based incentive awards to officers, employees, directors and other key persons (including consultants). The Board anticipates that providing such persons with a direct stake in the Company, following the Merger, will assure a closer alignment of the interests of such individuals with those of the Company and its stockholders, thereby stimulating their efforts on the Company’s behalf and strengthening their desire to remain with the Company.
The 2021 Plan provides for a share issuance pool equal to 11,022,170 shares of Common Stock as of the effective date of the 2021 Plan, which we refer to as the Share Pool Limit. The Share Pool Limit is subject to adjustment in the event of a stock split, stock dividend or other change in the Company’s capitalization. The maximum aggregate number of shares of Common Stock that may be issued upon exercise of incentive stock options under the 2021 Plan shall not exceed the Share Pool Limit.
If any award under the 2021 Plan is forfeited, expires or otherwise terminates without issuance of the shares of Common Stock in respect of such award, or if any award is settled for cash, then the shares to which those awards were subject, shall, to the extent of such forfeiture, expiration, termination, non-issuance or cash settlement, again be available for delivery with respect to awards under the 2021 Plan. It should be noted that Shares used to pay the exercise price or tax withholding associated with awards will count against and, therefore, will not be returned to the pool.
The 2021 Plan contains a limitation whereby the value of all awards under the 2021 Plan granted to any non-employee director for services as a non-employee director in any fiscal year may not exceed $750,000.
The 2021 Plan is administered by the Compensation Committee of the Board, or, if at any such time there is no Compensation Committee, the 2021 Plan will be administered by the Board. For purposes of this description of the 2021 Plan, references to the Compensation Committee shall instead refer to the Board in the event that there is no Compensation Committee. The Compensation Committee will have full power to select, from among the individuals eligible for awards, the individuals to whom awards will be granted, to make any combination of awards to participants, and to determine the specific terms and conditions of each award, subject to the provisions of the 2021 Plan. The Compensation Committee may delegate to the chief executive officer or any other officer the authority to grant stock options and other awards to employees who are not subject to the reporting and other provisions of Section 16 of the Exchange Act, subject to certain limitations and guidelines. Persons eligible to participate in the 2021 Plan will be those full or part-time employees, non-employee directors and other key service providers (including consultants) as selected from time to time by the Compensation Committee in its discretion.
Under the 2021 Plan, the Compensation Committee is authorized to grant stock options, stock appreciation rights, restricted stock, restricted stock units, other equity-based awards and cash incentive awards as described below. Awards may be subject to a combination of time and performance-based vesting conditions, as may be determined by the Compensation Committee.
The 2021 Plan permits the granting by the Compensation Committee of both options to purchase Common Stock intended to qualify as incentive stock options under Section 422 of the Code and options that do not so qualify. Options granted under the 2021 Plan will be non-qualified options if they fail to qualify as incentive options or exceed the annual limit on incentive stock options. Incentive stock options may only be granted to employees of the Company and its subsidiaries. Non-qualified options may be granted to any persons eligible to receive incentive options and to non-employee directors and key persons. The option exercise price of each option will be determined by the Compensation Committee but may not be less than 100% of the fair market value of the Common Stock on the date of grant unless the option is granted (i) pursuant to a transaction described in, and in a manner consistent with, Section 424(a) of the Code or (ii) to individuals who are not subject to U.S. income tax. The term of each option will be fixed by the Compensation Committee and may not exceed ten years following the date of grant. The Compensation Committee will determine at what time or times each option may be exercised, including whether the vesting of such options may be accelerated under any given circumstances.
Upon exercise of options, the option exercise price must be paid in full either in cash, by certified or bank check or other instrument acceptable to the Compensation Committee or by delivery (or attestation to the ownership) of shares of Common Stock that are beneficially owned by the optionee for at least six months or were purchased in the open market. Subject to applicable law, the exercise price may also be delivered by a broker pursuant to irrevocable instructions to the broker from the optionee. In addition, the Compensation Committee may permit non-qualified options to be exercised using a net exercise feature, which reduces the number of shares issued to the optionee by the number of shares with a fair market value equal to the aggregate exercise price.
The Compensation Committee may award stock appreciation rights subject to such conditions and restrictions as it may determine. Stock appreciation rights entitle the recipient to shares of Common Stock, or cash, equal to the value of the appreciation in our stock price over the exercise price. The exercise price may not be less than 100% of the fair market value of Common Stock on the date of grant. The term of each stock appreciation right will be fixed by the Compensation Committee and may not exceed ten years following the date of grant. The Compensation Committee will determine at what time or times each stock appreciation right may be exercised.
The Compensation Committee may award restricted shares of Common Stock and restricted stock units to participants subject to such conditions and restrictions as it may determine. These conditions and restrictions may include the achievement of certain performance goals and/or continued employment with the Company through a specified vesting period. The Compensation Committee may also grant shares of Common Stock that are free from any restrictions under the 2021 Plan. Unrestricted stock may be granted to a participant in recognition of past services or for other valid consideration and may be issued in lieu of cash compensation due to such participant. The Compensation Committee may grant dividend equivalent rights to participants that entitle the recipient to receive credits for dividends that would be paid if the recipient had held a specified number of shares of Common Stock.
The 2021 Plan provides that upon the effectiveness of a “change in control,” as defined in the 2021 Plan, an acquirer or successor entity may assume, continue or substitute outstanding awards under the 2021 Plan or cash-out awards. The Compensation Committee has the discretion to accelerate vesting of awards.
Participants in the 2021 Plan are responsible for the payment of any federal, state or local taxes that the Company is required by law to withhold upon the exercise of options or stock appreciation rights or vesting of other awards. Subject to approval by the Compensation Committee, participants may elect to have up to the maximum tax withholding obligations satisfied by authorizing the Company to withhold shares of Common Stock to be issued pursuant to the exercise or vesting of such award.
The Compensation Committee may make such adjustments to awards as it considers appropriate to preserve their value in the event of an extraordinary dividend, recapitalization, stock split, spin-off or any other event that constitutes an equity restructuring, including adjustments to the terms of (i) the number of shares with respect to which awards may be granted under the 2021 Plan and (ii) outstanding awards (including adjustments to exercise prices of options and other affected terms of awards).
The Compensation Committee may (i) cause the cancellation of any award, (ii) require reimbursement of any award by a participant or beneficiary, and (iii) effect any other right of recoupment of equity or other compensation provided under the 2021 Plan or otherwise in accordance with any company policies that currently exist or that may from time to time be adopted or modified in the future by the Board or the Compensation Committee and/or applicable law, each of which is referred to as a “clawback policy.” In addition, a participant may be required to repay to the Company certain previously paid compensation, whether provided under the 2021 Plan or an award agreement or otherwise, in accordance with any clawback policy. By accepting an award, a participant is also agreeing to be bound by any existing or future clawback policy adopted by the Board or the Compensation Committee, or any amendments that may from time to time be made to the clawback policy in the future by the Board or the Compensation Committee in its discretion (including without limitation any clawback policy adopted or amended to comply with applicable laws or stock exchange requirements) and is further agreeing that all of the participant’s award agreements may be unilaterally amended by the Compensation Committee, without the participant’s consent, to the extent that Compensation Committee in its discretion determines to be necessary or appropriate to comply with any clawback policy.
Except as otherwise provided by the Compensation Committee or set forth in an award agreement, awards will not be transferable except by will or by laws of descent and distribution. In no event may any award be transferred to a third party in exchange for value without the consent of the Company’s stockholders prior to vesting.
The Board may amend or discontinue the 2021 Plan, and the Compensation Committee may amend or cancel outstanding awards for purposes of satisfying changes in law or any other lawful purpose, but no such action may adversely affect rights under an award without the holder’s consent. Certain amendments to the 2021 Plan require the approval of the Company’s stockholders.
The foregoing description of the 2021 Plan is qualified in its entirety by the full text of the 2021 Plan, which is attached hereto as Exhibit 10.11, and is incorporated herein by reference.
Item 5.03 Amendments to Articles of Incorporation or Bylaws; Change in Fiscal Year.
Amendments to Articles of Incorporation or Bylaws
On October 12, 2021, in connection with the consummation of the Transactions, the Company amended and restated its certificate of incorporation effective as of the Closing (as amended, the “A&R Charter”). Effective immediately following the Closing, the Company amended and restated its bylaws (as amended, the “A&R Bylaws”).
The following summary describes the material provisions of our A&R Charter and A&R Bylaws and is qualified in its entirety by the full text of the A&R Charter and A&R Bylaws, which are attached hereto as Exhibit 3.1 and Exhibit 3.2 to this Report, respectively, and are incorporated herein by reference.
General
Our purpose will be to engage in any lawful act or activity for which corporations may now or hereafter be organized under the DGCL.
Certain provisions of the A&R Charter and A&R Bylaws summarized below may be deemed to have an anti-takeover effect and may delay or prevent a tender offer or takeover attempt that a stockholder might consider in its best interest, including those attempts that might result in a premium over the market price for the shares of Common Stock.
The Company filed the A&R Charter with the Secretary of State of the State of Delaware. Concurrently with the filing of the A&R Charter, the Company notified the Financial Industry Regulatory Authority of the proposed name change and, on October 14, 2021, had its trading symbol for its Common Stock updated to “APGT”.
Name Change
Because the Company’s business operations will generally be conducted through Legacy Appgate (which does business as “AppGate”), the Company changed its name to “Appgate, Inc.”.
Exclusive Forum
The A&R Charter designates that, unless we consent in writing to the selection of an alternative forum, the sole and exclusive forum, to the fullest extent permitted by law, for (1) any derivative action or proceeding brought on our behalf, (2) any action asserting a claim of breach of a fiduciary duty owed by any of our current or former directors, officers or other employees or stockholders to us or our stockholders, creditors or other constituents, or a claim of aiding and abetting any such breach of fiduciary duty, (3) any action asserting a claim against us or any of our directors or officers or other employees or stockholders arising pursuant to, or any action to interpret, apply, enforce any right, obligation or remedy under or determine the validity of, any provision of the DGCL or our A&R Charter or A&R Bylaws or as to which the DGCL confers jurisdiction on the Court of Chancery of the State of Delaware, (4) any action asserting a claim that is governed by the internal affairs doctrine, or (5) any other action asserting an “internal corporate claim” under the DGCL shall be the Court of Chancery of the State of Delaware (or, if and only if the Court of Chancery does not have subject matter jurisdiction, another state court sitting in the State of Delaware or, if and only if neither the Court of Chancery nor any state court sitting in the State of Delaware has subject matter jurisdiction, then the federal district court for the District of Delaware) (the “Delaware Forum Provision”).
Notwithstanding the foregoing, the A&R Charter provides that the Delaware Forum Provision will not apply to any actions arising under the Securities Act or the Exchange Act. Any person or entity purchasing or otherwise acquiring any interest in our securities shall be deemed to have notice of and consented to this provision. Although we believe these provisions benefit us by providing increased consistency in the application of Delaware law for the specified types of actions and proceedings, the provisions may have the effect of discouraging lawsuits against us or our directors and officers.
Additionally, the A&R Charter provides that unless the Company consents in writing to the selection of an alternative forum, the federal district court for the District of Delaware shall, to the fullest extent permitted by law, be the exclusive forum for the resolution of any complaint asserting a cause of action arising under the Securities Act. Any person or entity purchasing or otherwise acquiring any interest in shares of capital stock of the Company are deemed to have notice of and consented to this provision. The Supreme Court of Delaware has held that this type of exclusive federal forum provision is enforceable. There may be uncertainty, however, as to whether courts of other jurisdictions would enforce such provision, if applicable.
Increase in Authorized Number of Shares of Common Stock
The A&R Charter authorizes capital stock consisting of:
| | ● | 270,000,000 shares of Common Stock, par value $0.001 per share; and |
| | ● | 1,000,000 shares of Preferred Stock, par value $0.001 per share. |
The increase in the authorized number of shares of Common Stock was necessary for the Company to consummate the Merger (and to issue the shares that may be required to be issued to holders of Notes) and have additional authorized shares of Common Stock for financing its business, for acquiring other businesses, for grants and issuances under the 2021 Plan, for forming strategic partnerships and alliances and for stock dividends and stock splits. Notwithstanding the foregoing, authorized but unissued shares of Common Stock may enable the Board to render it more difficult or to discourage an attempt to obtain control of the Company and thereby protect continuity of or entrench its management, which may adversely affect the market price of the Company’s Common Stock. If in the due exercise of its fiduciary obligations, for example, the Board were to determine that a takeover proposal were not in the best interests of the Company, such shares could be issued by the Board without stockholder approval in one or more private placements or other transactions that might prevent or render more difficult or make more costly the completion of any attempted takeover transaction by diluting voting or other rights of the proposed acquirer or insurgent stockholder group, by creating a substantial voting block in institutional or other hands that might support the position of the incumbent board of directors, by effecting an acquisition that might complicate or preclude the takeover, or otherwise.
General Description of Common Stock
Voting Rights. Each share of our Common Stock entitles its owner to one vote on all matters submitted to a vote of our stockholders, including the election of directors. Under our A&R Charter and A&R Bylaws, our stockholders do not have cumulative voting rights. Because of this, the holders of a majority of the shares of Common Stock entitled to vote in any election of directors will be able to elect all of the directors standing for election, if they should so choose.
Dividend Rights. The holders of our Common Stock are entitled to ratably receive dividends, when, as and if declared by our Board, in its discretion, from funds legally available for the payment of dividends.
Liquidation Rights. If we liquidate, dissolve or wind up, the owners of our Common Stock are entitled to share proportionately in our assets, if any, legally available for distribution to stockholders, but only after prior satisfaction of all outstanding debts and other liabilities and the payment of liquidation preferences, if any, on any outstanding preferred stock.
Other Rights and Preferences. Our Common Stock does not have preemptive rights, sinking fund provisions or subscription, redemption or conversion privileges, and it will not be subject to any further calls or assessments by us. All outstanding shares of our Common Stock are fully paid and non-assessable. The rights, powers, preferences and privileges of holders of our Common Stock are subject to those of the holders of any shares of our preferred stock we may authorize and issue in the future.
General Description of Preferred Stock
Our A&R Charter authorizes our Board, without further stockholder approval, to: (i) issue preferred stock in one or more series; (ii) establish the number of shares to be included in each such series; and (iii) fix the designations, powers, preferences and rights of the shares of each series and any qualifications, limitations or restrictions on those shares. The Board may establish a class or series of preferred stock with preferences, powers and rights (including voting rights) senior to the rights of the holders of our Common Stock. If we issue any of our preferred stock, it may have the effect of delaying, deferring or preventing a change in control.
Dividends
Declaration and payment of any dividend is subject to the discretion of our Board. The time and amount of dividends will be dependent upon, among other things, our business prospects, results of operations, financial condition, cash requirements and availability, debt repayment obligations, capital expenditure needs, contractual restrictions, covenants in the agreements governing our current and future indebtedness, industry trends, the provisions of Delaware law affecting the payment of dividends and distributions to stockholders and any other factors or considerations our Board may regard as relevant. We currently intend to retain all available funds and any future earnings to fund the development and growth of our business, and therefore do not anticipate paying any cash dividends on our Common Stock in the foreseeable future.
Anti-Takeover Provisions
Our A&R Charter and A&R Bylaws contain provisions that may delay, defer or discourage another party from acquiring control of us, including our classified Board and our ability to issue new series of preferred stock without stockholder approval. We expect that these provisions, which are summarized below, will discourage coercive takeover practices or inadequate takeover bids. These provisions are also designed to encourage persons seeking to acquire control of us to first negotiate with our Board, which we believe may result in an improvement of the terms of any such acquisition in favor of our stockholders. However, they also give our Board the power to discourage acquisitions that some stockholders may favor.
Authorized but Unissued Shares; Undesignated Preferred Stock. The authorized but unissued shares of our Common Stock is available for future issuance without stockholder approval except as required by law or by any stock exchange on which our Common Stock may be listed. These additional shares may be utilized for a variety of corporate purposes, including future public offerings to raise capital, acquisitions and employee benefit or compensation plans. In addition, our Board may authorize, without stockholder approval, the issuance of undesignated preferred stock with voting rights or other rights or preferences designated from time to time by our Board. The existence of authorized but unissued shares of Common Stock or preferred stock may enable our Board to render more difficult or to discourage an attempt to obtain control of us by means of a merger, tender offer, proxy contest or otherwise.
Board Classification. Our A&R Charter provides that our Board will be divided into three classes of directors, with the classes to be as nearly equal in number as possible, and with the directors serving three-year terms. As a result, approximately one-third of our Board will be elected each year. The classification of directors will have the effect of making it more difficult for stockholders to change the composition of our Board. Our A&R Charter and A&R Bylaws provide that, subject to any rights of holders of preferred stock to elect additional directors under specified circumstances, the number of directors will be fixed from time to time exclusively pursuant to a resolution adopted by our Board.
No Cumulative Voting. Our A&R Charter provides that stockholders are not permitted to cumulate votes in the election of directors.
Special Meetings of Stockholders. Our A&R Bylaws provides that special meetings of our stockholders may be called, prior to the Trigger Event (as defined in the A&R Charter), only by or at the direction of our Board or our Chairman at the request of holders of not less than a majority of the combined voting power of our Common Stock, and, from and after the Trigger Event, only by or at the direction of our Board or our Chairman.
Stockholder Action by Written Consent. Pursuant to Section 228 of the DGCL, any action required to be taken at any annual or special meeting of the stockholders may be taken without a meeting, without prior notice and without a vote if a consent or consents in writing, setting forth the action so taken, is signed by the holders of outstanding stock having not less than the minimum number of votes that would be necessary to authorize or take such action at a meeting at which all shares of our stock entitled to vote thereon were present and voted, unless our certificate of incorporation provides otherwise. Our A&R Charter precludes stockholder action by written consent from and after the Trigger Event.
Advance Notice Requirements for Stockholder Proposals and Nomination of Directors. Our A&R Bylaws require stockholders seeking to bring business before an annual meeting of stockholders, or to nominate individuals for election as directors at an annual or special meeting of stockholders, to provide timely notice in writing. To be timely, a stockholder’s notice will need to be sent to and received by our Secretary both (1) at our principal executive offices by hand delivery, overnight courier service, or by certified or registered mail, return receipt required, and (2) by electronic mail, as provided in the A&R Bylaws, no later than the close of business on the 90th day, nor earlier than the close of business on the 120th day, prior to the anniversary of the immediately preceding annual meeting of stockholders. However, in the event that the annual meeting is called for a date that is not within 30 days before or 70 days after the anniversary of the immediately preceding annual meeting of stockholders, or if no annual meeting was held in the preceding year, such notice will be timely only if received no earlier than the close of business on the 120th day prior to the annual meeting and no later than the close of business on the later of the 90th day prior to such annual meeting and the tenth day following the date on which a public announcement of the date of the annual meeting was made by us. Our A&R Bylaws also specify requirements as to the form and content of a stockholder’s notice. These provisions may preclude our stockholders from bringing matters before our annual meeting of stockholders or from making nominations for directors at our meetings of stockholders. These provisions may also discourage or deter a potential acquirer from conducting a solicitation of proxies to elect the potential acquirer’s own slate of directors or otherwise attempting to obtain control of the Company.
Removal of Directors; Vacancies. Under the DGCL, unless otherwise provided in our A&R Charter, directors serving on a classified board may be removed by the stockholders only for cause. Our A&R Charter provides that from and after the Trigger Event, directors may only be removed with cause, and only by the affirmative vote of holders of at least 66 2/3% in voting power of all the then-outstanding shares of Common Stock of the Company entitled to vote thereon. In addition, our A&R Charter provides that from and after the Trigger Event, any newly created directorship on our Board that results from an increase in the number of directors and any vacancy occurring in our Board may only be filled by a majority of the directors then in office, although less than a quorum, or by a sole remaining director (and not by the stockholders).
Supermajority Provisions. Our A&R Charter and A&R Bylaws provide that our Board is expressly authorized to alter, amend, rescind or repeal, in whole or in part, our A&R Bylaws without a stockholder vote in any matter not inconsistent with Delaware law and our A&R Charter. From and after the Trigger Event, in addition to any vote of the holders of any class or series of capital stock of our Company required therein, our A&R Bylaws or applicable law, any amendment, alteration, rescission or repeal of our A&R Bylaws by our stockholders will require the affirmative vote of the holders of at least 75% in voting power of all the then-outstanding shares of stock of our Company entitled to vote thereon, voting together as a single class.
The DGCL provides generally that the affirmative vote of a majority of the outstanding shares entitled to vote thereon, voting together as a single class is required to amend a corporation’s certificate of incorporation unless the certificate of incorporation requires a greater percentage. Our A&R Charter provides that the following provisions in our A&R Charter may be amended, altered, repealed or rescinded only by the affirmative vote of the holders of at least 75% in voting power of all the then-outstanding shares of stock of our Company entitled to vote thereon, voting together as a single class:
| ● | the provision requiring a 75% supermajority vote for stockholders to amend our A&R Bylaws; |
| ● | the provisions providing for a classified board of directors (the election and term of our directors); |
| ● | the provisions regarding removal of directors; |
| ● | the provisions regarding stockholder action by written consent; |
| ● | the provisions regarding calling special meetings of stockholders; |
| ● | the provisions regarding filling vacancies on our Board and newly created directorships; |
| ● | the provisions regarding competition and corporate opportunities; |
| ● | the provisions regarding Section 203 of the DGCL; |
| ● | the provisions eliminating monetary damages for breaches of fiduciary duty by a director and governing forum selection; and |
| ● | the amendment provision requiring that the above provisions be amended only with a 75% supermajority vote. |
Limitations on Liability and Indemnification of Officers and Directors
Section 102(b)(7) of the DGCL enables a corporation in its certificate of incorporation, or an amendment thereto, to eliminate or limit the personal liability of a director to the corporation or its stockholders for monetary damages for violations of the director’s fiduciary duty as a director, except (i) for any breach of the director’s duty of loyalty to the corporation or its stockholders, (ii) for acts or omissions not in good faith or which involve intentional misconduct or a knowing violation of law, (iii) pursuant to Section 174 of the DGCL (providing for director liability with respect to unlawful payment of dividends or unlawful stock purchases or redemptions) or (iv) for any transaction from which a director derived an improper personal benefit. Our A&R Charter provides for such limitation of liability.
Our A&R Charter and A&R Bylaws provide that, to the fullest extent permitted by the DGCL, a member of the Board shall not be personally liable to the Company or its stockholders for monetary damages for breach of fiduciary duty owed to the Company its stockholders.
Corporate Opportunity Doctrine
Our A&R Charter provides that, to the fullest extent permitted by law (including without limitation Section 122(17) of the DGCL), the doctrine of corporate opportunity, or any other analogous doctrine, shall not apply with respect to us or any of our officers or directors, or any of our or their respective affiliates, in circumstances where the application of any such doctrine would conflict with any fiduciary duties or contractual obligations we or they may have as of the date of the A&R Charter or in the future. Our A&R Charter also provides that we renounce any expectancy that any of our directors or officers, or any of their respective affiliates, will offer any such corporate opportunity of which he or she may become aware to us; provided, however, that the doctrine of corporate opportunity shall apply with respect to any of our directors or officers only with respect to a corporate opportunity that was offered to such person solely and exclusively in his or her capacity as a director or officer of the Company, and (i) such opportunity is one that we are legally and contractually permitted to undertake and would otherwise be reasonable for us to pursue and (ii) to the extent the director or officer is permitted to refer that opportunity to us without violating any other legal obligation.
Business Combination with Interested Stockholders
We have opted out of Section 203 of the DGCL; however, our A&R Charter contains similar provisions providing that we may not engage in certain “business combinations” with any “interested stockholder” for a three-year period following the time that the stockholder became an interested stockholder, unless:
| ● | prior to such time, our Board approved either the business combination or the transaction which resulted in the stockholder becoming an interested stockholder; |
| ● | upon consummation of the transaction that resulted in the stockholder becoming an interested stockholder, the interested stockholder owned at least 85% of our voting stock outstanding at the time the transaction commenced, excluding certain shares; or |
| ● | at or subsequent to that time, the business combination is approved by our Board and by the affirmative vote of holders of at least 66 2/3% of our outstanding voting stock that is not owned by the interested stockholder. |
Generally, a “business combination” includes a merger, asset or stock sale or other transaction resulting in a financial benefit to the interested stockholder. Subject to certain exceptions, an “interested stockholder” is a person who, together with that person’s affiliates and associates, owns, or within the previous three years owned, 15% or more of our outstanding voting stock. For purposes of this section only, “voting stock” has the meaning given to it in Section 203 of the DGCL.
Under certain circumstances, this provision will make it more difficult for a person who would be an “interested stockholder” to effect various business combinations with us for a three-year period. This provision may encourage companies interested in acquiring us to negotiate in advance with our Board because the stockholder approval requirement would be avoided if our Board approves either the business combination or the transaction which results in the stockholder becoming an interested stockholder. These provisions also may have the effect of preventing changes in our Board and may make it more difficult to accomplish transactions which stockholders may otherwise deem to be in their best interests. Our A&R Charter provides that the Investors, and any of their respective direct or indirect transferees and any group as to which such persons are a party, do not constitute “interested stockholders” for purposes of this provision.
Change in Fiscal Year
On October 12, 2021, in connection with the Closing and the A&R Bylaws, our Board approved to change the Company’s fiscal year from March 31 to December 31, effective immediately. This change was effectuated to remain consistent with the fiscal year end of Legacy Appgate, which has become the Company’s operating subsidiary.
Item 5.06 Change in Shell Company Status.
As a result of the Merger, the Company ceased to be a shell company. Reference is made to the disclosure in Items 1.01 and 2.01 of this Report, which is incorporated herein by reference.
Item 8.01 Other Events.
On October 12, 2021, the parties to the Merger Agreement issued a joint press release announcing, among other things, the completion of the Merger, a copy of which is furnished as Exhibit 99.1 hereto.
Item 9.01 Financial Statements and Exhibits.
| (a) | Financial statements of businesses acquired |
The audited consolidated financial statements of Legacy Appgate as of and for the years ended December 31, 2020 and 2019 are filed as Exhibit 99.2 hereto and are incorporated herein by reference.
The unaudited condensed consolidated financial statements of Legacy Appgate for the three and six months ended June 30, 2021 and 2020, and as of June 30, 2021 and December 31, 2020 are filed as Exhibit 99.3 hereto and are incorporated herein by reference.
(b) Pro forma financial information
The unaudited pro forma condensed combined financial information of the Company is filed as Exhibit 99.5 hereto and incorporated herein by reference.
(d) Exhibits
| | | | | Incorporated by Reference |
| Exhibit Number | | Description | | Form | | Exhibit | | Filing
Date |
| 2.1† | | Agreement and Plan of Reorganization, dated as of February 8, 2021, by and among Newtown Lane, Merger Sub and Legacy Appgate | | 8-K | | 2.1 | | 02/09/2021 |
| 3.1 | | Second Amended and Restated Certificate of Incorporation | | | | | | |
| 3.2 | | Amended and Restated Bylaws | | | | | | |
| 10.1 | | Registration Rights Agreement, dated as of October 12, 2021 by and among Newtown Lane, SIS Holdings, Ironbound and, solely with respect to Section 3.1 thereof, Medina Capital Fund II – SIS Holdco, LP | | | | | | |
| 10.2 | | Support Agreement, dated as of February 8, 2021, by and among Newtown Lane, Legacy Appgate and SIS Holdings LP | | 8-K | | 10.1 | | 02/09/2021 |
| 10.3 | | Support Agreement, dated as of February 8, 2021, by and among Newtown Lane, Legacy Appgate and Ironbound Partners Fund, LLC | | 8-K | | 10.2 | | 02/09/2021 |
| 10.4 | | Lock-Up Agreement, dated as of October 12, 2021, by and among Newtown Lane, SIS Holdings and Ironbound | | | | | | |
| 10.5 | | Note Purchase Agreement, dated as of February 8, 2021, by and among Legacy Appgate and the lenders named on the Schedule of Lenders attached thereto | | | | | | |
| 10.6 | | Note Issuance Agreement, dated as of February 8, 2021, by and among Legacy Appgate, the Guarantors and Magnetar | | | | | | |
| 10.7 | | Supplemental Agreement, dated as of October 12, 2021, by and between Newtown Lane, Legacy Appgate and Magnetar Financial, LLC as representative of the Holders | | | | | | |
| 10.8 | | Registration Rights Agreement, dated as of February 8, 2021, by and among Legacy Appgate and the investors named therein | | | | | | |
| 10.9 | | Form of Director and Officer Indemnification Agreement | | | | | | |
| 10.10† | | Securities Purchase Agreement, dated as of December 17, 2020, by and between Legacy Appgate and E-Discovery AcquireCo, LLC | | | | | | |
| 10.11# | | 2021 Incentive Compensation Plan | | | | | | |
| 10.12# | | Amended and Restated Employment Agreement dated October 12, 2021 among Legacy Appgate, the Company and Manuel D. Medina | | | | | | |
| 10.13# | | Employment Agreement dated October 12, 2021 between the Company and Barry Field | | | | | | |
| 10.14# | | Employment Agreement dated October 12, 2021 between the Company and Rene A. Rodriguez | | | | | | |
| 10.15# | | Employment Agreement dated October 12, 2021 between the Company and Jawahar Sivasankaran | | | | | | |
| 10.16# | | Employment Agreement dated October 12, 2021 between the Company and Jeremy M. Dale | | | | | | |
| 10.17# | | Employment Agreement dated October 7, 2019 between Legacy Appgate and Michael Aiello | | | | | | |
| 10.18# | | Separation Agreement and Release dated June 5, 2020 between Legacy Appgate and Michael Aiello | | | | | | |
| 16.1 | | Letter from Liggett & Webb P.A. as to the change in certifying accountant, dated as of October 15, 2021 | | | | | | |
| 21.1 | | Subsidiaries of the Company | | | | | | |
| 99.1 | | Press release dated October 12, 2021 | | | | | | |
| 99.2 | | Audited consolidated financial statements of Legacy Appgate as of and for the years ended December 31, 2020 and 2019 | | | | | | |
| 99.3 | | Unaudited condensed consolidated financial statements of Legacy Appgate for the three and six months ended June 30, 2021 and 2020, and as of June 30, 2021 and December 31, 2020 | | | | | | |
| 99.4 | | Legacy Appgate’s Management’s Discussion and Analysis of Financial Condition and Results of Operation for the three and six months periods ended June 30, 2021 and 2020 and the years ended December 31, 2020 and 2019 | | | | | | |
| 99.5 | | Unaudited pro forma condensed combined financial information of the Company | | | | | | |
| 104 | | Cover Page Interactive Data File | | | | | | |
| # | Indicates management contract or compensatory plan or arrangement. |
| † | Certain of the exhibits and schedules to this Exhibit have been omitted in accordance with Regulation S-K Item 601(a)(5). The Company agrees to furnish a copy of all omitted exhibits and schedules to the SEC upon its request. |
SIGNATURES
Pursuant to the requirements of the Securities Exchange Act of 1934, the registrant has duly caused this report to be signed on its behalf by the undersigned hereunto duly authorized.
| Dated: October 15, 2021 | Appgate, Inc. |
| | | |
| | By: | /s/ Barry Field |
| | | Barry Field |
| | | Chief Executive Officer |
86


