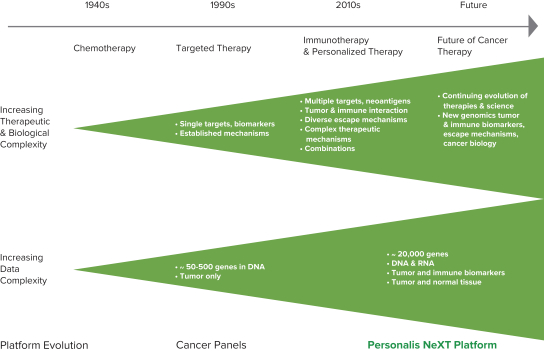
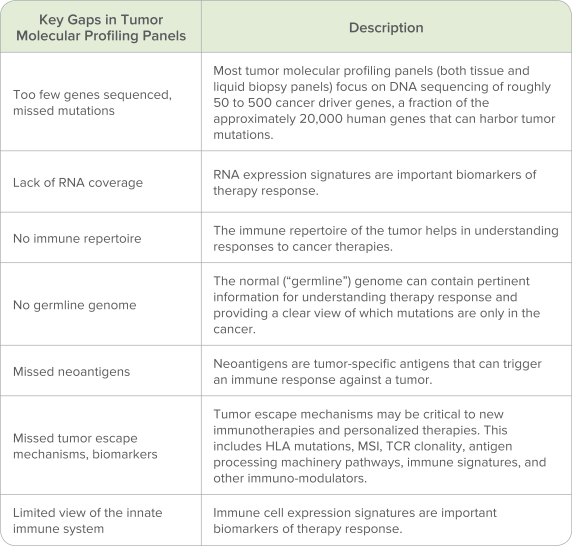
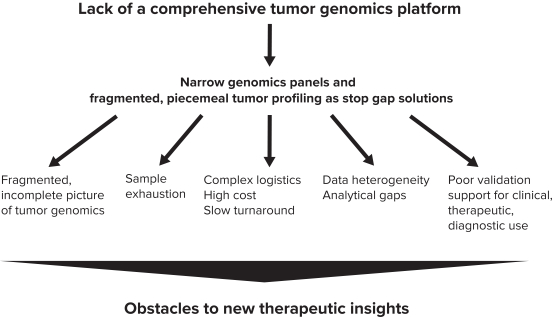
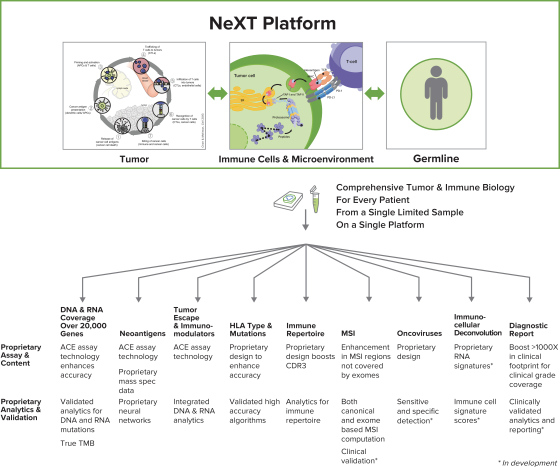
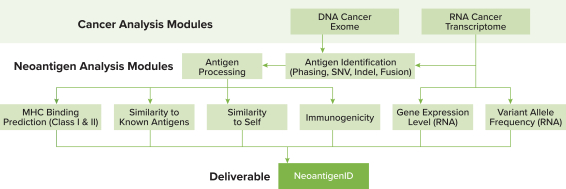
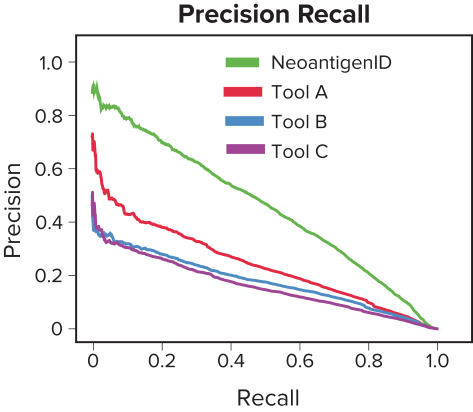
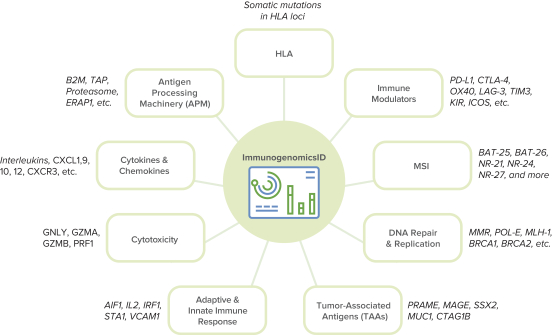
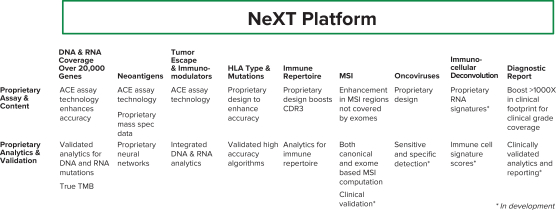
Our internal information technology systems, or those of our third-party vendors, contractors, or consultants, may fail or suffer security breaches, loss or leakage of data, and other disruptions, which could result in a material disruption of our services, compromise sensitive information related to our business, or prevent us from accessing critical information, potentially exposing us to liability or otherwise adversely affecting our business.
We are increasingly dependent upon information technology systems, infrastructure, and data to operate our business. In the ordinary course of business, we collect, store, and transmit confidential information (including but not limited to intellectual property, proprietary business information, and personal information). It is critical that we do so in a secure manner to maintain the confidentiality and integrity of such confidential information. We also have outsourced elements of our operations to third parties, and as a result we manage a number of third-party vendors and other contractors and consultants who have access to our confidential information.
Despite the implementation of security measures, given the size and complexity of our internal information technology systems and those of our third-party vendors and other contractors and consultants, and the increasing amounts of confidential information that they maintain, our such information technology systems are potentially vulnerable to breakdown or other damage or interruption from service interruptions, system malfunction, natural disasters, terrorism, war, and telecommunication and electrical failures, as well as security breaches from inadvertent or intentional actions by our employees, third-party vendors, contractors, consultants, business partners, and/or other third parties, or from cyber-attacks by malicious third parties (including the deployment of harmful malware, ransomware,denial-of-service attacks, social engineering, and other means to affect service reliability and threaten the confidentiality, integrity, and availability of information), which may compromise our system infrastructure, or that of our third-party vendors and other contractors and consultants, or lead to data leakage. The risk of a security breach or disruption, particularly through cyber-attacks or cyber intrusion, including by computer hackers, foreign governments, and cyber terrorists, has generally increased as the number, intensity, and sophistication of attempted attacks and intrusions from around the world have increased. We may not be able to anticipate all types of security threats, and we may not be able to implement preventive measures effective against all such security threats. The techniques used by cyber criminals change frequently, may not be recognized until launched, and can originate from a wide variety of sources, including outside groups such as external service providers, organized crime affiliates, terrorist organizations, or hostile foreign governments or agencies. To the extent that any disruption or security breach were to result in a loss of, or damage to, our data or applications, or those of our third-party vendors and other contractors and consultants, or inappropriate disclosure of confidential or proprietary information, we could incur liability and reputational damage and the further development and commercialization of our services could be delayed. The costs related to significant security breaches or disruptions could be material and exceed the limits of the cybersecurity insurance we maintain against such risks. If the information technology systems of our third-party vendors and other contractors and consultants become subject to disruptions or security breaches, we may have insufficient recourse against such third parties and we may have to expend significant resources to mitigate the impact of such an event, and to develop and implement protections to prevent future events of this nature from occurring.
While we have not experienced any such system failure, accident, or security breach to date, and believe that our data protection efforts and our investment in information technology reduce the likelihood of such incidents in the future, we cannot assure you that our data protection efforts and our investment in information technology will prevent significant breakdowns, data leakages, breaches in our systems, or those of our third-party vendors and other contractors and consultants, or other cyber incidents that could have a material adverse effect upon our reputation, business, operations, or financial condition. For example, if such an event were to occur and cause interruptions in our operations, or those of our third-party vendors and other contractors and consultants, it could result in a material disruption of our programs and the development of our services and technologies could be delayed. Furthermore, significant disruptions of our internal information technology systems or those of our third-party vendors and other contractors and consultants, or security breaches could result in the loss, misappropriation, and/or unauthorized access, use, or disclosure of, or the prevention of access to, confidential information (including trade secrets or other intellectual property, proprietary business
20