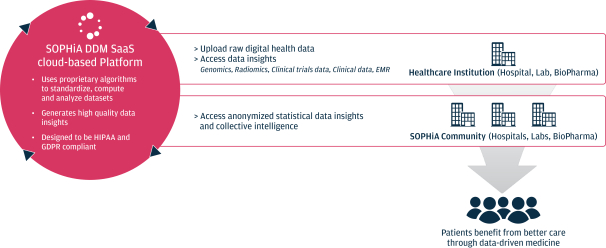
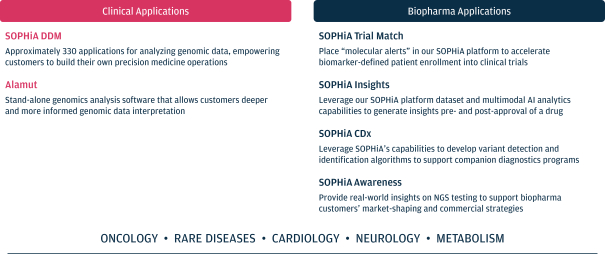
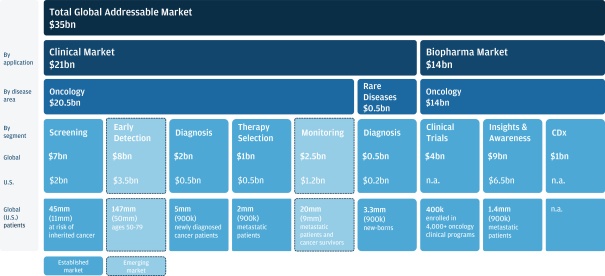
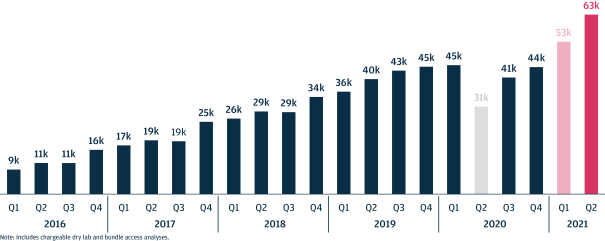
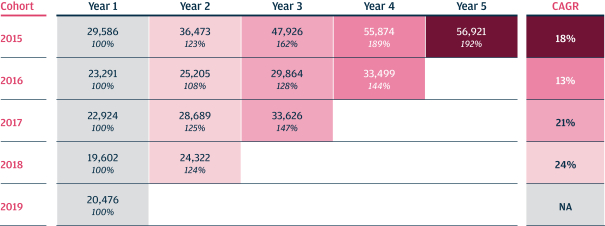
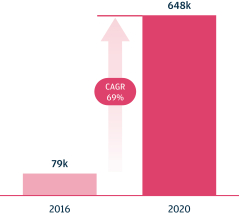
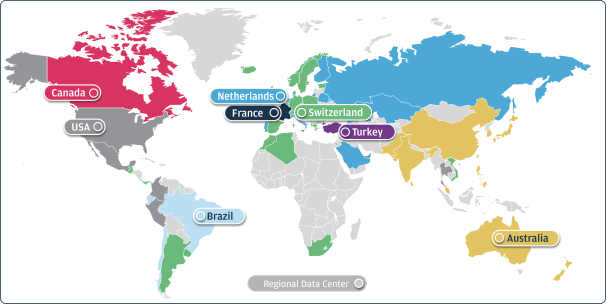
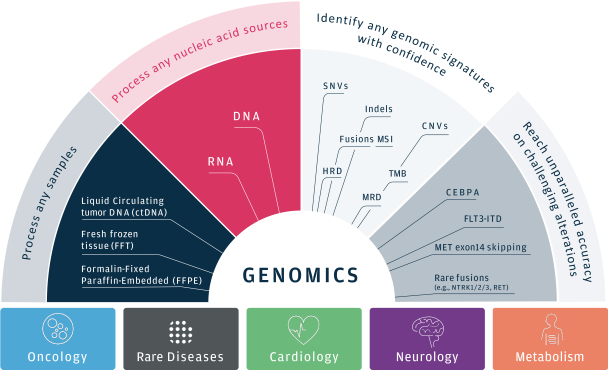
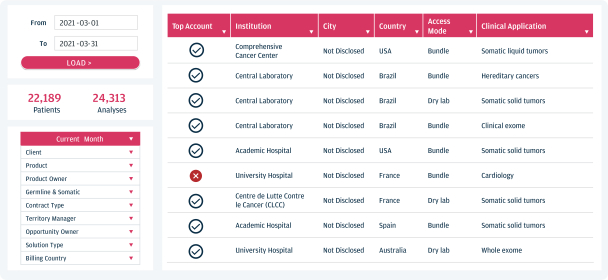
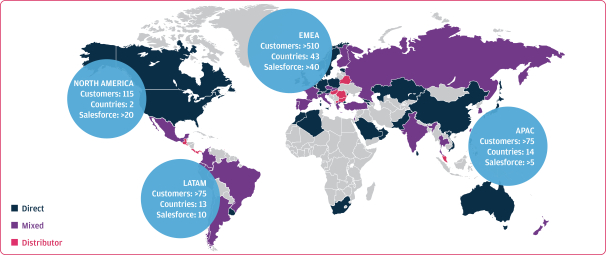
As we attain greater commercial success, our competitors are likely to develop technology, platforms, products and services that offer features and functionality similar to ours. Improvements in existing competitive technology, platforms, products and services or the introduction of new competitive technology, platforms, products and services may make it more difficult for us to compete for sales, particularly if competitors demonstrate better accuracy, reliability, convenience or effectiveness or price their platforms, products and services less expensively.
Our competitors may develop data analytics platforms and products or adopt and implement standards or technologies not compatible with our SOPHiA platform and our other services and products. This may inhibit our efforts to develop our platform, services and products in a technology-agnostic manner, which could narrow the addressable market for our SOPHiA platform and our other services and products, adversely impact their sales and market acceptance, and limit our revenue growth and potential profitability.
In addition, we operate in an ecosystem where we and our customers have multiple offerings and our own customers may become our competitors or may view us as potential competitors. This could disincentivize our customers or potential customers from adopting our offerings and sharing data with us, which would adversely impact sales and market acceptance and limit our revenue growth and potential profitability.
Security or data privacy breaches, other unauthorized or improper access, or denial of access (e.g., ransomware) could result in additional costs, loss of revenue, significant liabilities, harm to our brand and decreased use of our SOPHiA platform and related solutions, products or services.
In connection with various facets of our business, we collect and use a variety of personal data related to different data subjects (e.g., patients, users, agents, employees, representatives, etc.), such as identity data, contact data, profile data, technical data, health data, and genomic data. In addition, in connection with the performance of our contractual obligations and upon request from our customers and collaborators, we may access additional data, such as data available in the accounts of customers for support operations or data provided for research and development projects. Any failure to prevent or mitigate security incidents or improper access to, use, disclosure or other misappropriation of our data or customers’ personal data or the inability to rightfully access any such data could result in significant liability under state (e.g., state breach notification and privacy laws such as the California Consumer Privacy Act (“CCPA”)), federal (e.g., the Health Insurance Portability and Accountability Act of 1996, as amended by the Health Information Technology for Economic and Clinical Health Act (“HITECH”), collectively “HIPAA”) and international laws (e.g., the General Data Protection Regulation (“GDPR”)). Such an incident may also cause a material loss of revenue from the potential adverse impact to our reputation and brand, affect our ability to retain or attract new users and customers of our products and services and potentially disrupt our business.
Unauthorized disclosure of sensitive or confidential patient or employee data, including personally identifiable information, whether through a breach of computer systems, systems failure, employee negligence, fraud or misappropriation, or otherwise, or unauthorized access to or through our information systems and networks, whether by our employees or third parties, could result in negative publicity, legal liability and damage to our reputation. Unauthorized disclosure of personally identifiable information could also expose us to sanctions for violations of data privacy laws and regulations around the world. To the extent that any disruption or security incident resulted in a loss of or damage to our data or applications, or inappropriate disclosure of confidential or proprietary information, we could incur liability and the further development of our products or services could be delayed.
As we become more dependent on information technologies, to conduct our operations, cyber incidents, including deliberate attacks and attempts to gain unauthorized access to computer systems and networks, may increase in frequency and sophistication. These threats pose a risk to the security of our systems and networks, the confidentiality and the availability and integrity of our data, and these risks apply both to us (including via
34